Introduction
Welcome to the second part of our OpSec for Everyday Users guide. If you haven’t yet read Part 1, we highly recommend starting there—it covers how to protect your private keys and avoid common phishing attacks that can drain your wallet in seconds.
In this part, we turn our focus to device security. Even the most secure wallet setup can be undone by a compromised laptop or network. We’ll walk through how to harden your operating system, isolate risky activity with virtual machines and sandboxes, lock down your network, and prepare for worst-case scenarios. Whether you're managing a few tokens or a serious portfolio, securing the device you use is non-negotiable.
1. Device Security
When it comes to operational security, protecting the environment in which you access your crypto assets is just as important as safeguarding your private keys. Even the most secure cold wallet can be compromised if used on a compromised device or network, and for teams shipping code, a smart contract audit is the other half of that defense.
This section covers the core principles of device security, including system hardening, virtualization, sandboxing, network isolation, malware prevention, and operational best practices.

1.1 System Hardening: Clean & Secure Setup
A secure system starts with minimizing attack surfaces and hardening software configurations.
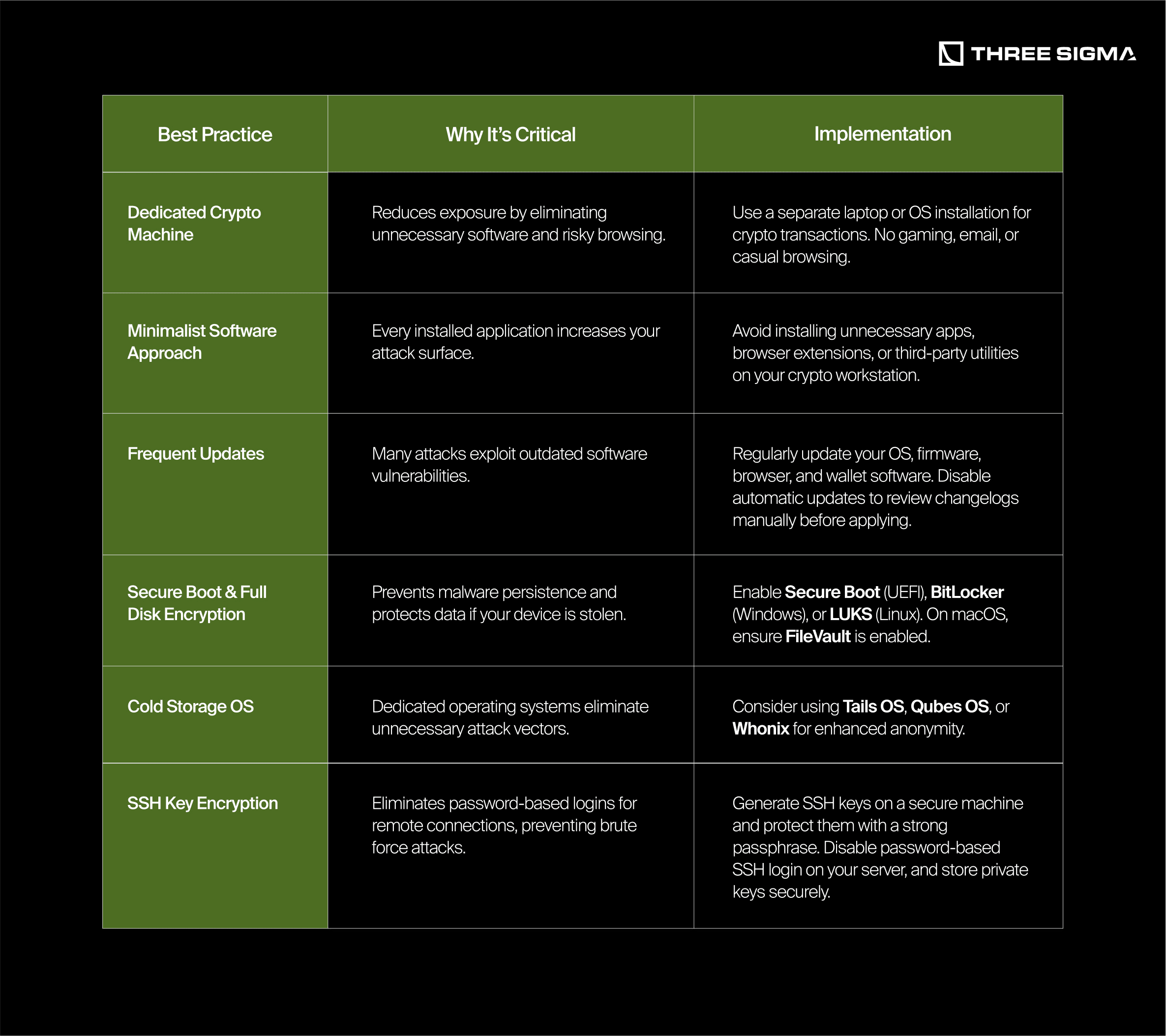
Pro Tip: If you can, disable auto-download or auto-install features for both applications and system updates; review each update before installing to ensure it’s from a legitimate source.
