Introduction
In recent years, digital assets such as Bitcoin, Ethereum, and other cryptocurrencies have become an integral part of corporate finances. From corporate treasuries diversifying into crypto to start-ups paying salaries in stablecoins, the adoption trend has accelerated, and along with it, the responsibility to keep these assets secure. Unlike traditional financial systems, crypto networks are decentralized and irreversible: any loss or theft of private keys means a permanent loss of funds, with no central authority to reverse fraudulent transactions, making expert-led blockchain security services a prudent baseline for teams with material exposure. If you’re formalizing a security program, consider our enterprise-grade blockchain security services for comprehensive coverage.
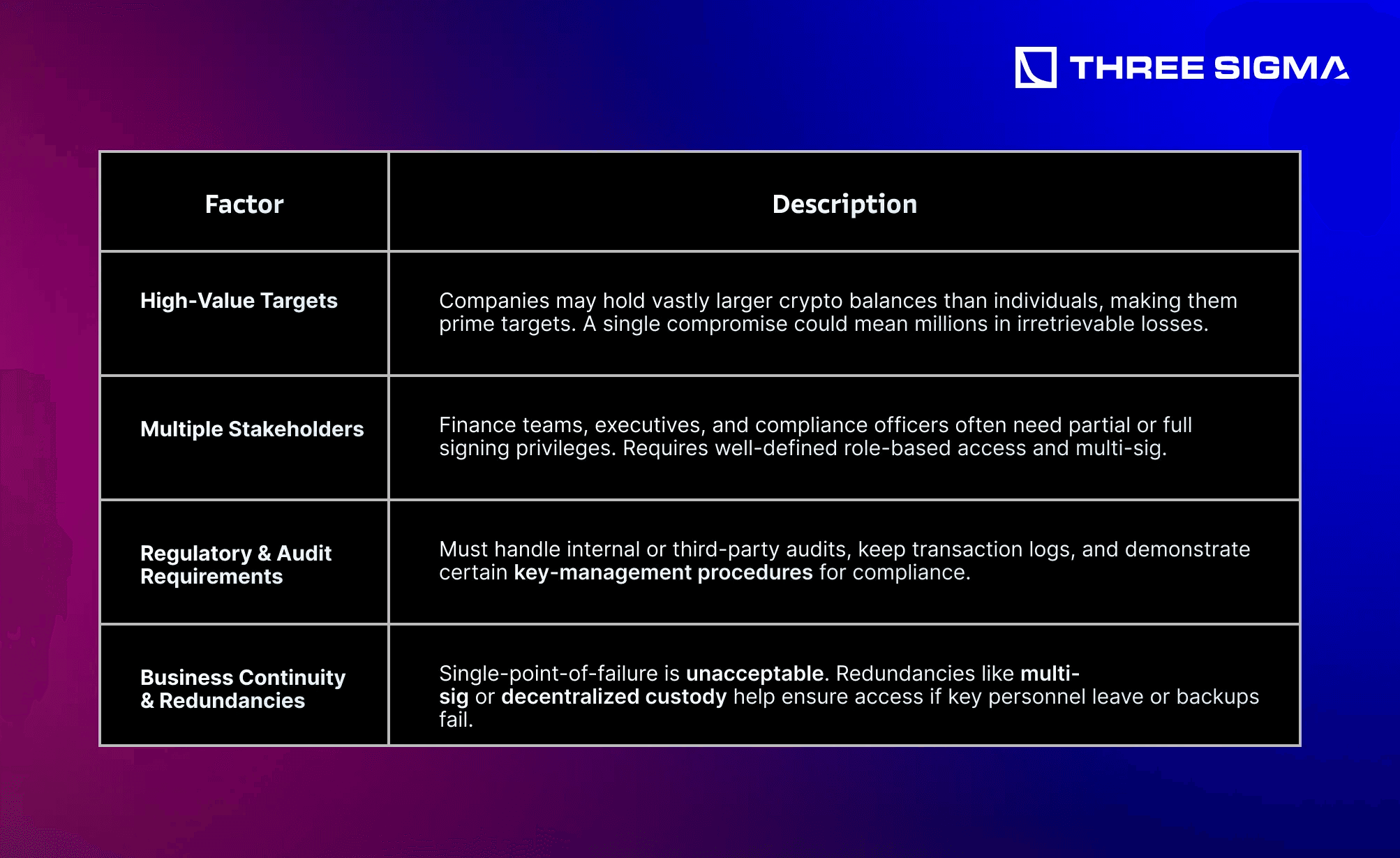
For companies, this raises the stakes significantly compared to personal wallets. Multi-million-dollar (or even billion-dollar) sums can be at risk, which makes robust operational security (OpSec) not merely advisable, but mission-critical. A single successful attack, whether through compromised wallet backups, phishing of an employee, or a sophisticated supply chain exploit, can lead to devastating financial and reputational damage.
In this guide, we’ll explore enterprise-level operational security, how to store private keys, safeguard corporate wallets, and minimize the risk of both external and internal threats. While the best practices mirror many fundamentals applied by individual crypto holders, corporate environments face special considerations:
- Shared responsibilities: Multiple employees and executives often need controlled access.
- Regulatory overhead: Compliance with KYC/AML laws, tax reporting, and possibly additional audits.
- Complex usage patterns: Staking, payroll, and frequent transactions that require more frequent signing events.
Ultimately, a company’s OpSec posture is only as strong as its weakest link, be it a single compromised employee credential or a hot wallet used without proper safeguards. By understanding the nuances of corporate wallet security and private key management, enterprises can reduce the chance of catastrophic losses and ensure that crypto assets remain firmly under organizational control.

1. Private Key Management & Corporate Wallet Security
When an individual holds cryptocurrency, the basics of “not your keys, not your coins” generally suffice: keep private keys safe, ideally on a hardware wallet or secure offline storage. In a corporate setting, however, private key management becomes more complex, you have to coordinate multiple team members, maintain continuous availability for business operations, and satisfy both security and compliance mandates.
Below are core considerations for corporate wallet security—drawn from operational security research, real-world incidents, and widely cited best practices.

1.1 Why Corporate Private Key Management Demands Extra Rigor
Key Point:
“Your level of OpSec usually depends on your threat model.” For companies, that threat model is broader—encompassing not only external hacking and phishing but also insider threats and social engineering targeting employees or executives.
Real-World Example: Moby Trade Private Key Leak
On January 8th, 2025, Moby Trade suffered a private key leak, resulting in the theft of over $1 million in crypto assets. Attackers used compromised admin keys to upgrade existing proxy contracts, draining vaults that held ETH, BTC, and USDC.
- Key Loss: The attacker gained access to Moby Trade’s administrative private key—turning a small misstep into a major exploit.
- Proxy Contract Upgrades: Using the stolen key, the attacker performed malicious upgrades on Moby’s vault contracts, siphoning BTC, ETH, and stablecoins.
- Partial Whitehat Rescue: A whitehat group (SEAL911) noticed the attacker made a fatal mistake - they left an unprotected upgradeToAndCall function in their wake, salvaging ~$1.47 million in USDC from further theft.
Takeaway: Even if the underlying smart contracts are secure, a single stolen or leaked key can lead to catastrophic losses—highlighting how crucial private key hygiene and redundancy are in corporate setups.
1.2 Cold Wallets as the Gold Standard (But Not a Panacea)
Cold wallets (hardware or paper-based) often stand out as one of the safest methods for storing large sums of cryptocurrency offline. However, corporate usage adds extra layers of complexity:
- Physical Security Whether a hardware wallet (e.g., Trezor, Ledger, Coldcard, or Lattice) or a paper wallet, physical storage is critical. Devices and seed phrases often need to be kept in secure locations—for example, in safe-deposit boxes or fireproof safes, possibly across multiple geographic regions.
- Multi-Signature Configurations Relying on a single-signature cold wallet can be risky in a corporate environment. Multi-sig (e.g., 2-of-3, 3-of-5) spreads control across trusted parties, minimizing the impact if one device is compromised or an individual key holder is unavailable.
- Supply Chain & Firmware Attacks Purchase hardware wallets directly from the manufacturer or authorized distributors, and regularly verify the firmware integrity. Attackers can tamper with devices in transit or distribute fake look-alikes.

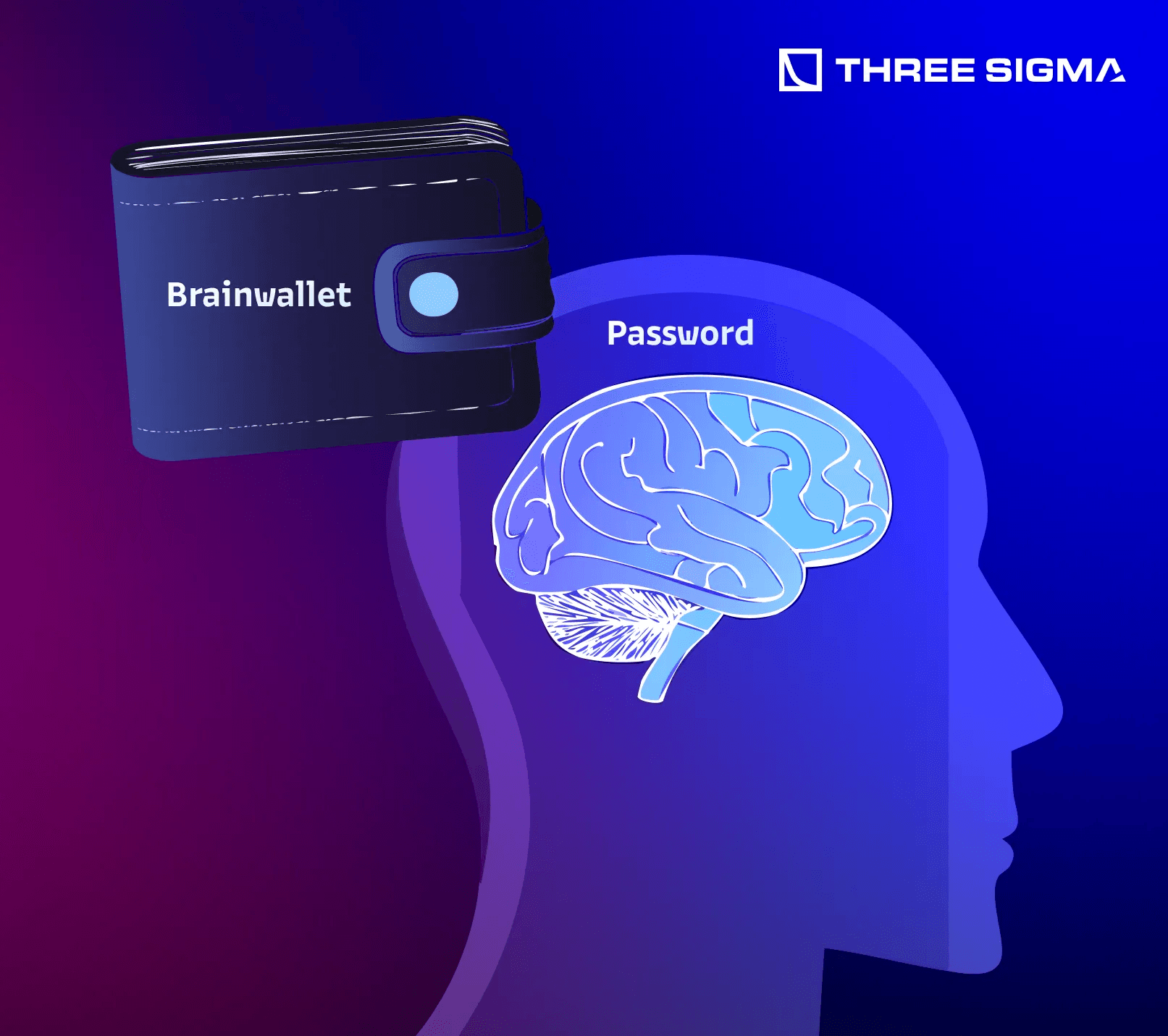
1.3 Brain Wallets: Why Corporations Should Avoid Them
A brain wallet derives its private key from a memorized passphrase. Though this might seem attractive—no physical device to protect—brain wallets are highly vulnerable to brute force attacks and are notoriously insecure.
