Introduction
You didn’t get into crypto to lose everything to a dumb mistake.
But it happens,every day. Not because someone cracked a cold wallet with quantum tech, but because someone clicked the wrong link. Used the same password twice. Trusted the wrong person.
Operational Security (OpSec) isn’t optional. It’s the difference between keeping your coins and waking up broke. This guide cuts through the noise and shows you how to actually protect yourself:
- Safeguard your private keys from everyday pitfalls.
- Spot and circumvent phishing and social engineering tricks.
- Build a security posture that’s resilient enough to withstand everything from petty thieves to state-level adversaries.
Whether you’re new to crypto or a seasoned holder, the strategies here will help you stay one step ahead of ever-evolving threats. By the end, you’ll have not just a stronger wallet setup, but also the peace of mind to manage your assets without constantly looking over your shoulder.
1. Private Key Hygiene
Safeguarding substantial crypto holdings, whether a few coins or the proverbial $1 billion, starts with protecting your private keys from both digital and physical threats. True security requires layers of defense: hardware, secure backups, air-gapped devices, and well-tested recovery procedures. That layered approach is central to our blockchain security services. Below, we’ll break down best practices and real-world examples of how hardware wallets and other methods have been compromised so you can avoid similar pitfalls.
1.1 Cold Wallets, Hardware Devices, and Multisigs
1.1.1 Why Hardware?
- Offline Generation & Storage: Hardware wallets (e.g., Trezor, Ledger, Coldcard, Lattice) create and store your private keys offline. This drastically lowers exposure to online-based exploits like keyloggers, phishing, and malware.
- Reduced Attack Surface: Because keys never leave the device, attackers can’t directly lift them from your PC or smartphone. Transactions get signed within the wallet, then broadcast by your online device.