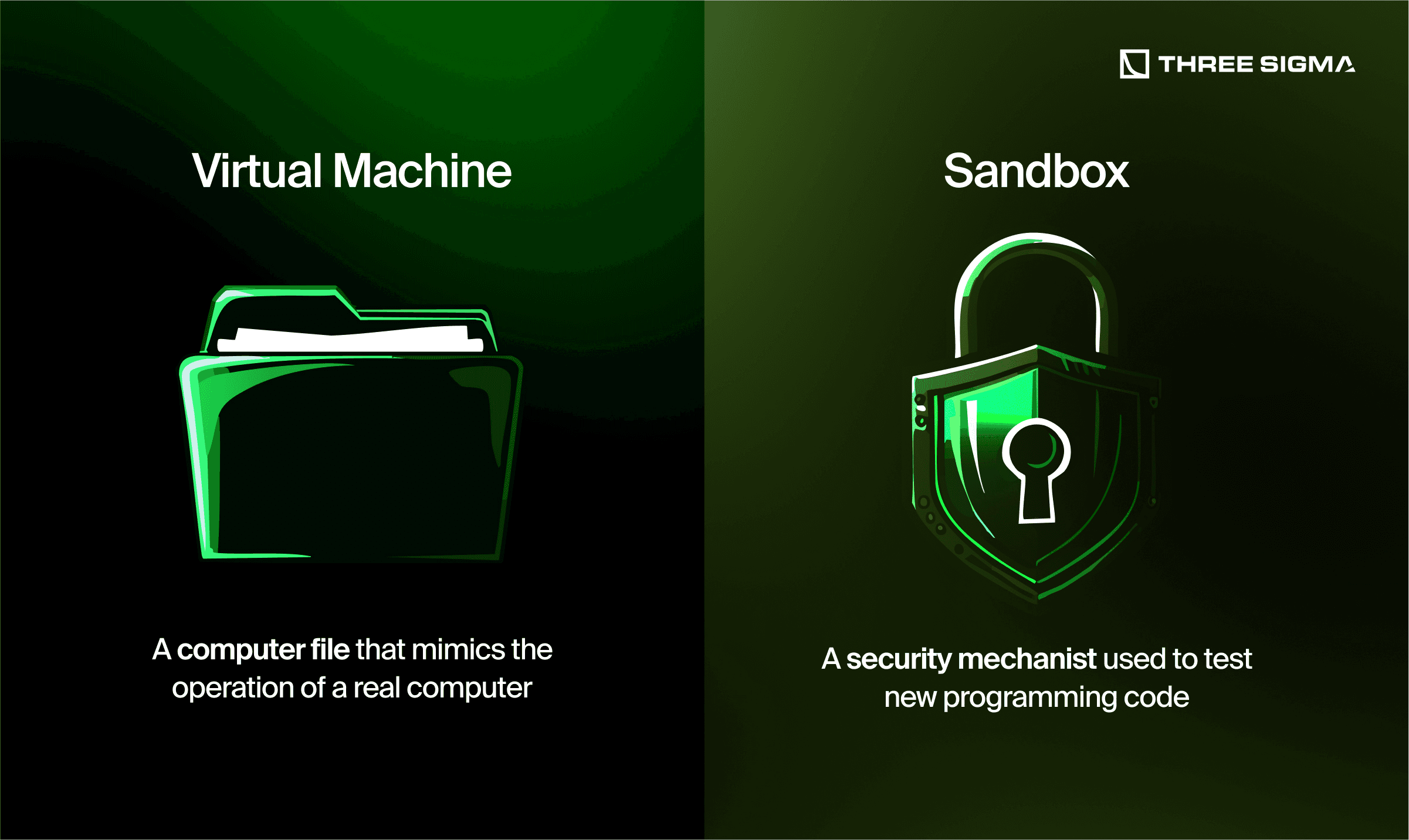
1.2 Virtualization & Sandboxing
- Virtual Machines (VMs) Consider running a separate VM for higher-risk activities—like opening emailed attachments or exploring new crypto protocols. If malicious code runs inside that VM, it won’t infect your primary operating system. Tools such as Qubes OS, Whonix, or even a standard VirtualBox/VMware setup can be invaluable.
- Sandboxing Tools For quickly examining suspicious files (like PDF resumes, invoices, or unknown installers), use specialized software (e.g., Dangerzone or any.run) to open them in an isolated sandbox environment. This helps contain potential malware.
1.3 Network Hygiene & Isolation
Securing your network is just as crucial as securing your device.
1.3.1 Segmented Networks
- Use separate Wi-Fi networks for crypto transactions and general browsing.
- If possible, set up a hardware firewall (e.g., pfSense, OPNsense) to monitor and restrict network traffic.