- Corporations Are Prime Targets Bots monitor blockchains looking for weak passphrase-based wallets. A large incoming transaction is quickly seized if the key is guessable.
- Irretrievable if Forgotten If an employee with the passphrase leaves or forgets a detail, the funds can be lost forever.
Conclusion:
Brain wallets are generally considered too risky for serious corporate use. They rely heavily on human memory and unpredictable human behavior.
1.4 Paper (or Metal) Wallets & Offline Generation
Paper or metal wallets can be used for long-term, rarely accessed crypto storage, but frequent transactions and multi-user access are more complex.
1 - Offline Generation
- Always generate seed phrases on a verifiably air-gapped device using open-source scripts or hardware RNG.
- Confirm you’re using robust entropy (atmospheric noise, tested RNG, or well-known cryptographic libraries).
2 - Storage & Redundancy
- Maintain duplicates in separate secure facilities (bank vaults, private safes).
- If one backup is destroyed or compromised, the other remains valid.
3 - Encryption & Steganography
- Optionally encrypt or embed the seed (steganography) for additional obscurity.
- Tools like Portable Secret or GPG-based solutions can help.
4 - Operational Friction
- Paper or metal wallets are best for deep cold storage. For daily transactions, consider a hardware or multi-sig hot wallet with limited funds.

1.5 Recommended Approach: Layered Security with Multi-Sig
Enterprises often require multiple signers (finance, executives, compliance) and must ensure no single user can unilaterally move large sums. A layered approach combining multi-sig, offline backups, and monitored operational wallets is ideal.
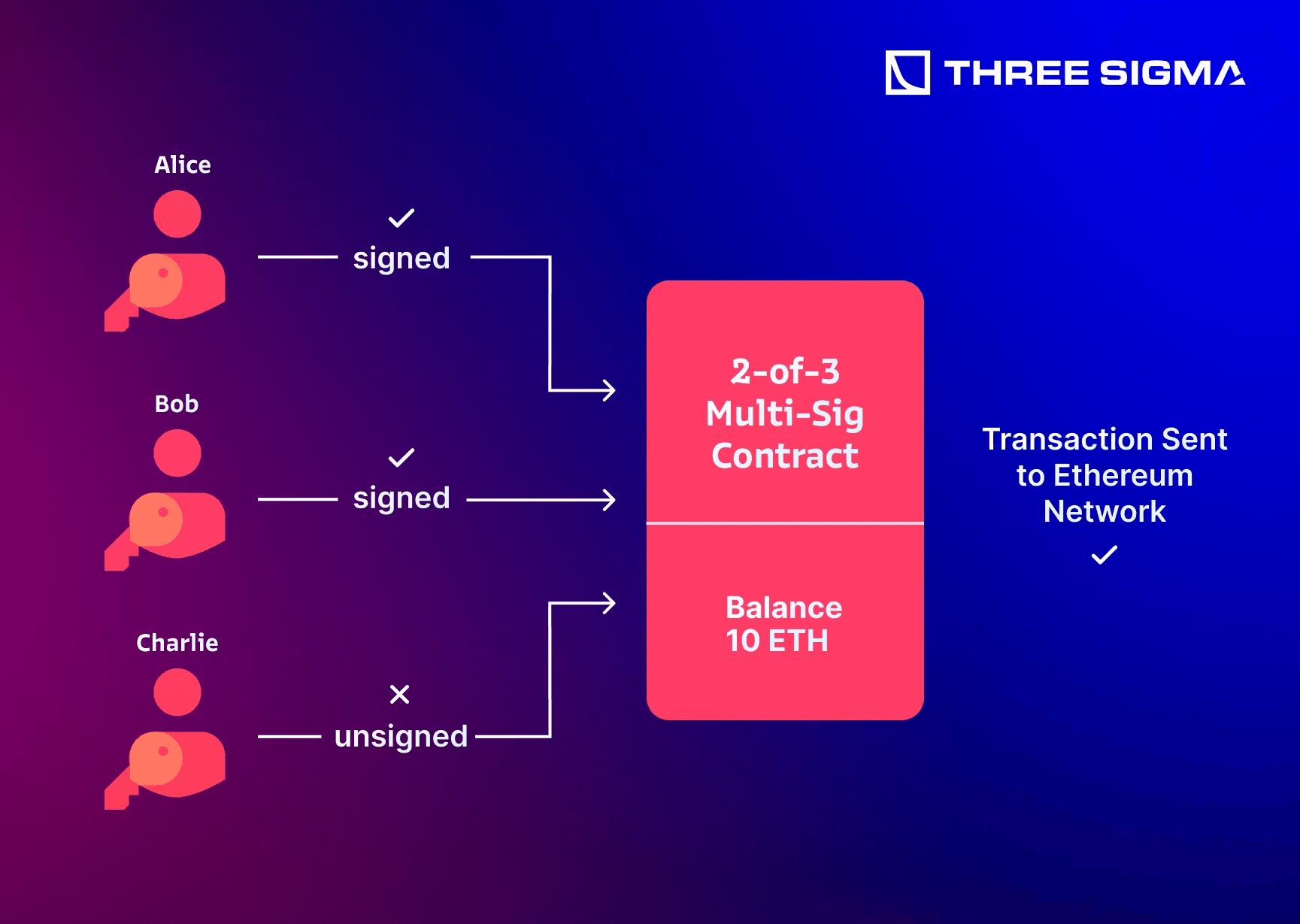
Below is a layered plan integrating advanced best practices from community resources:
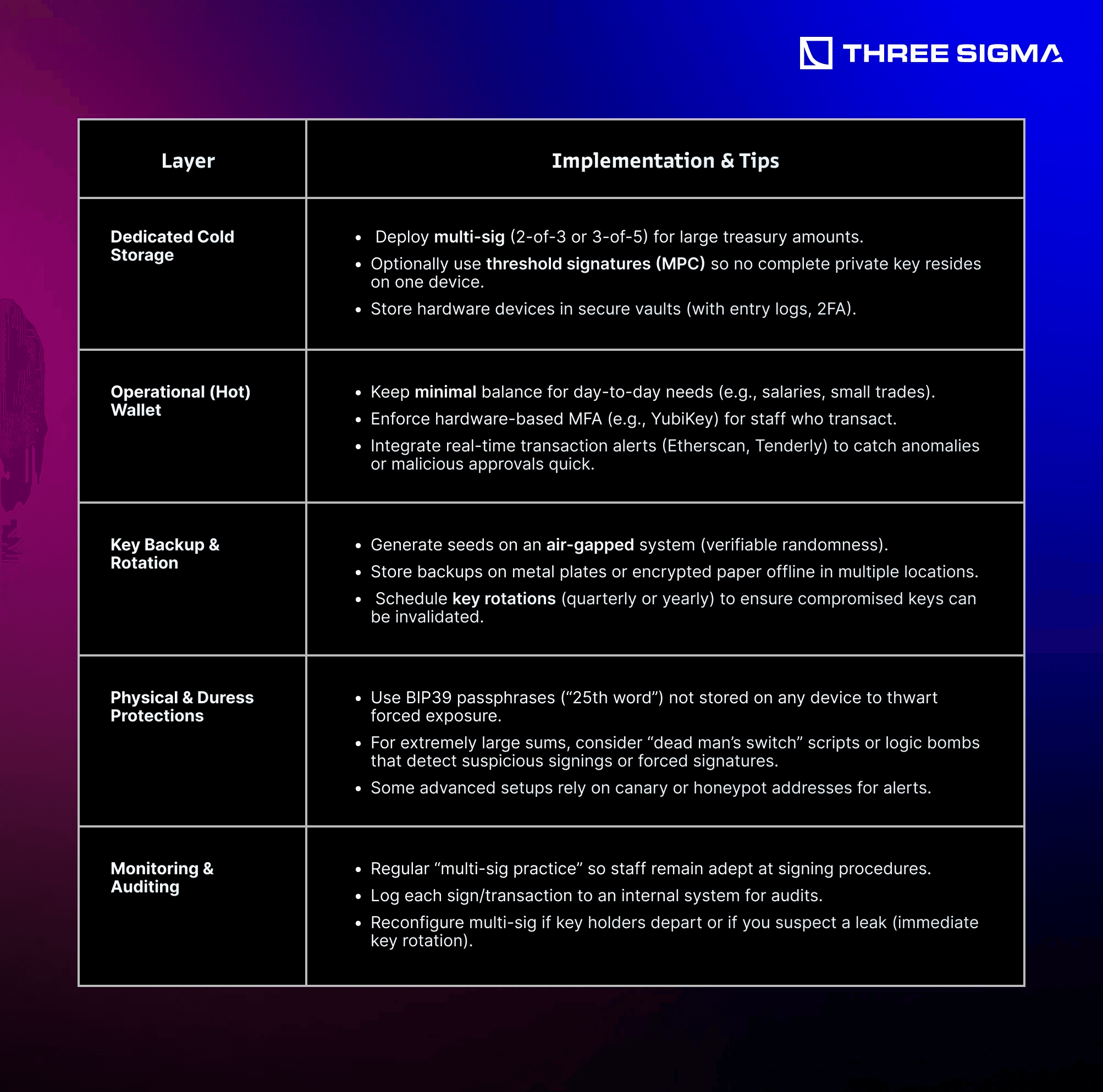
Additional Tech Tips:
- Vet multi-sig solutions (e.g., Gnosis Safe) following official guides (OpenZeppelin resources).
Physical Attacks
Large holdings invite coercion or kidnapping. Not all threats are digital. The co-founder of Ledger was reportedly kidnapped and tortured—losing a finger—until some ransom was paid. High-profile crypto owners have been robbed in home invasions. Maintaining a low public profile about holdings and employing passphrase-protected wallets can help mitigate these horrific scenarios.
The Physical Bitcoin Attacks repository tracks over 200 such incidents globally, with kidnappings, forced signings, and violence all on the rise each year. This underscores that physical security is every bit as vital as the digital.