1.1.2 Known Hardware Wallet Hacks: Examples & Lessons
Despite their strong reputation, hardware wallets are not invincible. Many documented hacks require physical access or highly specialized attacks, but they highlight the need for layered security (e.g., using a BIP39 passphrase or multisig). Here are a few examples adapted from The Charlatan’s List of Hardware Wallet Hacks:
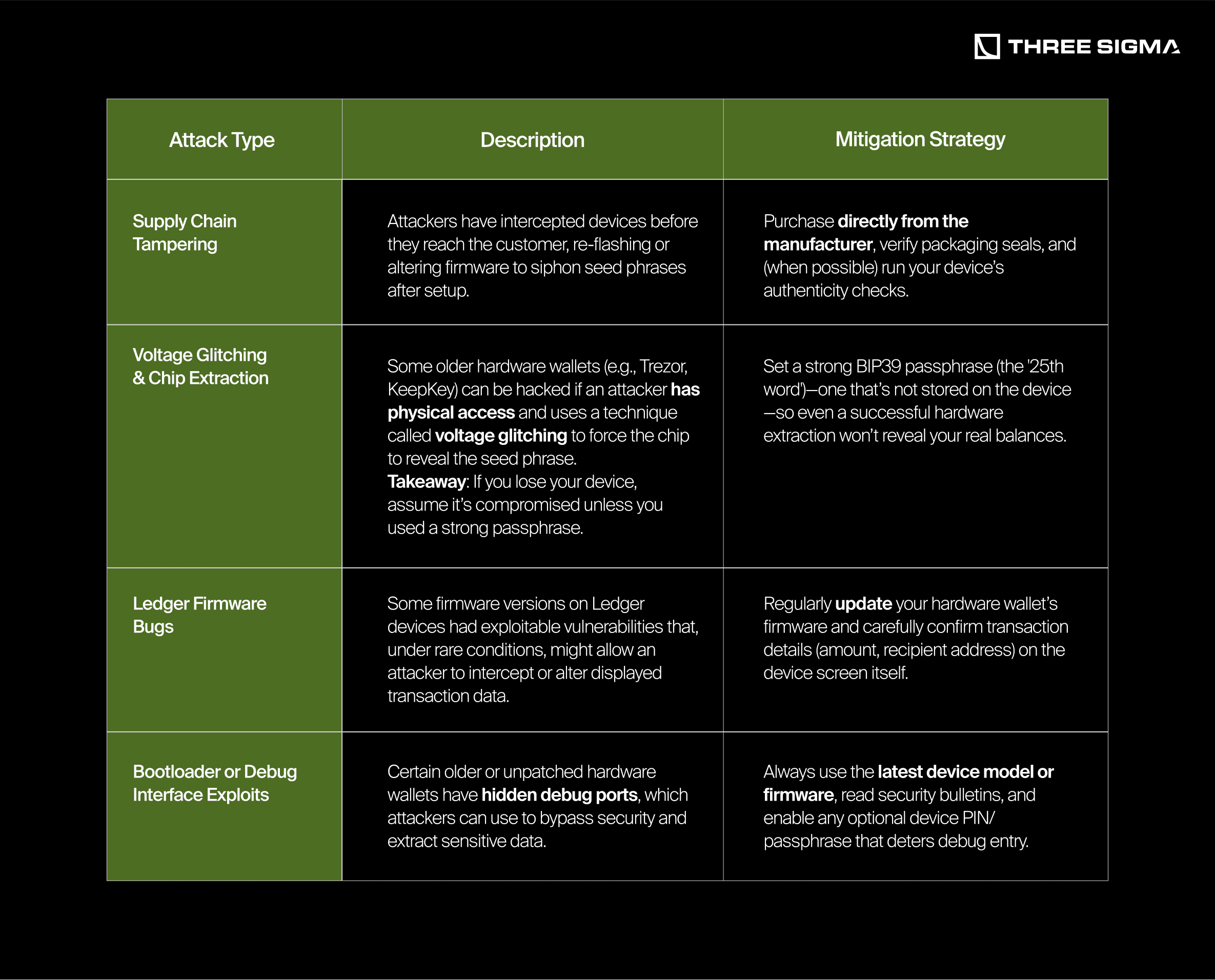
Key Takeaway: Hardware wallet hacks require physical possession and advanced skills. A strong passphrase or multisig setup makes extracting the seed nearly impossible.
1.1.3 Multisigs & Air-Gapped Setups
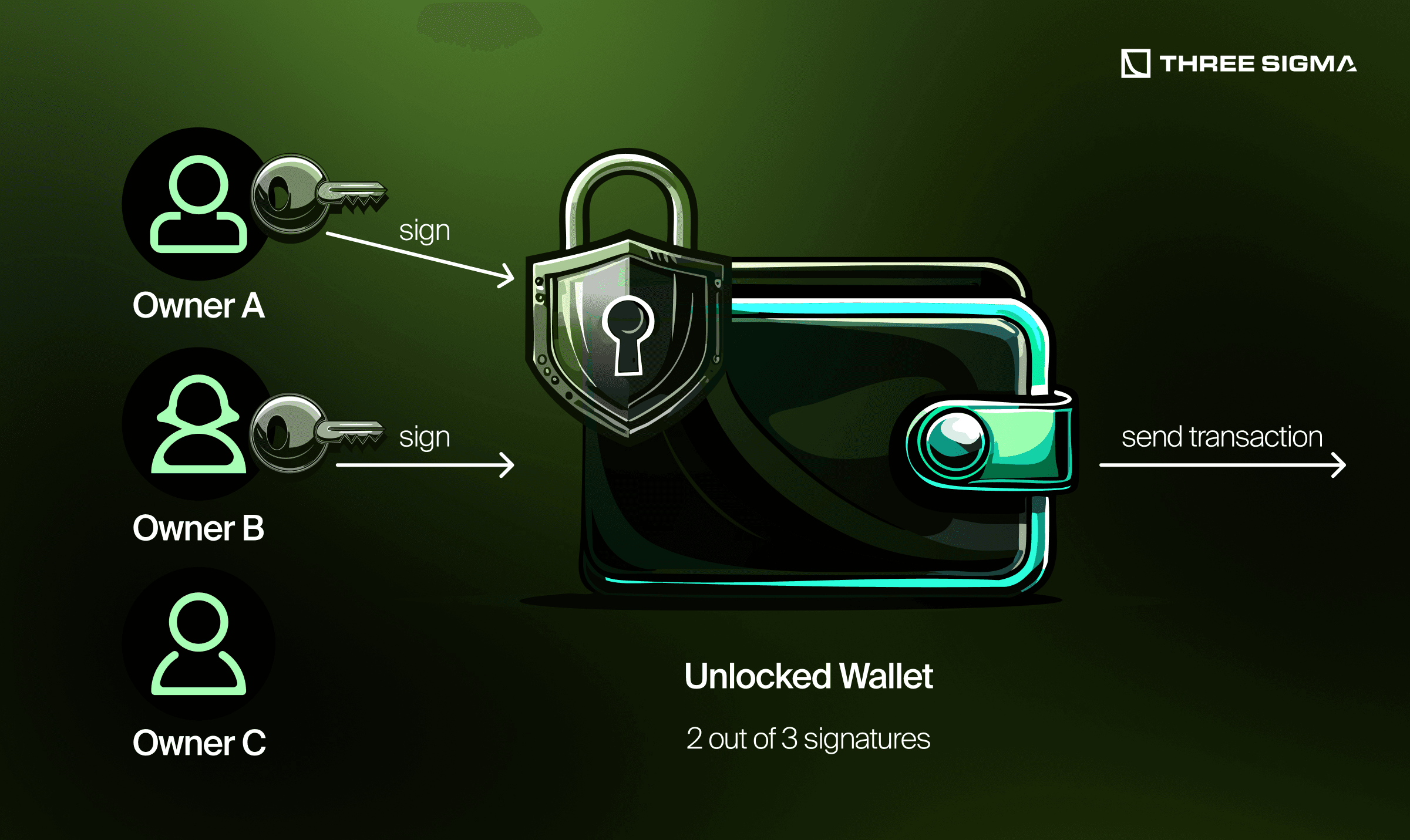
- Multisig (e.g., 2-of-3): Splitting keys across multiple devices ensures an attacker can’t drain your wallet by compromising just one. Even a stolen hardware wallet is not enough without the other keys.
- Trade-Off: More complexity means more points of failure, be sure to test the multisig with small amounts before entrusting large sums.
- Air-Gapped Computers: For ultimate isolation, generate keys and sign transactions on a PC that never touches the internet (e.g., an old laptop or Raspberry Pi). You then transfer signed transactions via USB or QR code.
- Physical Security Still Matters: Even air-gapped devices can be compromised if left unattended or infected beforehand. Guard them like you would guard a hardware wallet.
1.2 Brain Wallets & Why They’re Risky
A brain wallet derives a private key from a passphrase you memorize. While convenient, these are extremely prone to brute force attacks unless you use truly random, long, non-dictionary phrases. Various bots monitor blockchains for weak passphrases and seize any discovered funds immediately.
- High Entropy or Bust: Human-chosen phrases—song lyrics, poems, quotes—are rarely random enough to withstand cracking.