1.3.2 VPN, DNS Security & Public Wi-Fi Risks
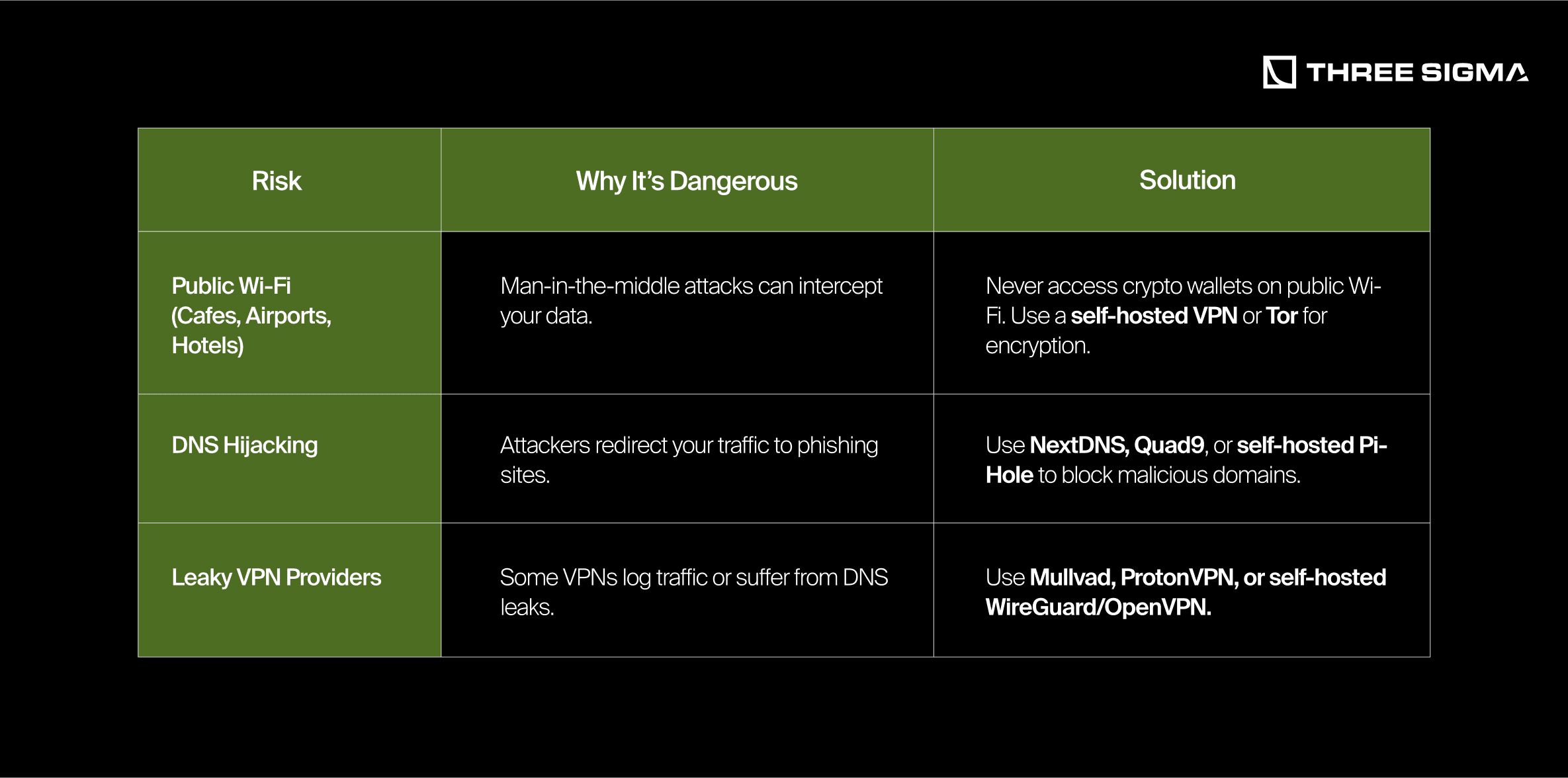
Pro Tip: For high-security setups, use a hardware VPN (e.g., GL.iNet routers) instead of software-based solutions.
1.4 Malware Prevention & Hardware Security
Even a well-configured system can fall victim to malware if security hygiene is neglected.
1.4.1 Preventing Malware Infections
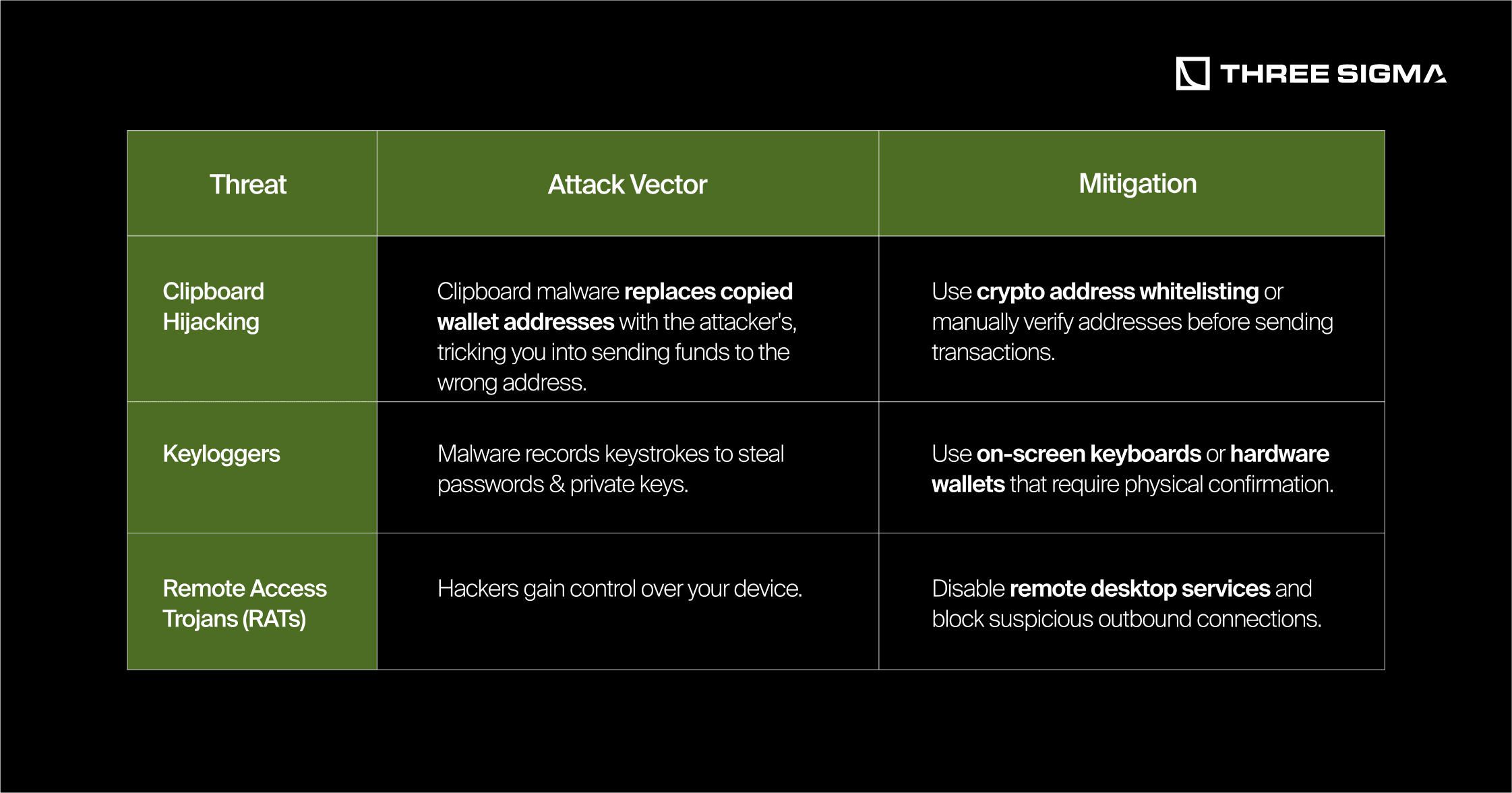
1.4.2 USB Security: Avoid “Rubber Ducky” Attacks
Malicious USB drives (e.g., Rubber Ducky) can run hidden scripts as soon as they are plugged in, stealing data or injecting malware.