1.6 Custodial vs. Non-Custodial Solutions
The table below compares custodial vs. non-custodial approaches for enterprises:
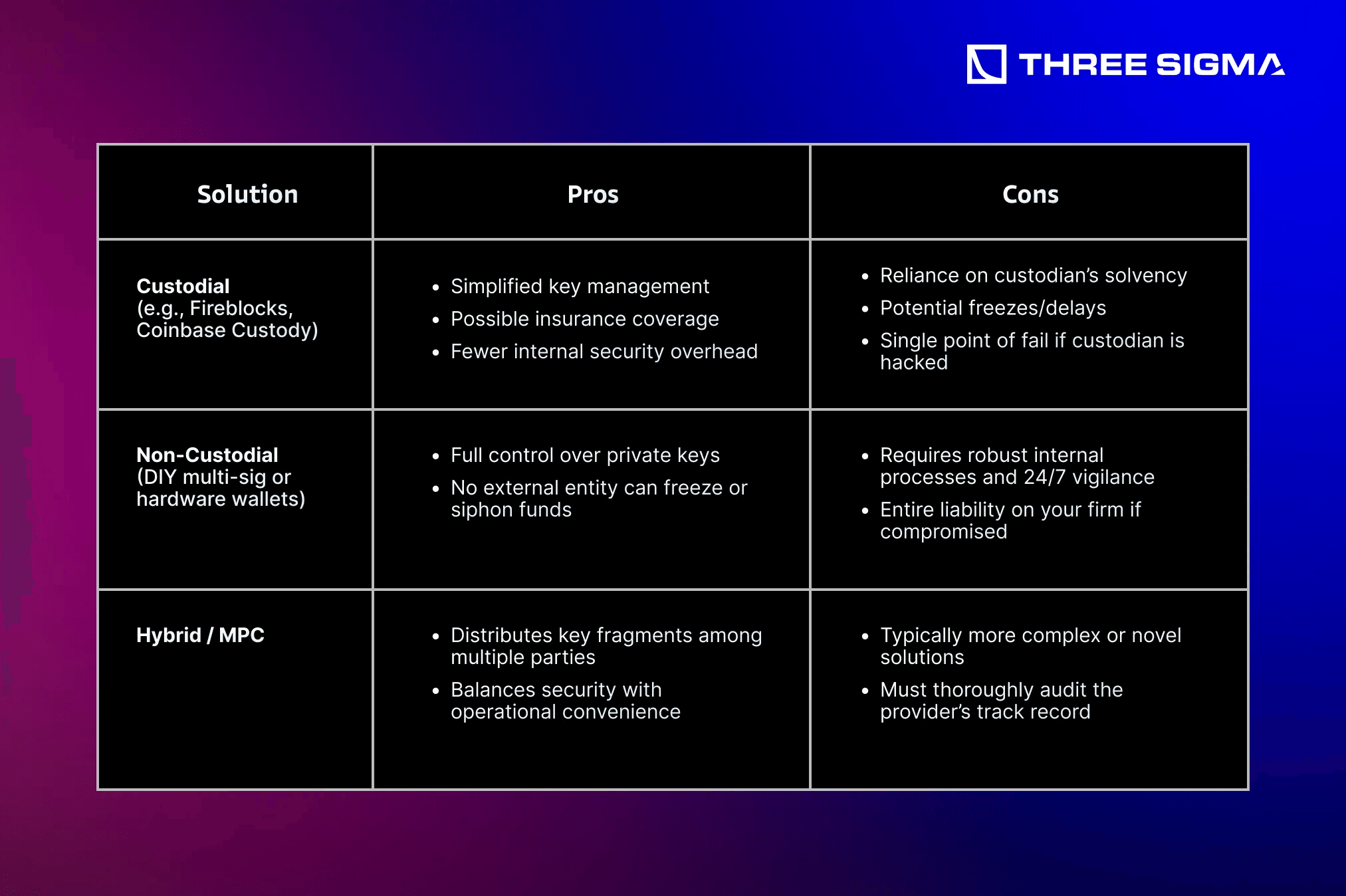
Tip: For large treasuries without internal security expertise, a partially custodial or MPC-based solution can be safer—provided the custodian has proven audits and a strong track record.
1.7 Concluding Thoughts on Private Key Management
Protecting corporate crypto holdings demands a comprehensive strategy that addresses both digital and physical threats. As illustrated by Moby Trade’s key leak and the rising trend of physical robberies and kidnappings, one compromised key can topple even the best-engineered system.
- Use Multi-Sig or advanced threshold signatures for treasury sums.
- Generate & Store seeds on offline systems, verifying entropy.
- Restrict Access with role-based controls—no single employee should drain the treasury.
- Continuously Audit backups, hardware wallets, and logs for suspicious activity.
- Plan for Coercion—deploy passphrases or “duress codes,” keep a low profile about your company’s holdings, and conduct staff security training on crisis scenarios.
Such a layered approach—spanning cold wallets, hardware security, multi-sig safeguards, and real-time monitoring—drastically reduces the chance of catastrophic loss and insider manipulation, enabling enterprises to confidently manage digital assets at scale.
2. Phishing & Social Engineering Awareness
Read our article for Users where we discussed Phishing Schemes.

3.1 Network Segmentation & Secure Infrastructure Design
Rather than a single perimeter, segmentation creates multiple layers or “zones” each with specific access rules. If an attacker breaches one zone, they have to defeat additional controls to reach more critical assets—limiting lateral movement and reducing the chances of a single exploit compromising all corporate funds.
3.1.1 Why Segment Your Network?
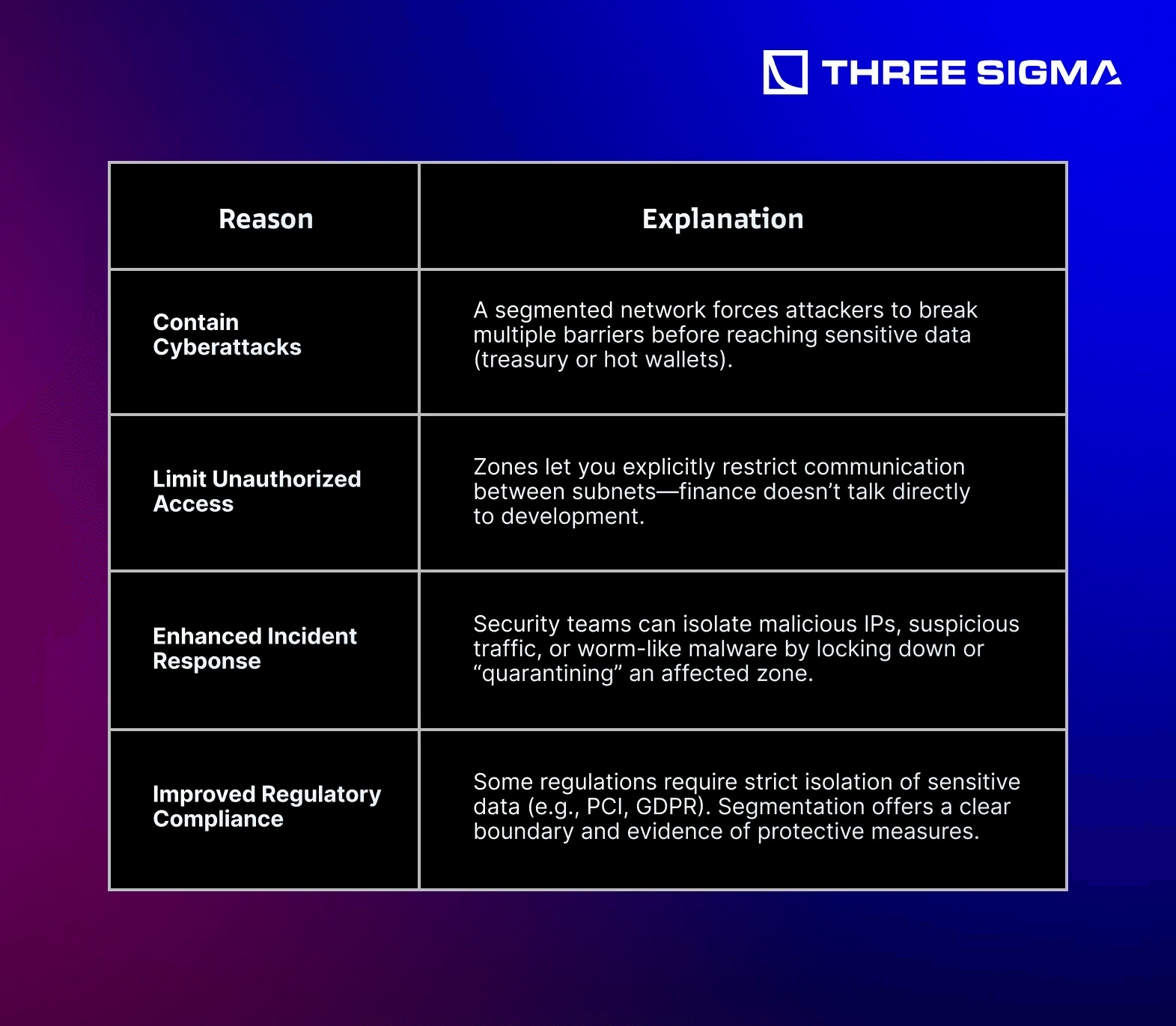
Analogy: Think of your corporate network like a house with multiple rooms and locked doors. A breach in one “room” shouldn’t grant an intruder free rein across the entire floor.
3.1.2 Implementation: Designing Logical Zones
Zones can be formed by IP ranges, subnets, or security groups based on risk and business function. For example:
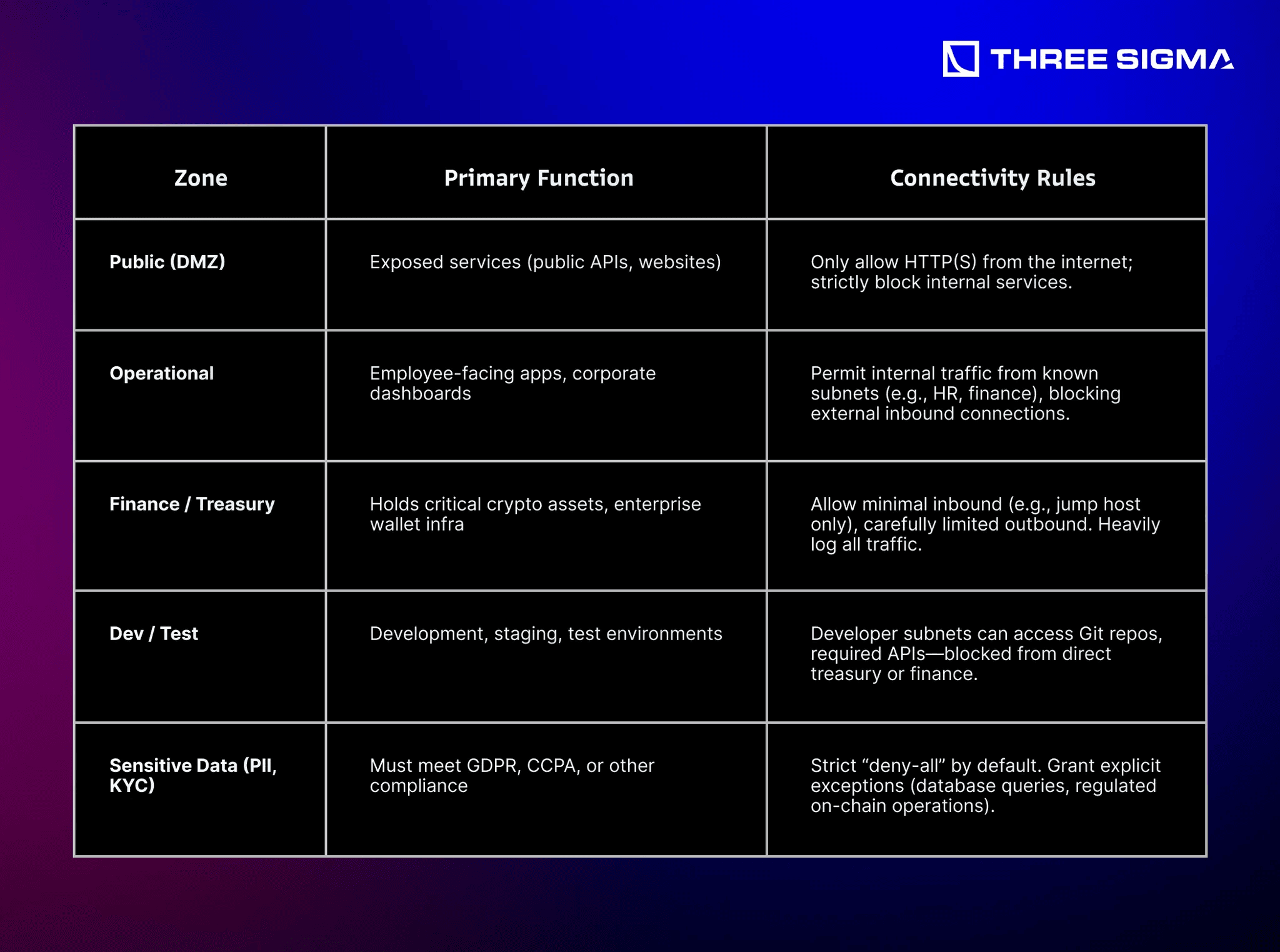
Technical: Use VLANs, subnets, or cloud security groups. Combine them with a robust firewall or NAC (Network Access Control) solution to define and enforce which ports/services can transit between zones.