- No Margin for Error: If you forget or slightly misspell your phrase, your funds are lost forever.
- Recommendation: Avoid brain wallets unless you have an advanced, specialized reason to use them. Even then, verify the randomness with robust methods (e.g., hardware RNG or atmospheric noise) and practice recovering it before storing real assets.
1.3 Paper or Metal Wallets
1.3.1 Single Key vs. BIP39 Seed

- Paper Wallet: You print or write down a private key (or BIP39 seed). It’s air-gapped by definition but easy to lose or damage.
- Metal Wallet: Laser-etched or stamped metal plates survive fire, floods, and general wear and tear.
1.3.2 Offline Generation & Storage
- No Online Generators: Many “paper wallet generator” sites have been outright scams, delivering pre-generated addresses that funnel deposits to attackers. Use a trusted offline generator (e.g., an air-gapped device running open-source software like [Ian Coleman’s BIP39]) or rely on your hardware wallet’s built-in seed generation.
- Multiple Backups, Multiple Locations: Keep at least two copies, stored separately (e.g., one in a home safe, another in a safe-deposit box). If one is lost or destroyed, you can recover with the other.
1.3.3 Encryption & Steganography
- Optional Encryption: Some people prefer storing an encrypted version of their seed (e.g., via GnuPG, VeraCrypt) so that even if someone finds your paper, they still need the encryption passphrase. However, decrypting on a connected device (laptop, desktop, etc.) introduces a risk: malicious software could capture your seed during the process.
- Steganography: Hiding your seed in images or other media is an extra layer of obscurity. However, extracting that hidden data on a connected device poses a risk: if your system is compromised, the seed can still be exposed. Also note that any small error in the steganographic process may corrupt the hidden data, making it unrecoverable.