- Never plug in unknown USB devices.
- Use a data blocker (USB condom) when charging in public places.
- If USB access is required, only connect through a sandboxed VM.
1.5 Operational Security & Monitoring
Even with all technical defenses in place, human error and overlooked security gaps remain the biggest risks.
1.5.1 Securing User Credentials

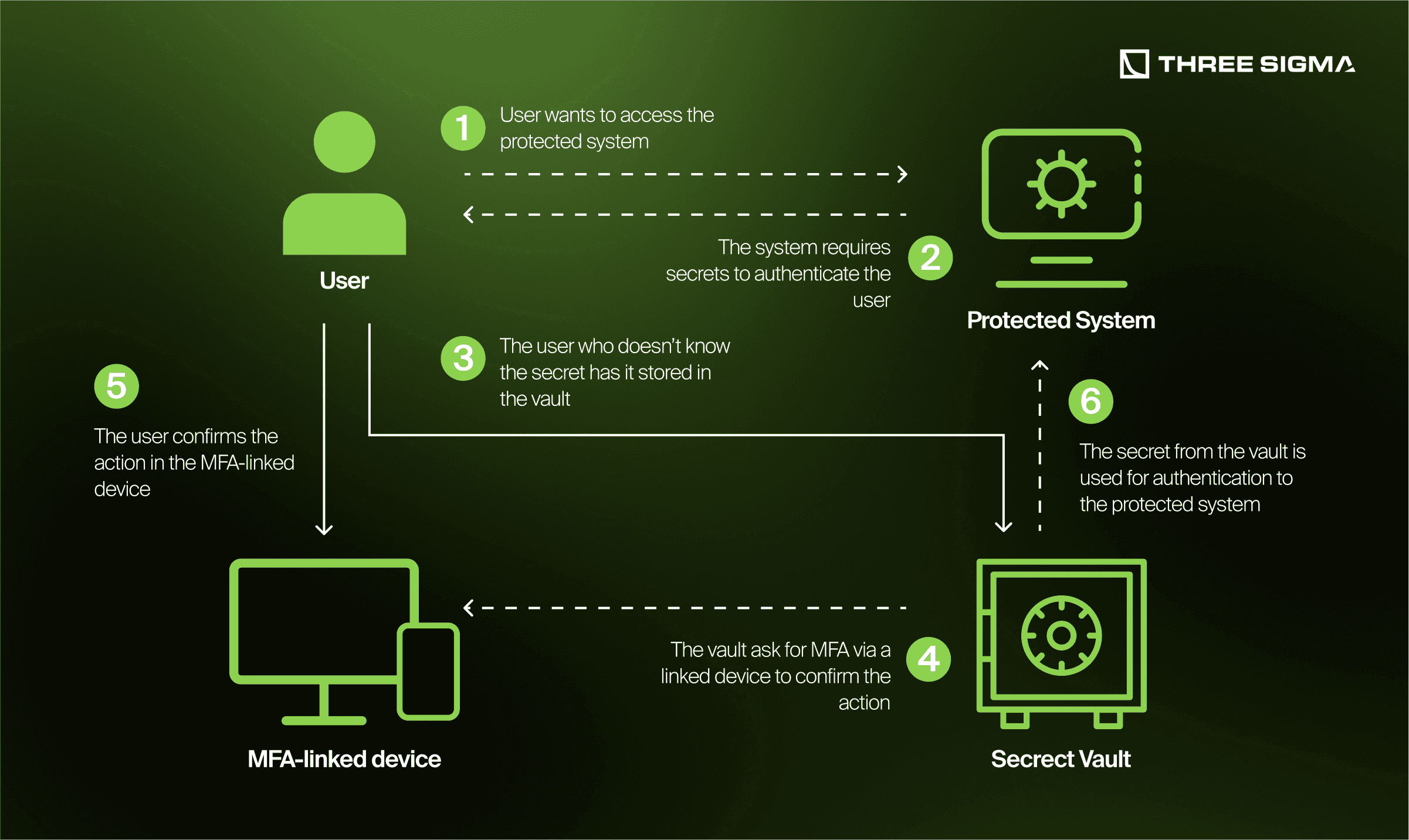
1.5.2 Continuous Monitoring & Alerts
- Monitor outgoing network traffic using Little Snitch (macOS) or OpenSnitch (Linux).