Example: For large DeFi or trading firms, you might segment the “Hot Wallet Transaction Network” from the “Employee LAN,” ensuring that an internal phishing infection doesn’t directly pivot to signing wallet transactions.
3.1.3 Enterprise-Grade Firewalls & Access Controls
Network segmentation depends on robust firewalls or next-generation firewall appliances:
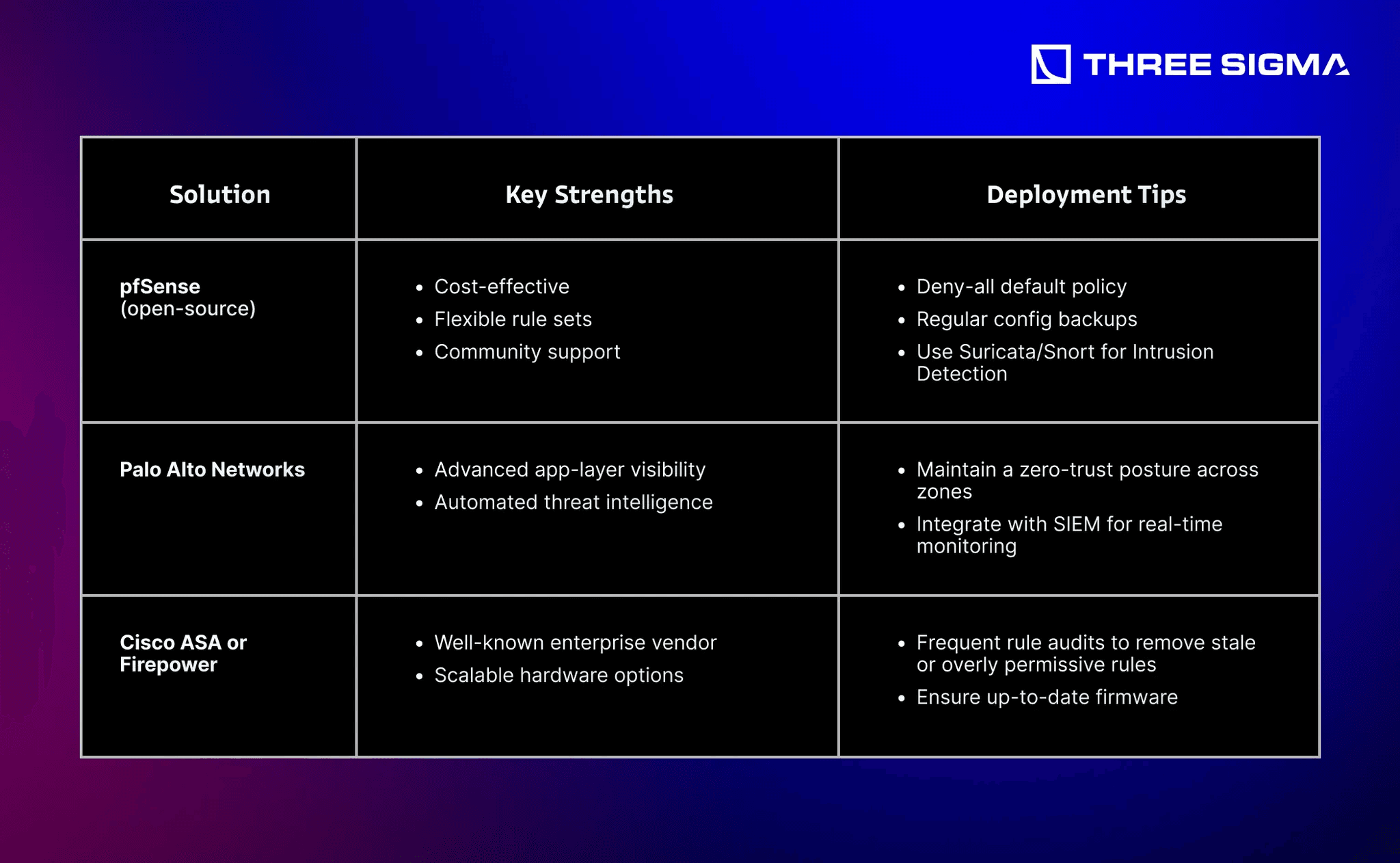
Access Control Lists (ACLs) define which services can flow across zone boundaries:
- Allow: Verified traffic (e.g., needed SSH or HTTPS)
- Block: Risky services, known malicious IPs, or unnecessary ports
Pro Tip: If suspicious traffic is detected (e.g., WannaCry-like worm or zero-day exploit), quickly adjust ACLs or push new firewall rules to isolate the compromised zone.
3.1.4 Minimizing Complexity vs. Microsegmentation
- Basic Segmentation: A small number of zones (3–5) drastically reduces the “blast radius” of an attack.
- Microsegmentation: Each application or service in its own zone, aligned with zero-trust. This level of granularity can be powerful but demands advanced tooling (SDN, NAC solutions, or dynamic policy management).
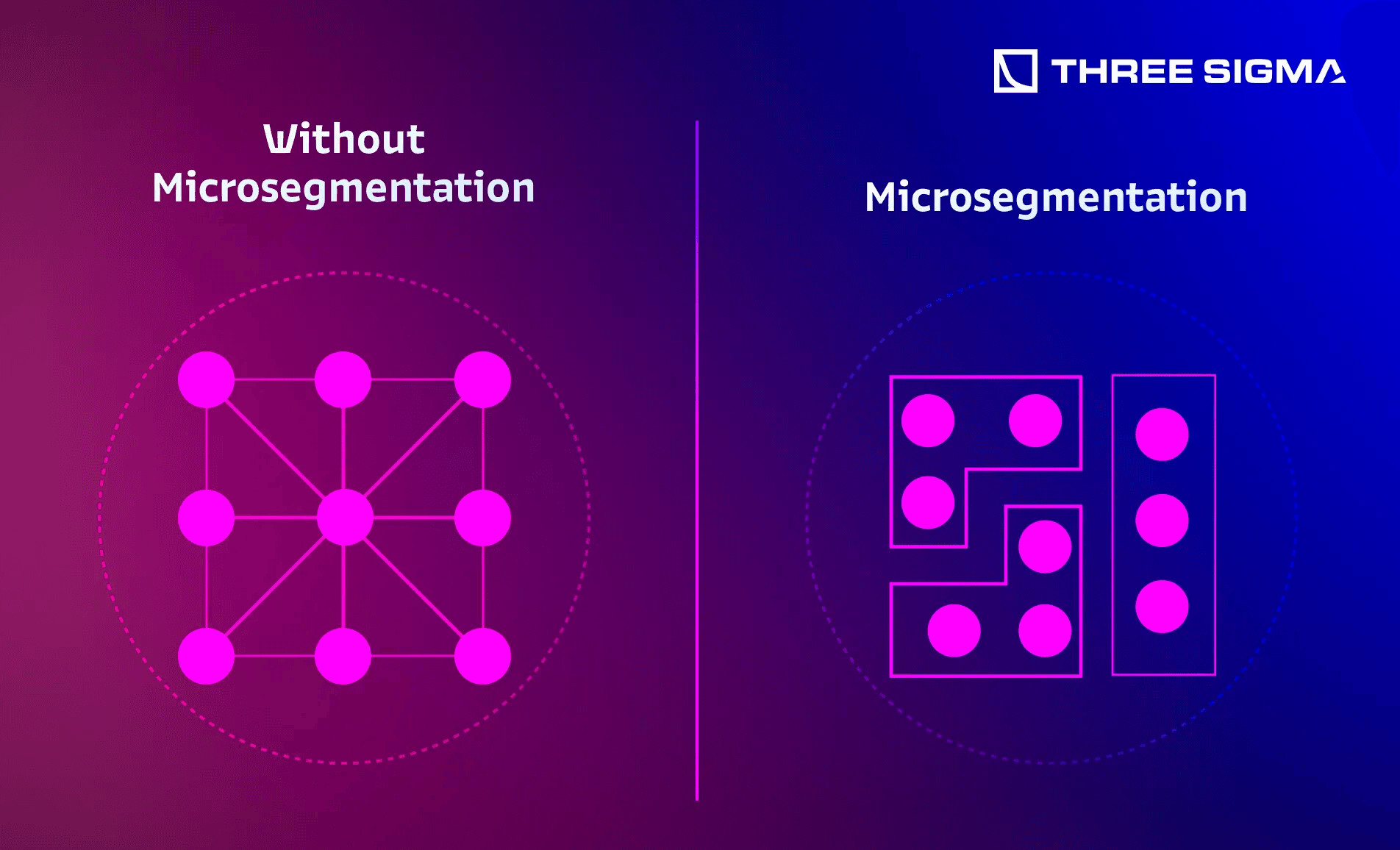
Takeaway: Start with a few well-defined zones (e.g., DMZ, operational, finance, dev) before ramping up to microsegmentation—excessive complexity can backfire if not managed properly.
3.2 Secure Device & Endpoint Management
Even with strong network segmentation, employee endpoints remain a top target—attackers often rely on phishing or malware that runs locally to pivot further. Enterprises should adopt advanced Endpoint Protection Platforms (EPP), Mobile Device Management (MDM), and virtualization for high-risk tasks.
3.2.1 Endpoint Protection Platforms (EPP) & Endpoint Detection and Response (EDR)
- Why It’s Critical: Malware and RAT (Remote Access Trojan) infections often start at the endpoint—employee laptops, finance team desktops, or developer machines. This was reportedly the root cause of the $1.4 Billion Bybit Hack, where a supposedly “safe” employee machine became infected.
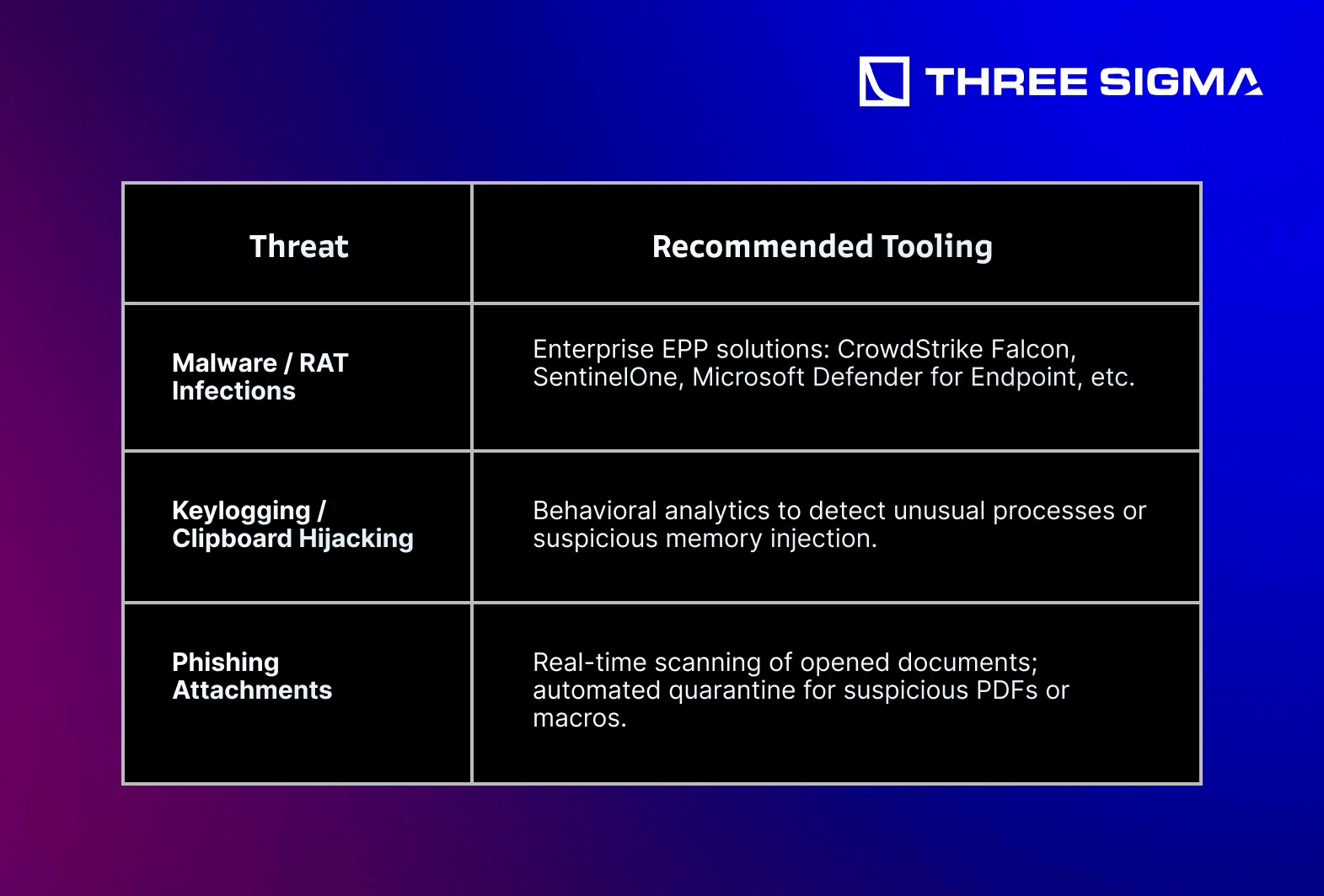
Example: Problem 1–10 references from OfficerCia's Crypto-OpSec-SelfGuard-RoadMap discuss RAT-based phishing. A robust EDR solution can identify unusual processes triggered by malicious PDF or DOC files, instantly isolating the affected endpoint.