1.4 Never Reuse Seeds & Periodic Validation
- Unique Keys Per Use Case: Reusing a seed across multiple wallets (hot or cold) increases your attack surface. A breach of one wallet now jeopardizes all funds tied to that seed.
- Fire Drills: At least once a year, practice recovering your seed on a fresh device or separate instance of your wallet software. This ensures your backup is correct, up to date, and that you know the steps by heart.
- Seed Rotation: If you hold very large amounts or your threat model changes (e.g., you move to a higher-risk jurisdiction), consider rotating to a new seed and transferring funds. This guards against hidden or delayed attacks on your old seed.

1.5 Practical Takeaways
- Layered Security Rules
- Hardware wallets drastically reduce online risk—but aren’t magically unhackable. Combine them with strong passphrases, secure purchases, and (when warranted) multisig.
- Defend Against Physical Threats
- Keep your devices locked up, limit who knows you hold crypto, and understand that an attacker with physical access can sometimes exploit advanced vulnerabilities.
- Backup Diligence
- Use multiple backups (paper or metal), stored in separate secure locations. Periodically test them so you’re sure recovery works.
- Avoid Brain Wallet Pitfalls
- Unless you have advanced knowledge of generating truly random, memorized passphrases, do not rely on a brain wallet.
- Continuous Vigilance