- Use OS-level integrity checking (e.g., Tripwire, AIDE) to detect unauthorized changes.
- Set up real-time alerts for login attempts or unexpected device activity.
1.5.3 Emergency Recovery Plans
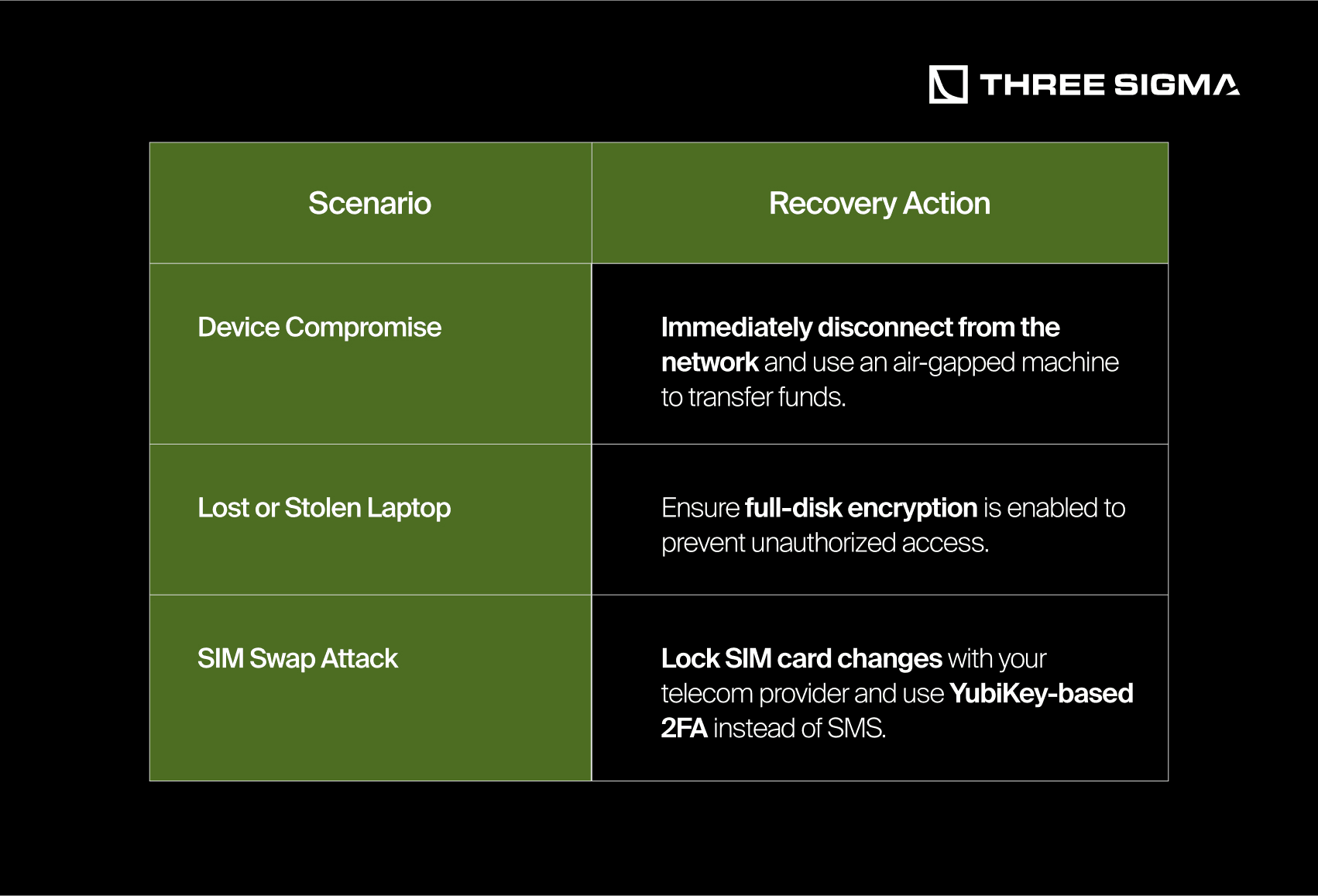
Pro Tip: Store encrypted backups of critical data in multiple offline locations to protect against physical theft or ransomware.
Key Takeaways
- Use a dedicated machine for crypto operations—never mix with general browsing or email.
- Keep your OS and software updated, but disable auto-updates to manually verify patches before installation.
- Virtualization and sandboxing can protect against malware infections from phishing attempts or file downloads.
- Network segmentation and a trusted VPN reduce the risk of network-based attacks.
- Harden device access with strong passwords, full-disk encryption, and real-time monitoring.
- Prepare for disaster recovery with encrypted backups and incident response plans.
2. Anonymity & Privacy
Maintaining privacy in a digital-first world—especially within crypto—requires an intentional approach. Whether you are casually protecting your on-chain activities or fully dissociating your real-world identity from your online persona, privacy decisions must be tailored to your threat model.
This section explores levels of privacy, tools for anonymity, and operational security techniques that can help you achieve maximum data protection.