3.2.2 Mobile Device Management (MDM)
Many employees use their personal smartphones for 2FA, wallet monitoring, or corporate communications. A compromised phone can become a direct vector for crypto theft.
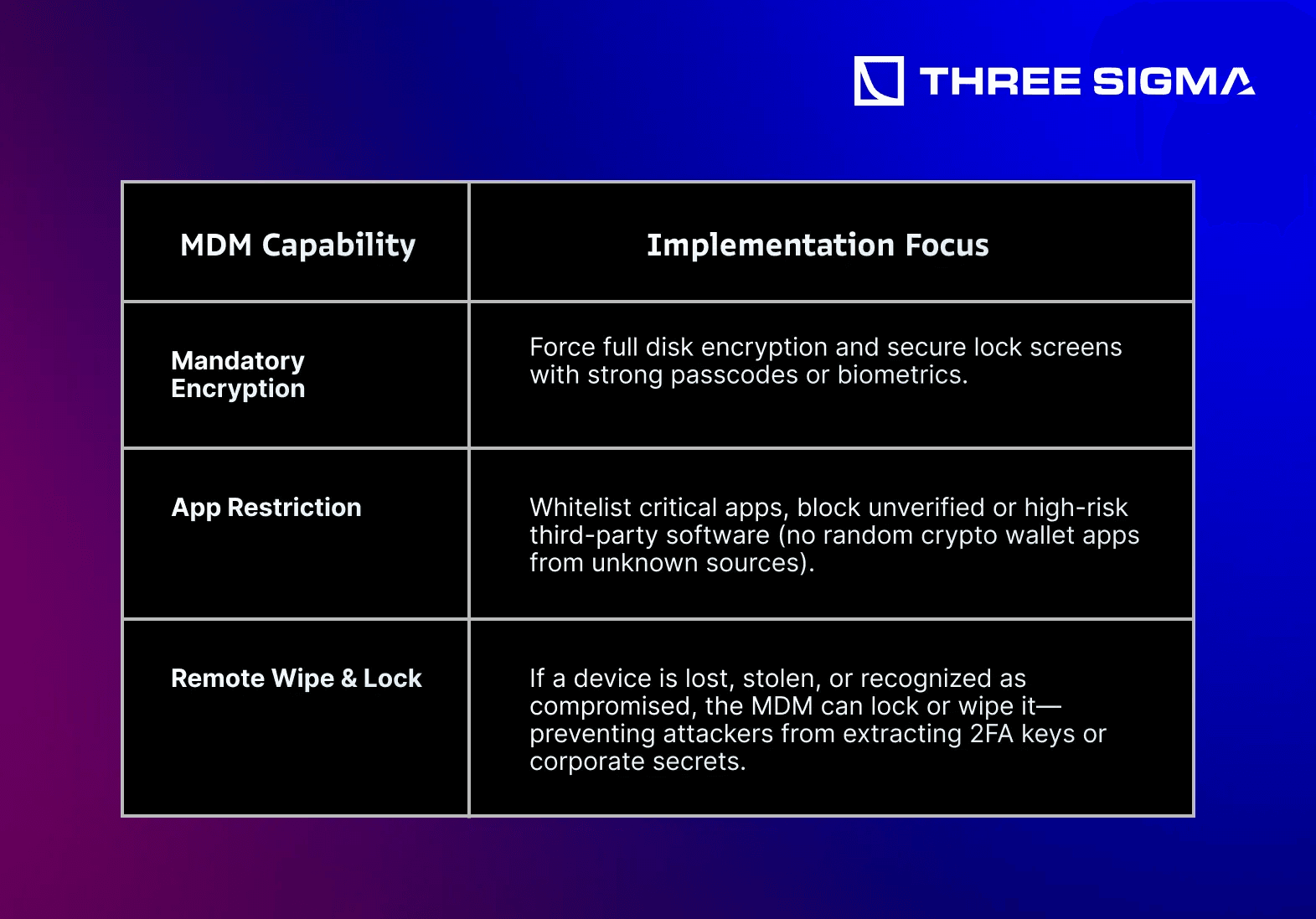
Reference: Problem 22 highlights the vulnerability of smartphones—especially if employees use them for sensitive tasks. MDM ensures consistent security policies across all devices.
3.2.3 Virtual Desktop Infrastructure (VDI)
VDI centralizes computing in a secure data center or cloud, so endpoints effectively become “thin clients.” This approach mitigates local malware risk and streamlines control of the corporate environment.
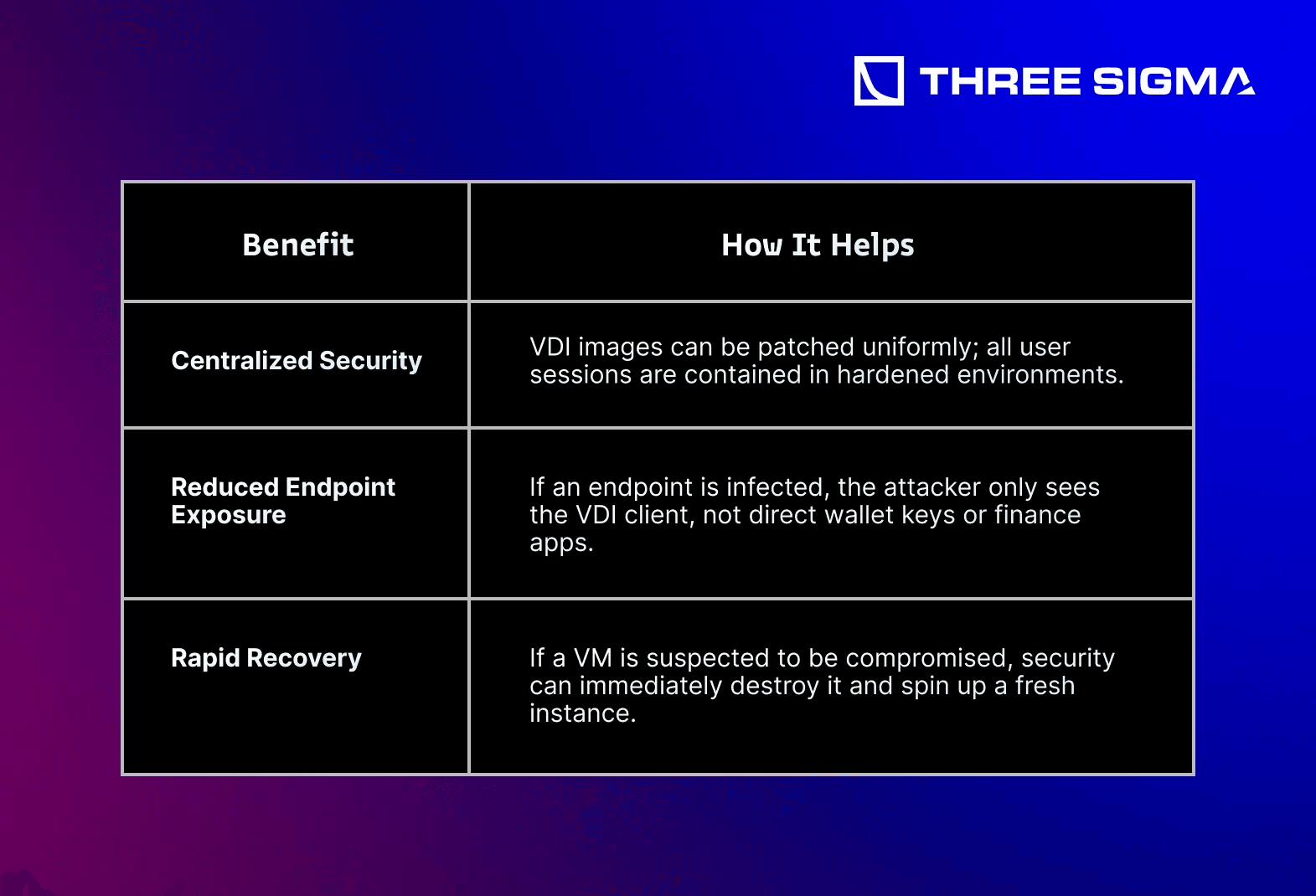
Tip: Solutions like AWS WorkSpaces, VMware Horizon, or Citrix create ephemeral, secure VMs for day-to-day crypto tasks—limiting local machine vulnerabilities.
3.3 Virtualization & Sandboxing Strategies
For advanced threat isolation, virtualization and sandboxing allow you to safely test or open suspicious files or quarantined email attachments.
Example: Problem 16 suggests always opening suspicious files in a “preview mode” or via a sandbox. This step prevented multiple RAT infections at a Web3 marketing agency.
3.3.2 Secure Containers & Docker Images
Many crypto companies use containerized microservices or host internal nodes in Docker. Hardening these containers is crucial:

Advanced: If using a container-based blockchain node, ensure the data directory is encrypted or protected by host-level ACLs.