- Pay attention to firmware updates, security announcements, and best practices in the crypto community. Attackers evolve, so your security measures must as well.
Remember: Effective OpSec is about minimizing each avenue of attack. Even if one layer fails (e.g., a flawed hardware wallet firmware), your additional safeguards—like a BIP39 passphrase or a multisig requirement—ensure that a single exploit doesn’t spell disaster.
2. Phishing & Social Engineering Awareness
Phishing and social engineering attacks remain some of the most effective and devastating attack vectors in the crypto space. Unlike technical exploits that target vulnerabilities in smart contracts or exchanges, social engineering manipulates people—exploiting human psychology, trust, and urgency to steal assets.
Unlike traditional finance, crypto transactions are irreversible, making phishing especially dangerous. A single misstep—entering a private key on a fraudulent website, signing a malicious transaction, or approving an unsafe contract—can lead to complete and permanent loss of funds.
Below, we explore common phishing tactics, real-world case studies, and defensive strategies that should be part of every user’s operational security.
2.1 How Hackers Bait Victims
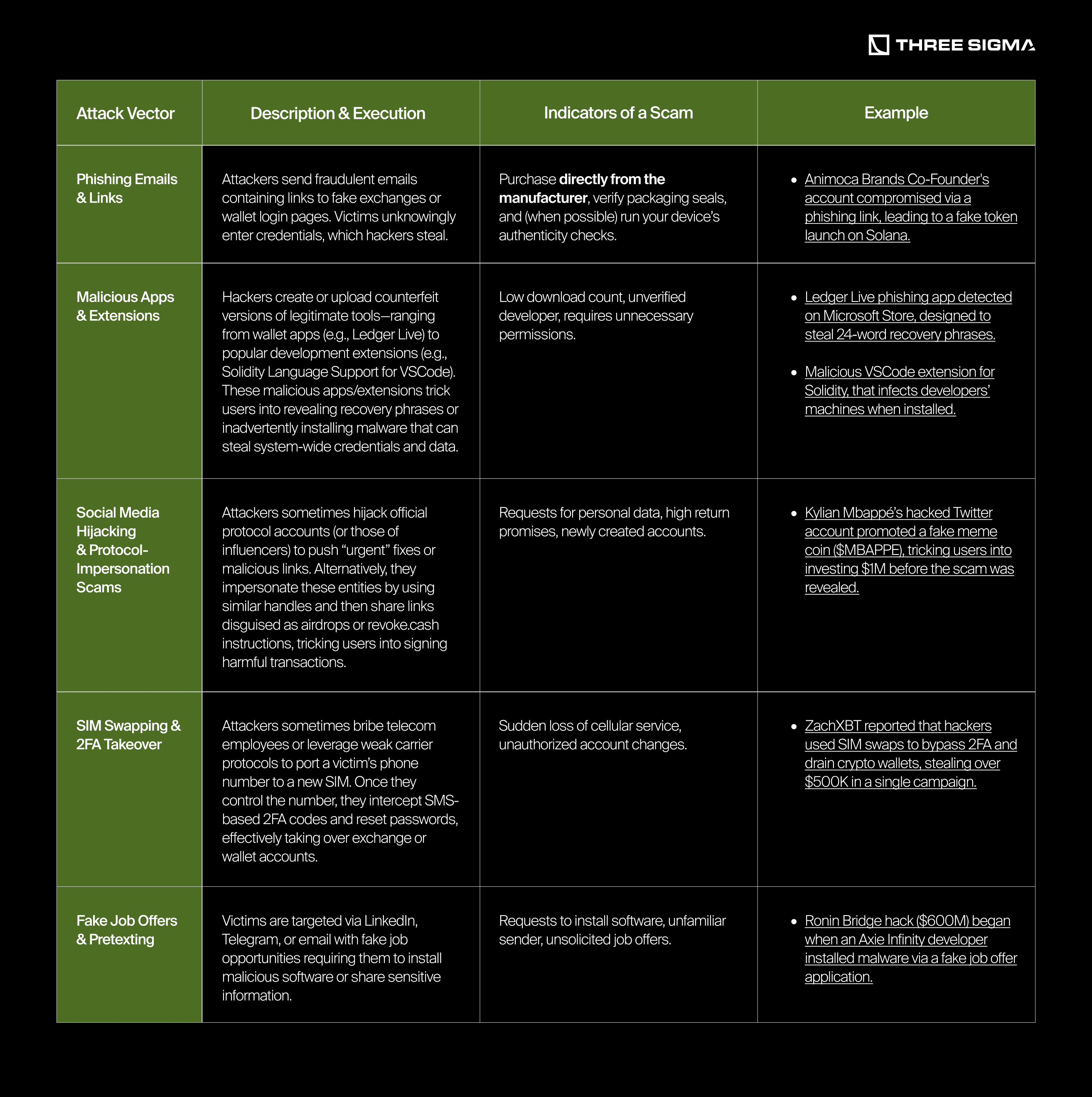
2.1.1 Phishing Emails & Links
Hackers utilize a variety of attack vectors to target cryptocurrency users. The table below outlines the most prevalent techniques:
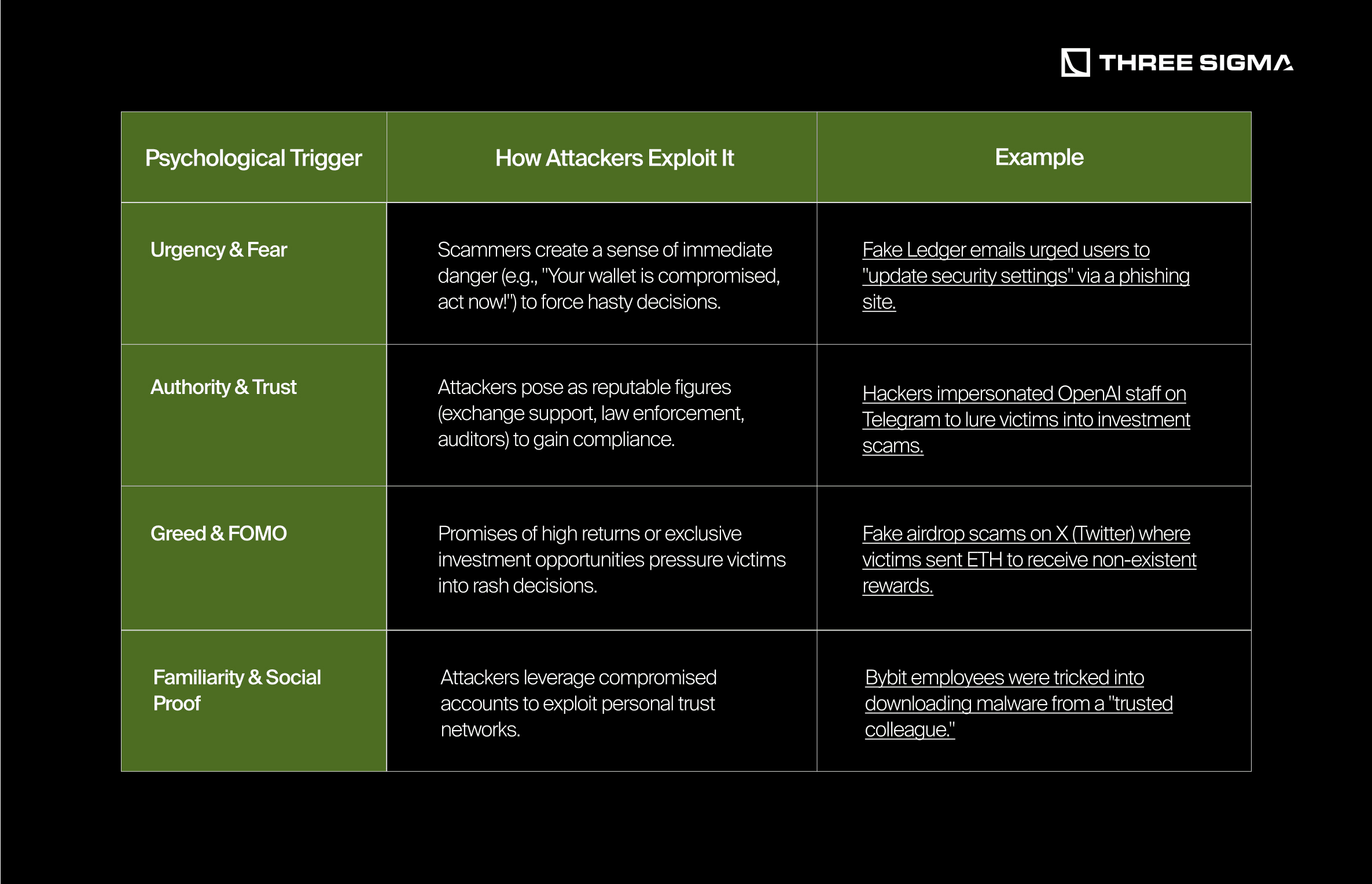
2.1.2 Psychological Manipulation Tactics
Social engineering relies on human psychology to trick victims. The table below outlines the most commonly exploited psychological triggers:
2.2 Mitigation Strategies
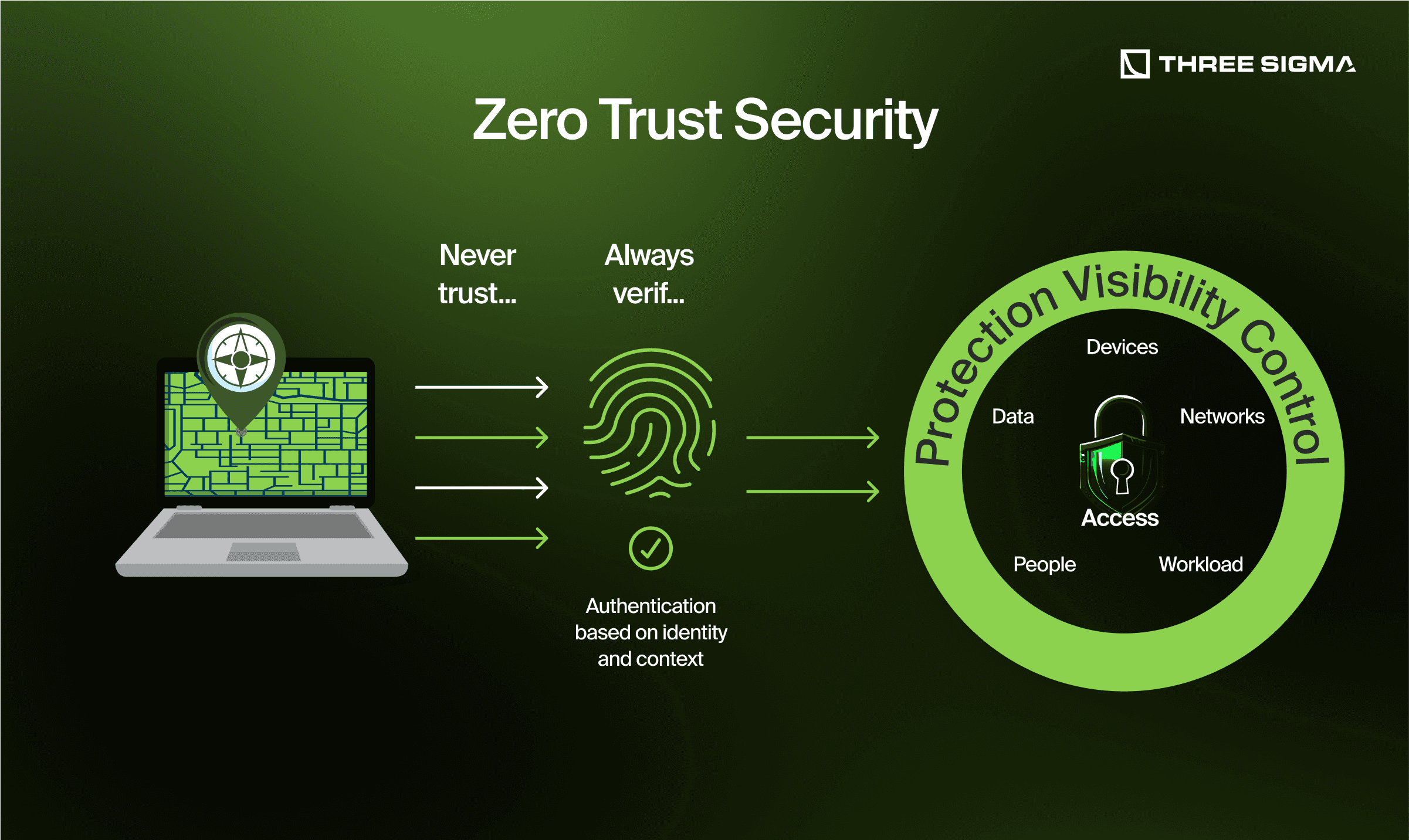
2.2.1 Adopting a Zero-Trust Security Model
The zero-trust principle assumes that all incoming messages, links, and requests are potentially malicious unless independently verified.
Implementation Steps
- Skepticism by Default: Assume all unsolicited messages (emails, social media DMs) are phishing attempts.
- Independent Verification: If you receive an urgent message from a company or individual, verify it through an official communication channel.
- Limit Public Exposure: Avoid discussing crypto holdings publicly, as this increases the likelihood of being targeted.
2.2.2 Strengthening Authentication Layers
- Avoid SMS-Based 2FA: SIM swap attacks allow hackers to hijack SMS-based authentication codes.
- Use Time-Based One-Time Passwords (TOTP): Apps like Aegis or Authy generate offline 2FA codes that cannot be intercepted remotely.
- Leverage Hardware Security Keys: Physical devices like YubiKey or SoloKey ensure authentication occurs locally on the device.
- Adopt a Password Manager: Storing or reusing passwords is risky. Use a reputable password manager (e.g., KeePass, Bitwarden, or 1Password) to generate strong, unique passwords for each account. This practice minimizes the chance that a single compromised password leads to multiple account breaches.
2.2.3 Enhancing Social Media & Email Security
Email Security Measures
- Enable DMARC, SPF, and DKIM on Domain Emails These protocols prevent email spoofing.
- Use Encrypted Email Services (ProtonMail, Tutanota) Prevents third parties from intercepting messages.
Social Media Protection
- Restrict DMs to Known Contacts Attackers often reach out via Twitter (X), Telegram, or Discord.
- Enable Login Notifications Alerts you to unauthorized login attempts.
2.2.4 Incident Response & Recovery
If you suspect or confirm that your credentials or crypto holdings have been compromised:
- Immediately Transfer Remaining Funds Move assets to a secure wallet.
- Revoke Active Sessions Check for logged-in devices on exchange or wallet accounts.
- Check Approved Smart Contract Interactions Use tools like Revoke.cash to remove unauthorized approvals.
- Report the Attack
- File reports with exchanges or wallet providers.
- Report impersonations to Twitter/X, Discord, or Telegram.
Final Thoughts
Phishing and social engineering attacks are among the most dangerous and effective threats in the crypto space. As hackers refine their tactics, users must continually adapt by implementing a zero-trust security model, leveraging hardware-based authentication, and conducting regular security audits.