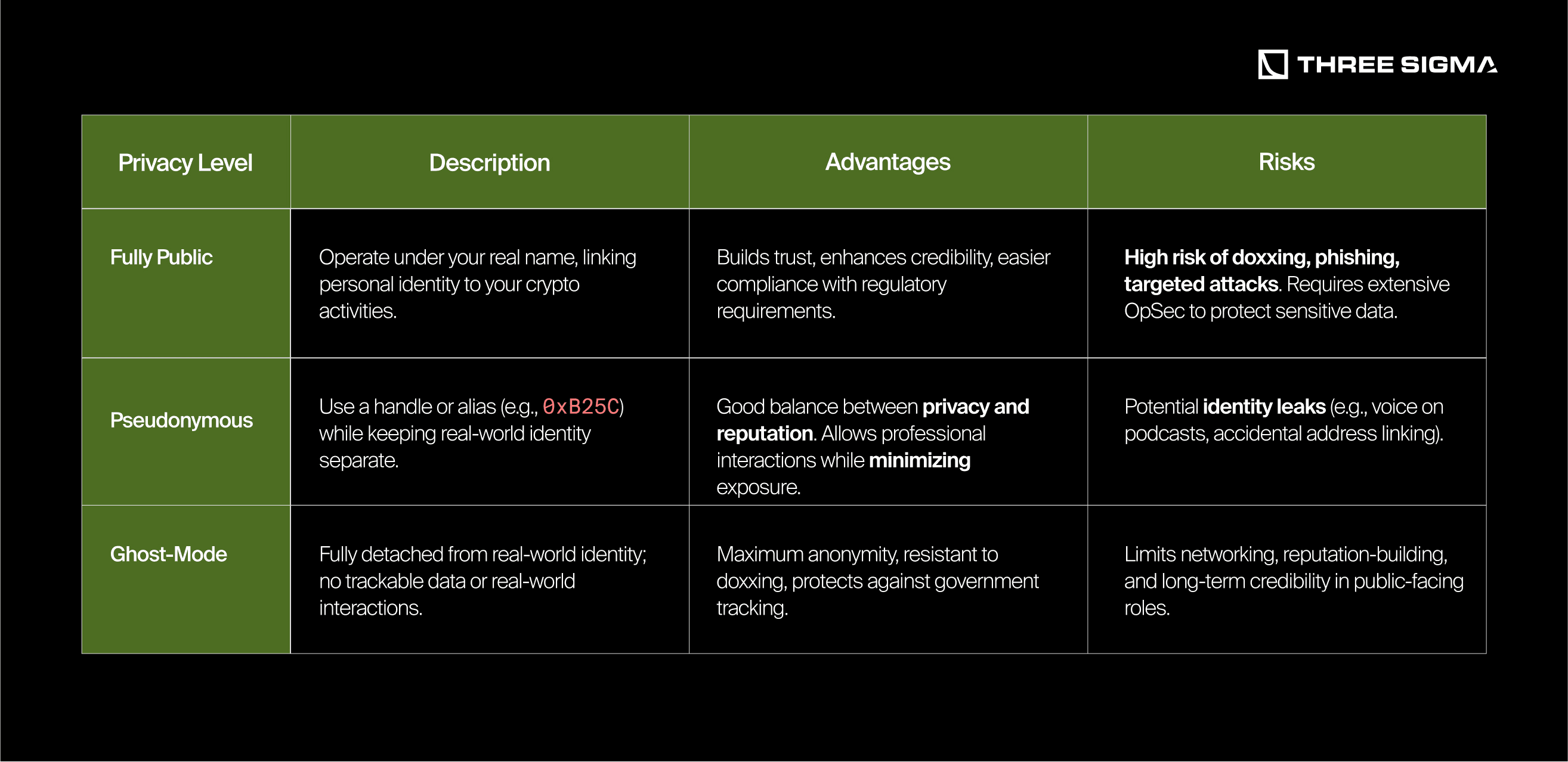
2.1 Levels of Privacy: Choosing Your Identity Model
Privacy in Web3 operates on a spectrum. The level of privacy you require depends on your threat model, your activities, and the level of public exposure you can tolerate.
Pro Tip: Even if you maintain a pseudonymous identity, transactional linkability between addresses, browsing patterns, and metadata can still reveal significant details about your behavior. Consider using privacy-enhancing technologies such as CoinJoin, zkSNARKs, or stealth addresses to minimize this risk.
2.2 Key Privacy Techniques & Defensive Measures
For those seeking stronger privacy, the following measures significantly reduce the risk of data leaks.