3.3.3 Virtualization-Based Isolation (Qubes OS, AWS WorkSpaces)
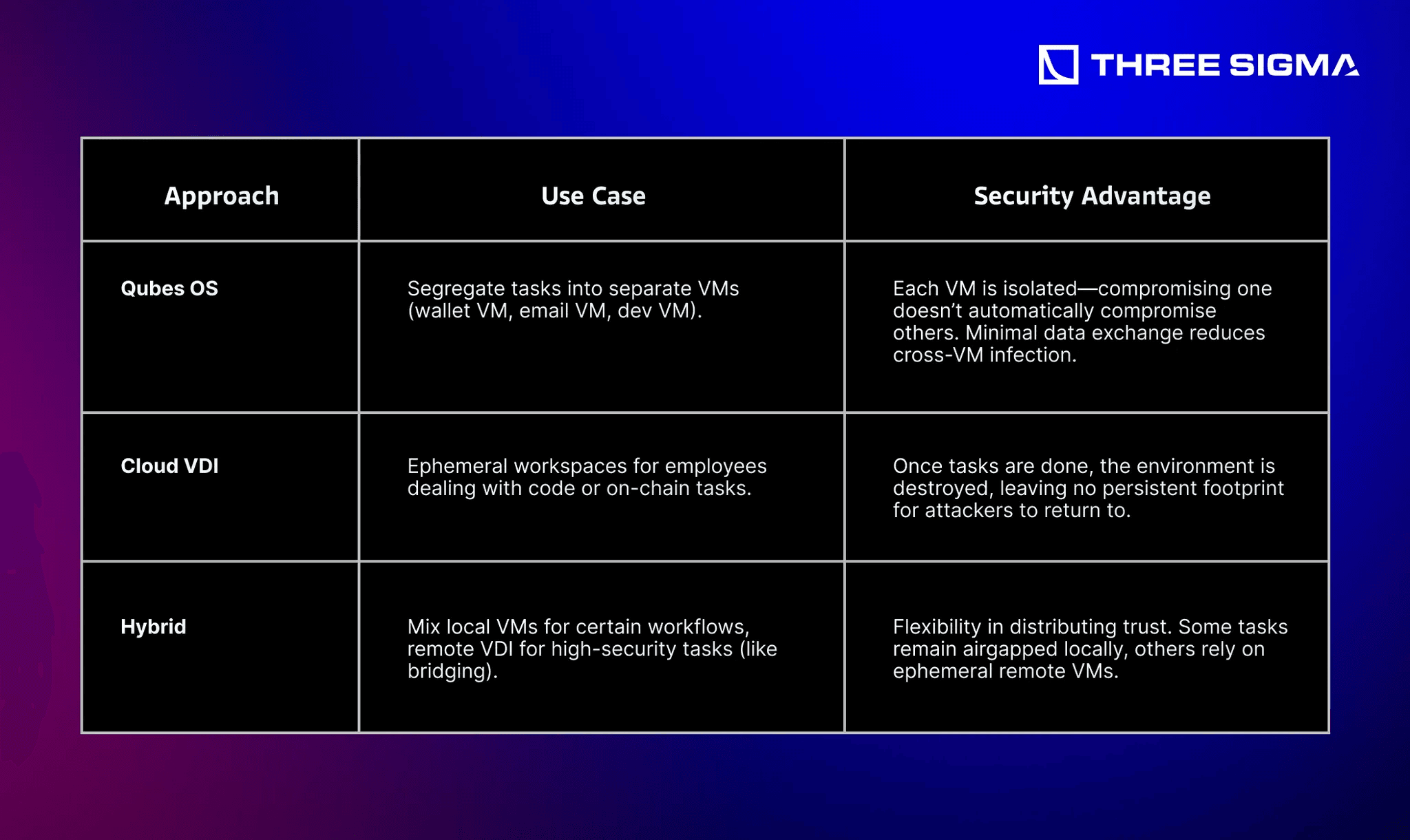
Reference: Problem 17 emphasizes that virtualization fosters a zero-trust posture—services remain strictly compartmentalized.
3.4 Hardware Security & USB Threats
Network segmentation is powerful, but a single compromised laptop or malicious USB device can bypass the best ACLs. Physical device audits and strict USB policies become essential.

3.4.1 Physical Device Audits & Tamper-Evident Hardware
Attackers can physically swap devices, add keyloggers, or tamper with internal components.
Recommendations:
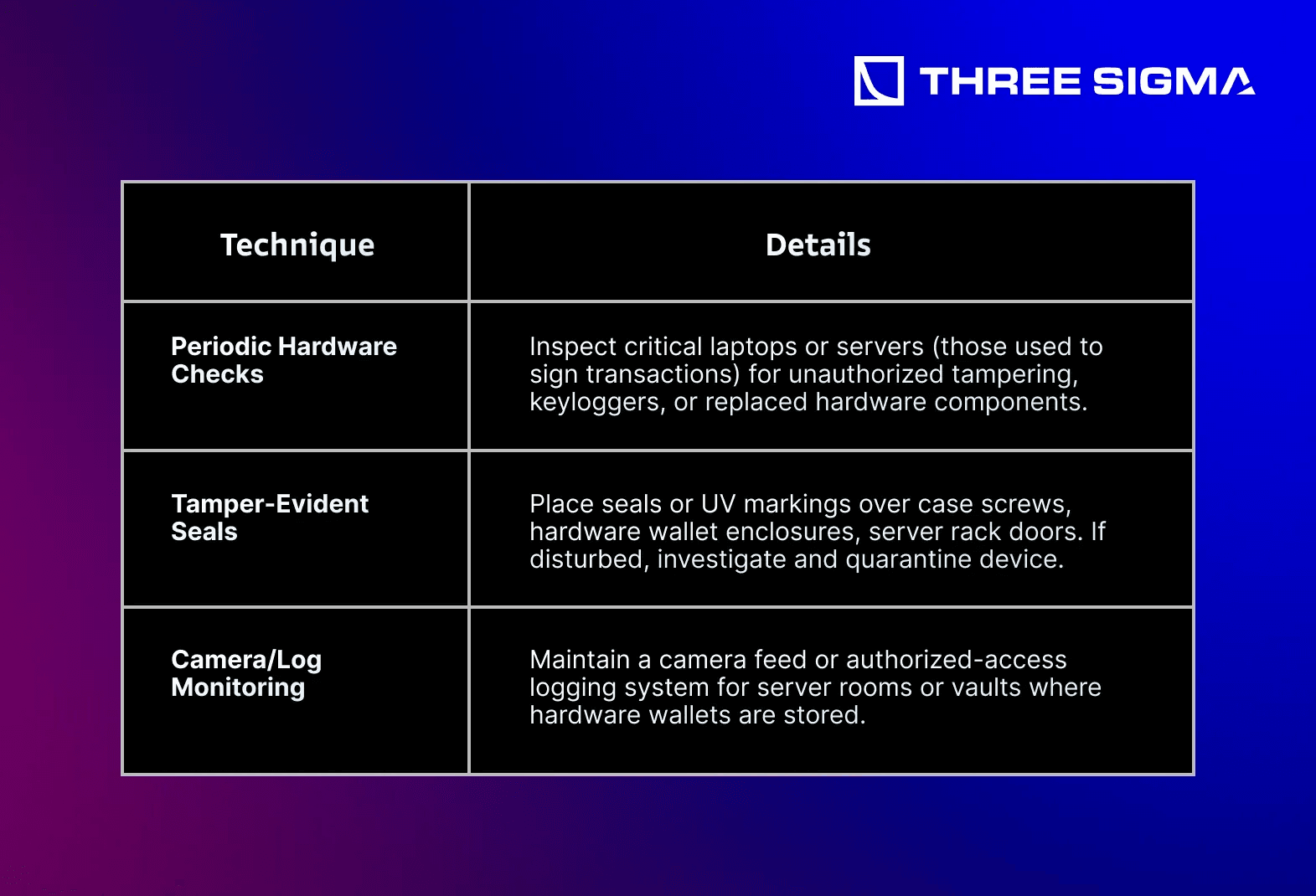
Tip: Similar to protecting cold storage vaults, treat physically accessible hardware as a potential infiltration route. If criminals or insiders can tamper with devices, advanced measures like epoxy or custom lock enclosures can reduce hardware extraction risks.
3.4.2 USB & Peripheral Device Policies
Rubber Ducky USB sticks or malware-laced flash drives can instantly compromise an endpoint if employees are free to plug in arbitrary devices.
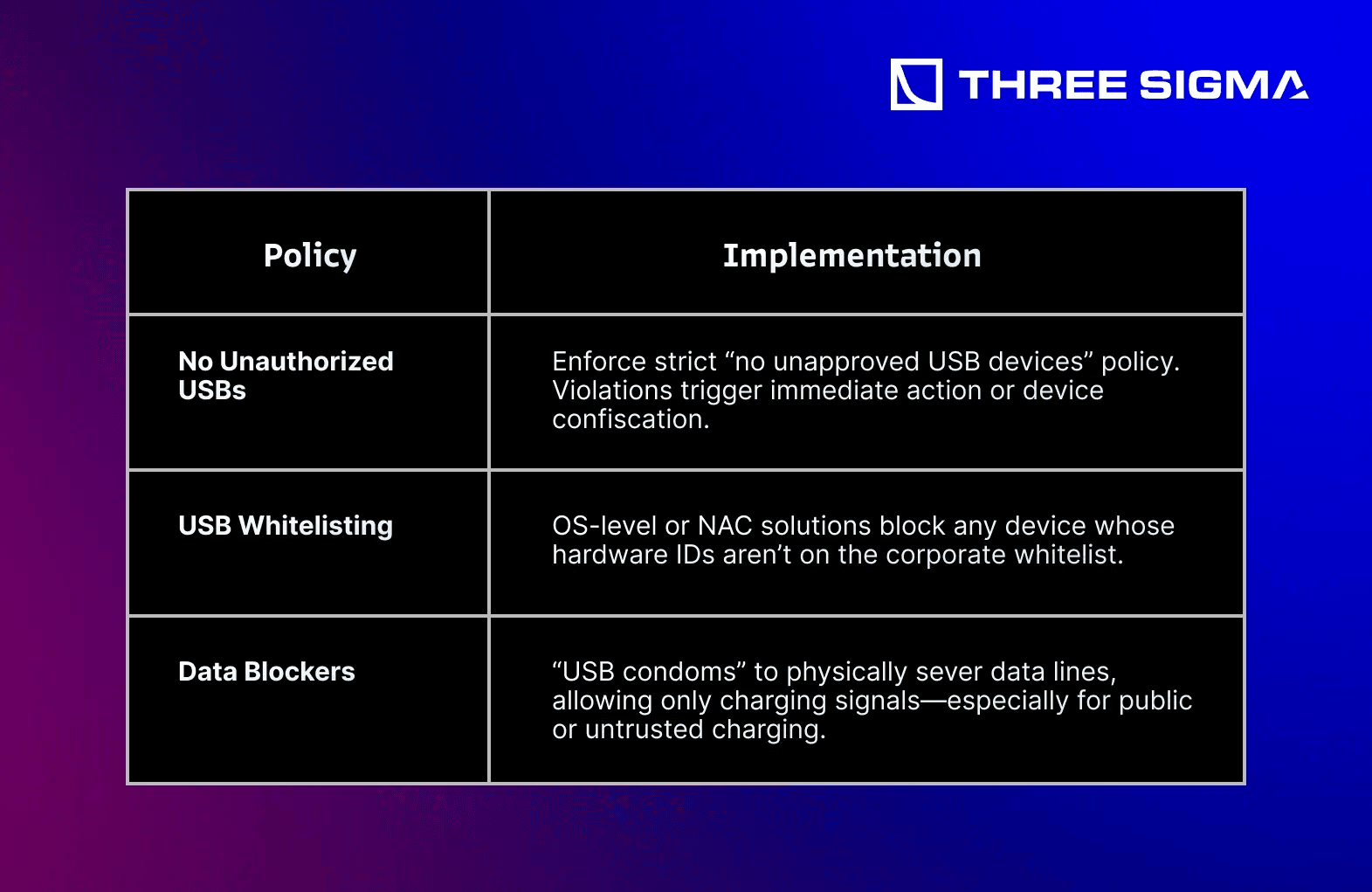
Reality: A single employee plugging in a Trojan-laced USB can circumvent segmentation. Physical device restrictions + user training are pivotal. Problem 20 emphasize physical infiltration attempts. USB controls are a first line of defense.