By applying these best practices, you significantly reduce the risk of falling victim to phishing schemes and ensure that your assets remain secure in an increasingly hostile digital environment.
Conclusion
You’ve now seen how critical proper private key management and vigilance against phishing can be. From using hardware wallets with strong passphrases to recognizing social engineering tactics, these foundational steps help ensure your assets stay firmly under your control.
Yet, even the most secure wallet is vulnerable if the device you use to access it is compromised.
In the next section, we’ll explore device security—covering everything from system hardening and network isolation to malware prevention and recovery planning. By applying these additional layers of protection, you’ll round out your crypto OpSec and close off loopholes attackers love to exploit.
From founder DMs to malicious pop-ups, attackers don’t need exploits when humans are easier targets. Our OPSEC Audit service helps teams prevent leaks, train personnel, and put guardrails around private key access and signing.
Frequently Asked Questions (FAQ)
1. What is OpSec, and why does it matter for crypto users?
Answer: OpSec (Operational Security) encompasses the strategies and precautions taken to protect sensitive information—like your private keys—from potential adversaries. In crypto, where transactions are irreversible, strong OpSec is the difference between safeguarding your assets and losing them to hacks, scams, or theft.
2. Are hardware wallets really necessary, or can I just store coins on an exchange?
Answer: While storing funds on an exchange is more convenient, it’s also riskier since exchanges can be hacked or subject to government seizures. Hardware wallets greatly reduce your exposure by keeping private keys offline. It’s one of the most effective defenses against digital attack vectors such as malware, phishing, or data breaches.
3. How secure are hardware wallets if hackers can still hack them?
Answer: No device is 100% invincible, but hardware wallets are far more secure than software wallets or exchange custody. Known hardware-wallet attacks often require advanced skills and physical access to your device. By adding layers—like a strong BIP39 passphrase, routine firmware updates, or multisig—you make it significantly harder for attackers to succeed.
4. What exactly is a “BIP39 passphrase,” and should I use one?
Answer: A BIP39 passphrase is an optional “25th word” added to your seed phrase, effectively creating a second layer of protection. Even if someone extracts or steals your hardware wallet’s seed, they won’t access your real funds without the separate passphrase. Using a strong, memorable passphrase is one of the simplest ways to boost wallet security.
5. Are multisig and air-gapped setups only for advanced users?
Answer: They’re more complex than a single hardware wallet, but they aren’t exclusively for experts. Many users employ a 2-of-3 multisig (e.g., two hardware wallets plus a trusted third backup key) to reduce single points of failure. Air-gapped setups can be done with basic technical knowledge: generating keys offline and signing transactions on a device never connected to the internet.
6. What are the risks of using a brain wallet?
Answer: Brain wallets derive private keys from a user-generated passphrase. Human-chosen phrases—song lyrics, quotes, or typical dictionary words—are easily brute-forced by bots. If you forget or slightly mistype it, your funds are lost forever. Unless you have a proven method to create truly random, high-entropy phrases, a brain wallet is generally too risky.
7. Should I trust online paper wallet generators?
Answer: Be extremely cautious. Some “paper wallet generator” websites have been outright scams, pre-generating addresses that funnel deposits to attackers. If you want a paper or metal backup, use reputable offline tools (like an air-gapped device running open-source software) or the built-in generation feature on a verified hardware wallet.
8. How can I avoid phishing and social engineering attacks?
Answer:
- Adopt a zero-trust mindset: Treat every unsolicited message or link as suspicious.
- Use strong authentication: Prefer app-based 2FA or hardware security keys over SMS codes.
- Verify before acting: Confirm “official” messages via known channels, and don’t rush because of urgency tactics.
- Protect your social media: Restrict DMs to trusted contacts and enable login notifications.
9. What should I do if I suspect my wallet or account is compromised?
Answer: Immediately move remaining funds to a secure wallet, revoke all exchange or DApp permissions (e.g., via Revoke.cash), change passwords, and switch to more secure authentication methods. If social media accounts are impersonating you or a project you follow, report it directly to the platform.
10. How often should I update my security practices?
Answer: Security is a continuous process. Check for firmware updates, new wallet releases, and best-practice recommendations at least every few months. Conduct an annual “fire drill” to ensure you can recover your wallets from backups and that any new devices or methods work seamlessly.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.