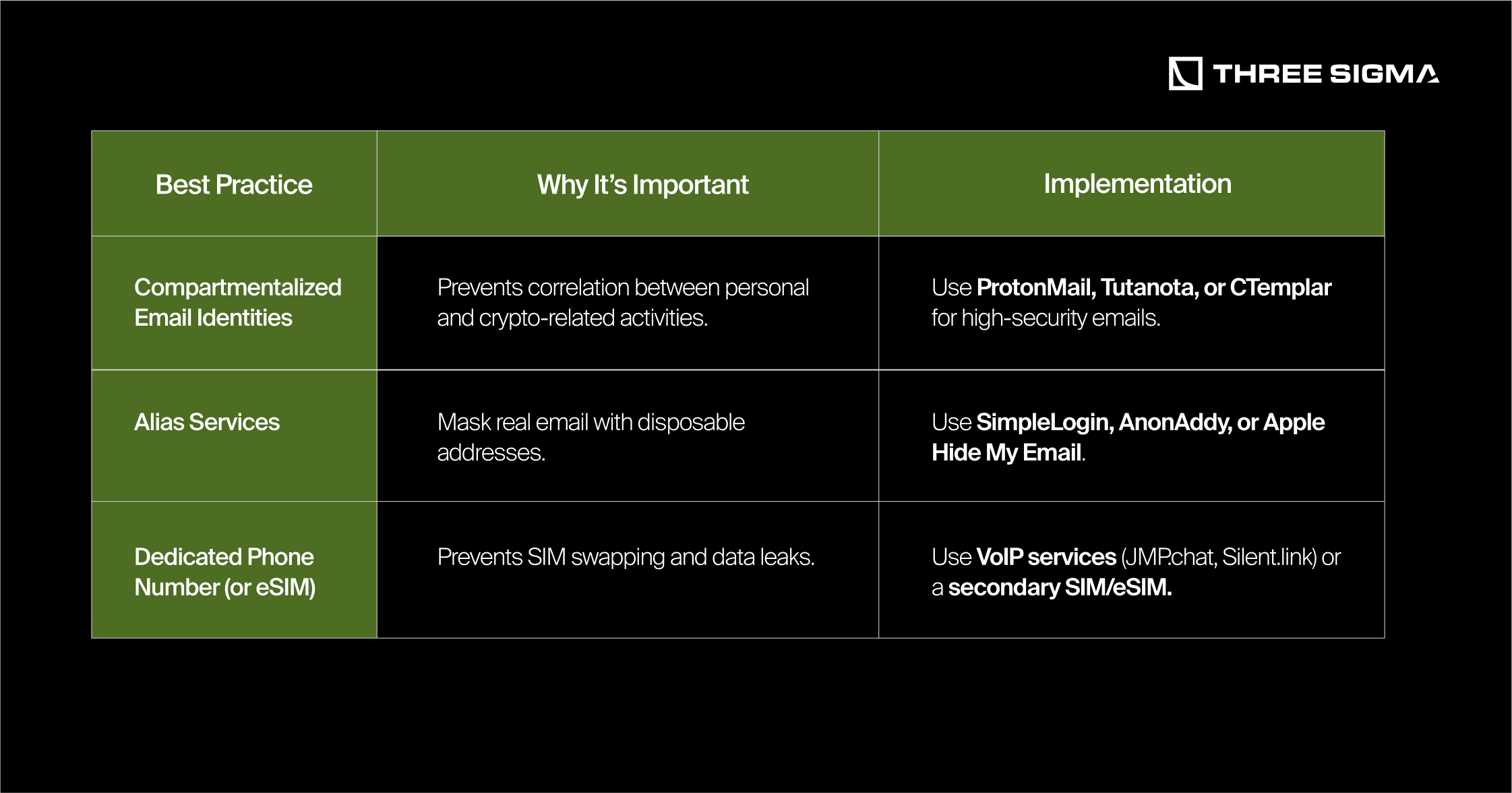
2.2.1 Separate Emails & Phone Numbers

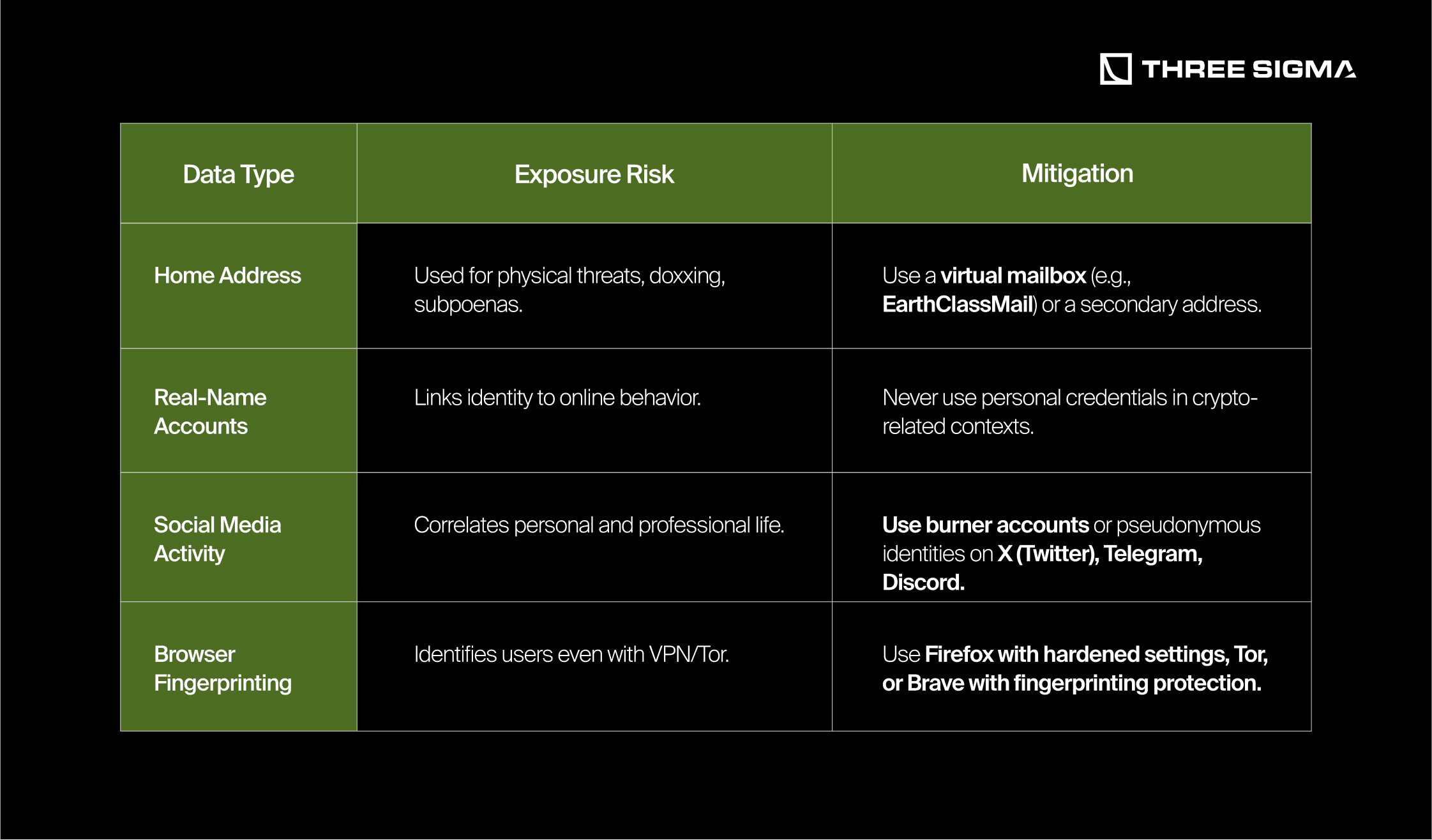
2.2.2 Minimal Personal Data Exposure
Reducing digital footprints is the foundation of strong privacy. Every account, transaction, and online interaction exposes metadata that can be aggregated, analyzed, and exploited.