3.4.3 Secure USB & Port Control Software
For organizations with large or distributed teams, specialized solutions help enforce policy:
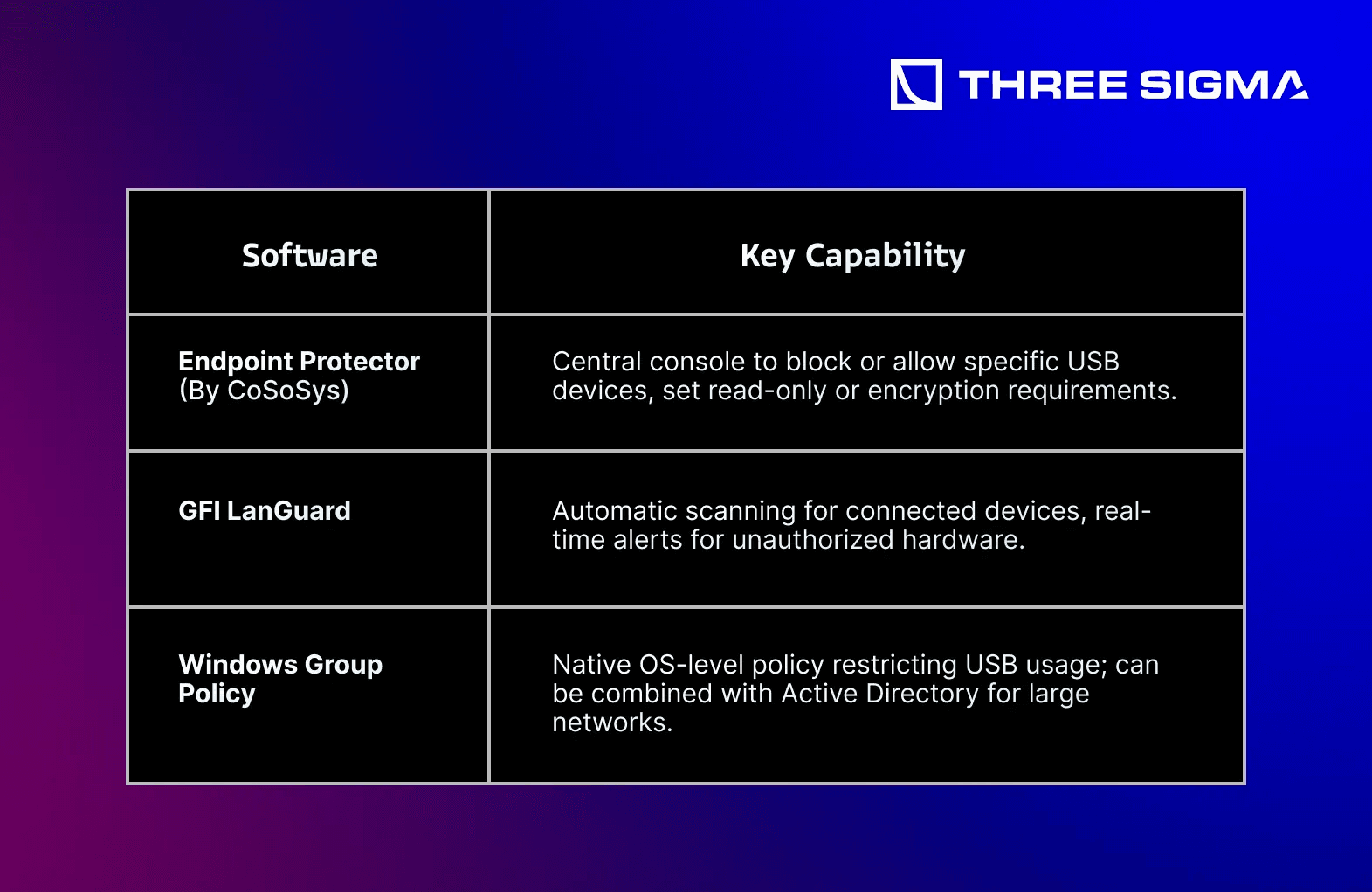
Key Takeaways for Network & Infrastructure Security
- Segment the Network – Divide your corporate environment into logical subnets (finance, dev, crypto) to contain attacks.
- Adopt Enterprise-Grade Defenses – Firewalls, IDS/IPS, EDR, and MDM solutions form the core shield for endpoints and networks.
- Leverage Virtualization – Qubes OS, Docker containers, or cloud-based VDI ensure each operation or microservice runs in strict isolation.
- Implement Hardware Safeguards – Regular device audits, tamper-evident seals, and strict USB policies help prevent physical infiltration or malicious implants.
- Continuous Monitoring & Auditing – Even the best initial setup requires ongoing oversight to catch new exploits or policy drift.
By proactively designing networks with segmentation, robust endpoint security, and hardware safeguards—crypto companies can drastically reduce the risk of catastrophic intrusions, stolen funds, and compromised IP. Combine these measures with employee awareness and incident response plans for a comprehensive, resilient defense against modern threats.
4. Privacy & Regulatory Compliance for Institutional Users
For institutions handling large volumes of personal data—like KYC, AML records, or employee information—maintaining privacy while meeting regulatory obligations is a delicate balancing act. Key frameworks such as GDPR (Europe), CCPA/CPRA (California), and others demand both technical safeguards and operational processes to prevent unauthorized disclosures.
Below, we explore strategies to keep user data private, minimize regulatory risk, and safeguard your organization’s reputation.

4.1 Privacy Levels & Regulatory Implications
4.1.1 Public Transparency vs. Confidentiality
Many crypto transactions occur on publicly visible blockchains—transparent by design. Institutions often require more confidentiality to hide trade strategies or client holdings from prying eyes. However, certain jurisdictions require auditable data or minimal disclosures.4.1 Privacy Levels & Regulatory Implications
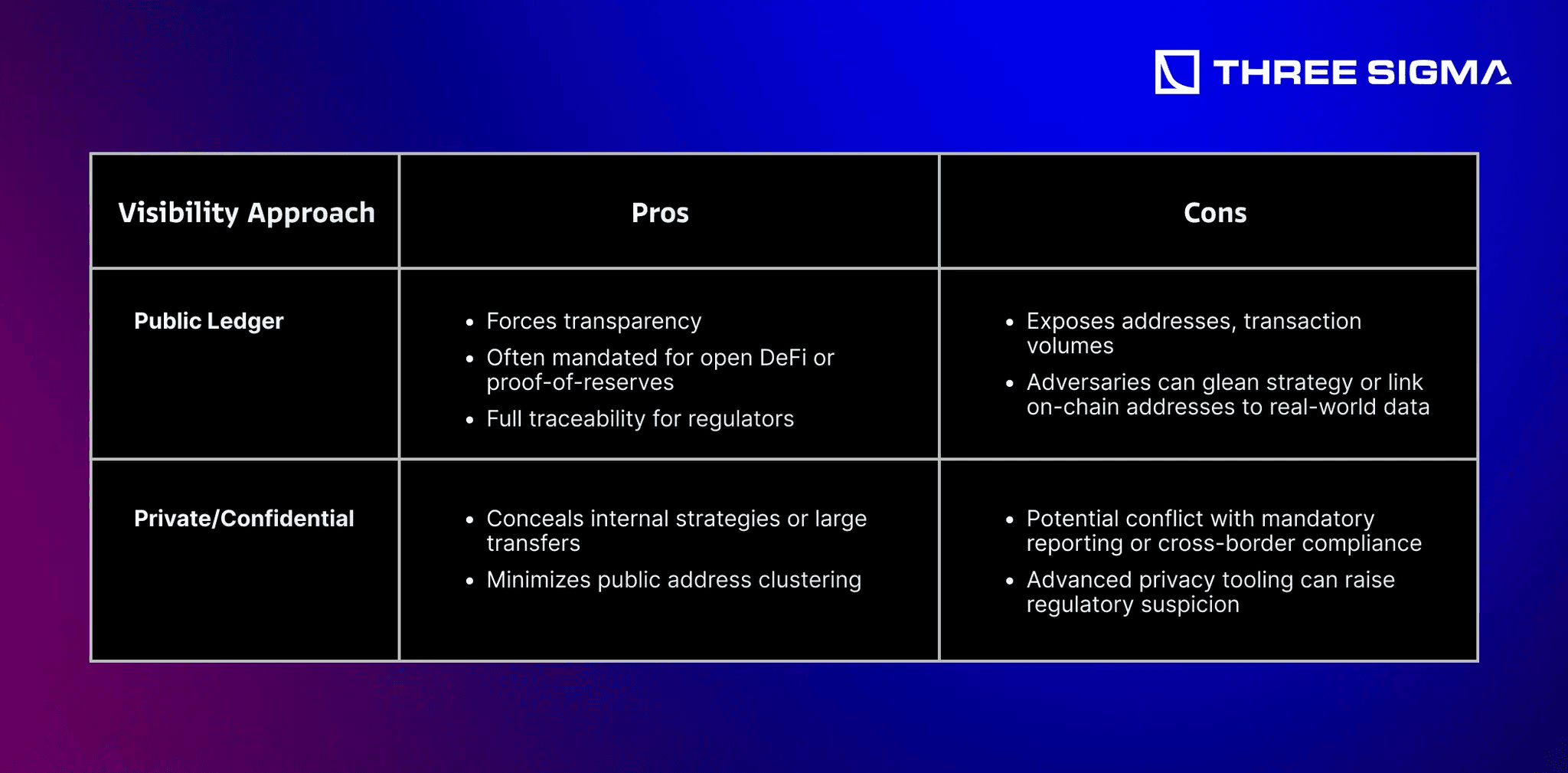
Note: In the EU, data must be collected only for specific, lawful purposes (GDPR data minimization). Over-collecting or publicly exposing user data can result in steep fines.
4.1.2 Handling KYC/AML Compliance Securely
Institutions often hold sensitive user data (e.g., passports, proof of address, financial statements) to comply with KYC/AML mandates. A single mishandling can trigger legal and reputational disasters.
1 - Customer Due Diligence
- Encrypt or tokenize personal data (PII).
- Restrict who can access the data; log every read/write attempt.
- Adhere to AML retention guidelines (often 5+ years).
2 - Compliance Retention & Disposal
- Ensure there’s a secure path to erase or anonymize records after the mandated period.
- Use robust versioning or backups with limited retention to avoid indefinite storage of user data.
Reference: Data Minimization & Inventorying Practices from the provided data-protection guidelines help ensure you only store the essential user data.

4.1.3 Major Data Protection Laws: GDPR, CCPA/CPRA
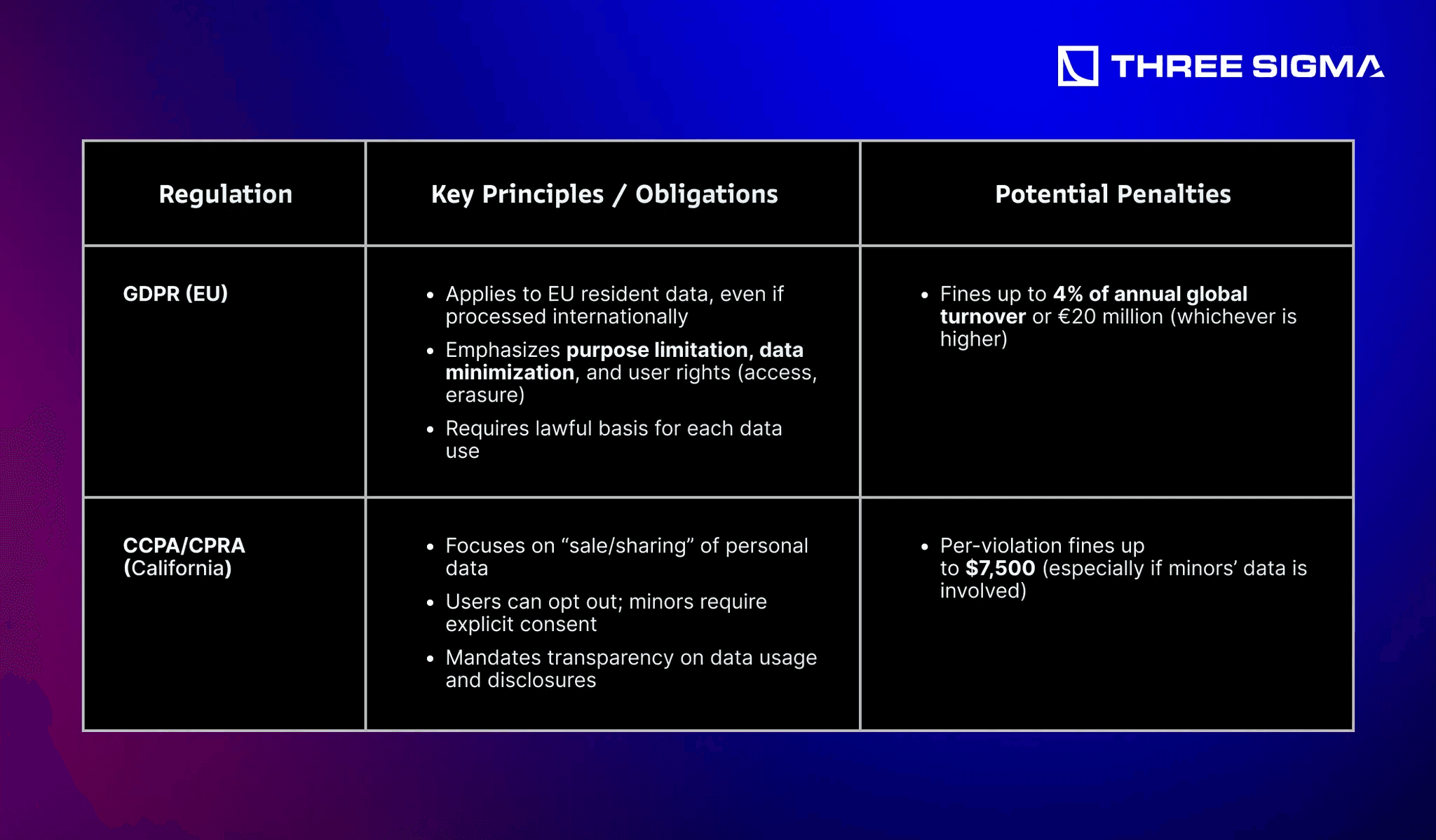
Keep in Mind: Data protection laws often have extraterritorial reach. If you process an EU resident’s data or market to them, you may need GDPR compliance—regardless of your company’s location.
4.2 Compartmentalization of Personal and Business Data
A fundamental best practice is segregating sensitive personal data (KYC, AML logs, user addresses) from general corporate or operational data.
4.2.1 Data Minimization & Pseudonymization
- Collect Only What’s Necessary: If it’s not required by compliance or operational workflows, don’t store it. Over-collection raises risk.
- Anonymize or Hash: Where possible, store only hashed references or pseudonyms. For on-chain addresses, consider mapping addresses to random internal IDs, rather than storing them in plaintext.
Implementation Tips
- Use role-based access to limit who can view or download personal data.
- Maintain a data inventory with each field’s purpose and retention policy. This helps demonstrate compliance and quickly identify high-risk data in a breach.
4.2.2 Virtual Mailboxes & Anonymous Domain Registration
For public-facing corporate details:
- Virtual Mailboxes: Use PO boxes or specialized forwarding addresses instead of exposing real offices or executives’ homes.
- Anonymous Domain Registration: Hide personal info in WHOIS records. Some domain providers or third-party “domain trustee” services mask ownership details.
4.2.3 Separate Corporate vs. Personal Device Policies
When employees use the same phone for personal and corporate tasks, mistakes can happen: private apps might leak corporate KYC data, or malicious websites can lead to cross-app data exploitation.
- BYOD (Bring Your Own Device) Policies: Employ MDM solutions that containerize corporate apps, limiting data sharing with personal apps.
- Prefer Dedicated Corporate Devices for staff who handle large transactions or direct user data. This isolates the environment and eases compliance checks.
Reference: Problem 22 underscores the vulnerability of smartphones. A strict separation ensures personal apps don’t inadvertently gain access to corporate KYC documents or wallet credentials.
4.3 Advanced Anonymity & Privacy Tools for Institutions
4.3.1 Privacy-Preserving Cryptography
4.3.2 On-Chain Privacy Techniques: Stealth Addresses, Mixers, L2s
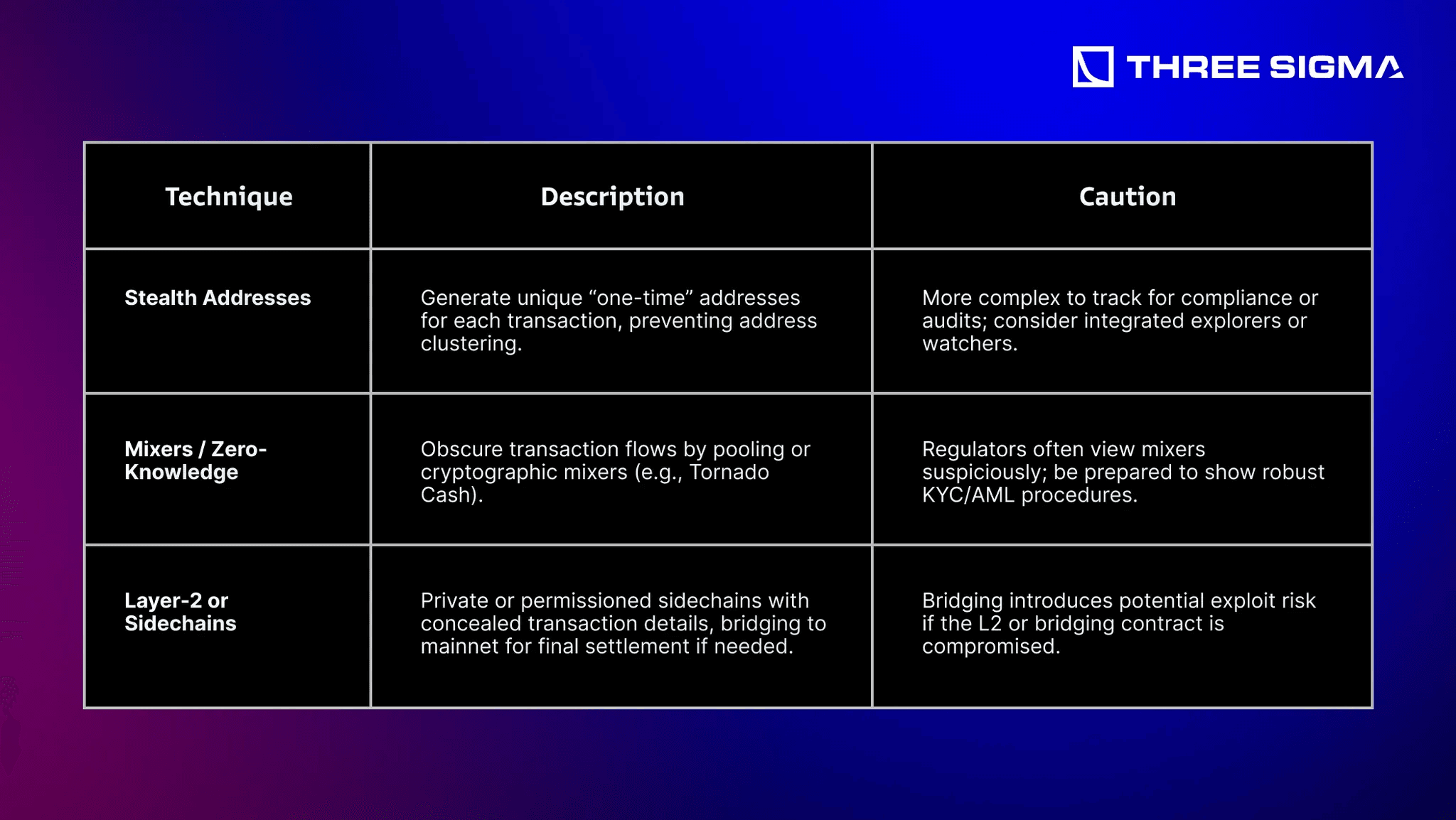
Regulatory Note: If your institution uses mixers, ensure you can prove compliance (e.g., verifying no illicit flows). Some jurisdictions see mixers as “facilitating money laundering” if insufficient KYC is implemented.
4.3.3 Secure Institutional Messaging & Communications
Encrypting chat or email content is standard in many enterprise contexts, but the metadata (who contacted whom, when, frequency) can also reveal patterns about deals or trades.
- End-to-End Encryption: Tools like Signal or ThreemaWork ensure message contents remain private.
- Metadata Minimization: Advanced solutions route or batch messages to reduce traceable patterns.
- Hardware Solutions: For extremely sensitive communications, some organizations use locked-down “secure phone” OSes (GrapheneOS or specialized Android forks).
Key Takeaways
1 - Map Out Regulatory Requirements
- Identify all jurisdictions you operate in or target. GDPR, CCPA, and other frameworks often apply extraterritorially if you process local residents’ data.
2 - Adopt Strong Data Governance
- Data inventory, minimization, and encryption are core practices. Knowing where and why you store data is half the battle.
3 - Invest in Advanced Privacy Tech
- Tools like MPC, zk-SNARKs, and stealth addressing help preserve confidentiality without stifling legitimate auditing needs.
4 - Separate Corporate from Personal
- Mitigate risk by enforcing dedicated devices or robust MDM for employees, and mask sensitive corporate info (domain WHOIS, mail addresses) with professional services.
5 - Continuously Monitor & Adjust
- Privacy regulations and chain analytics evolve quickly. Regularly review new compliance guidelines, data flows, and potential doxxing or correlation vulnerabilities.
By integrating these privacy strategies—while aligning them with KYC/AML mandates and data protection laws—institutions can maintain the trust of clients, regulators, and broader market participants, all while mitigating the substantial risks of privacy breaches or noncompliance fines.
By following the strategies in our article, you can minimize damage, expedite asset recovery, and reinforce your organization’s business continuity plans.
Conclusion
Modern enterprises integrating crypto assets face an ever-evolving threat landscape, where a single misconfiguration or overlooked procedure can trigger irreversible financial and reputational damage. Robust operational security, from private key management to network segmentation, and from compliance to incident response, is not an option but a necessity.
Key Takeaways
- A Comprehensive, Multi-Layered Framework OpSec isn’t just about buying the right products—it’s a holistic system of clear leadership, rigorous multi-sig policies, and carefully curated role-based access. Each department, from devs to finance, shares responsibility in defending crypto holdings.
- People Remain the Weakest (and Strongest) Link Even the most fortified hardware wallets or network perimeters can be undone by a single phishing email or compromised credential. Continuous, scenario-based employee training, insider threat awareness, and robust offboarding processes form your first line of defense.
- Infrastructure Hardening is Non-Negotiable Network segmentation, virtualization, and advanced endpoint protection drastically limit an attacker’s capacity to traverse your network. By converting a flat network into segmented zones, you build multiple layers an intruder must overcome.
- Privacy & Compliance as Strategic Assets Meeting GDPR, CCPA/CPRA, and KYC/AML requirements isn’t just about avoiding fines—it fosters client trust. Implementing privacy-preserving tools (e.g., zk-SNARKs, MPC) can become a competitive differentiator, proving you value user confidentiality.
- Plan for the Worst: Incident Response & Continuity Even with top-tier security, breaches happen. Responding quickly—containing the impact, recovering assets, and communicating transparently—can mean the difference between a minimal incident and an existential crisis. Regular drills, up-to-date runbooks, and a trusted response team are critical.
Multi-sig governance, role-based access, social engineering vectors, OPSEC at scale is hard. Our OPSEC Audit service helps organizations implement crypto-native controls that secure teams, assets, and reputations across the full attack surface.
Moving Forward
Treat OpSec as a living discipline, test it regularly, update training as threats evolve, and review potential vulnerabilities before they escalate. By layering defenses across people, processes, and technology:
- You reduce the chance that a single oversight (e.g., leaked admin key or social engineering) compromises the entire organization.
- You demonstrate regulatory diligence and user trust, which can be a significant market advantage.
- You stand ready to contain and recover from incidents quickly, preserving both financial assets and your organization’s reputation.
Ultimately, security is an ongoing conversation, not a one-time checklist. We encourage you to adapt these best practices to your unique threat model, stay agile in the face of rapid crypto innovation, and remember: a strong OpSec culture isn’t just about preventing attacks, it’s about emerging stronger whenever challenges arise.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.