Pro Tip: If you ever need to access crypto-related services with KYC requirements, consider separate devices or fresh VM instances to prevent tracking beyond that specific session.
2.2.3 Advanced Privacy Tools & Strategies
For high-level privacy, privacy-focused operating systems, encrypted communication channels, and anonymized browsing are essential.
Privacy-Focused Operating Systems
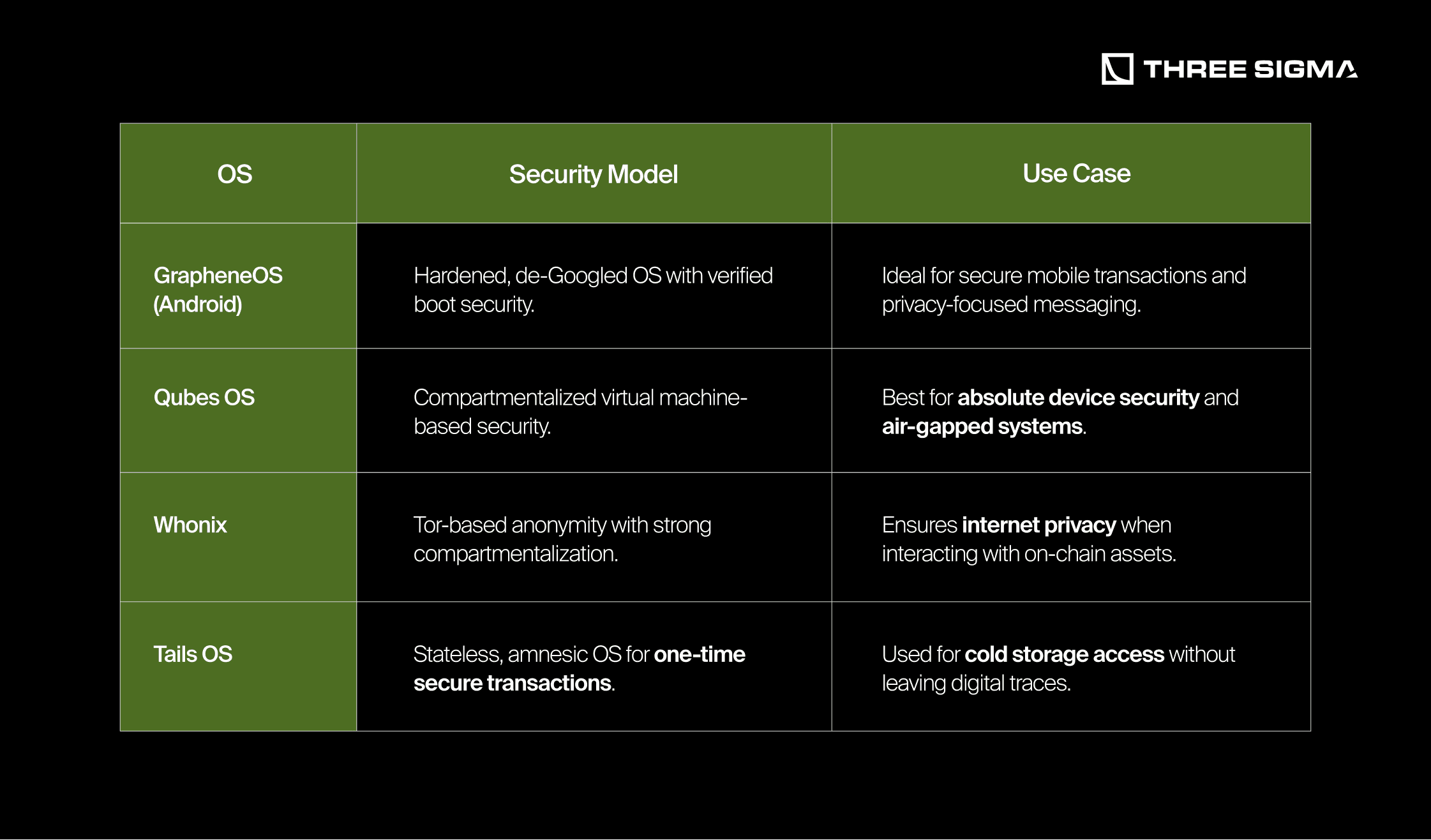
Note: Avoid stock Android or iOS devices for highly sensitive transactions. Even with privacy settings enabled, metadata leaks occur at the network level.
Anonymized Browsing & Network Security
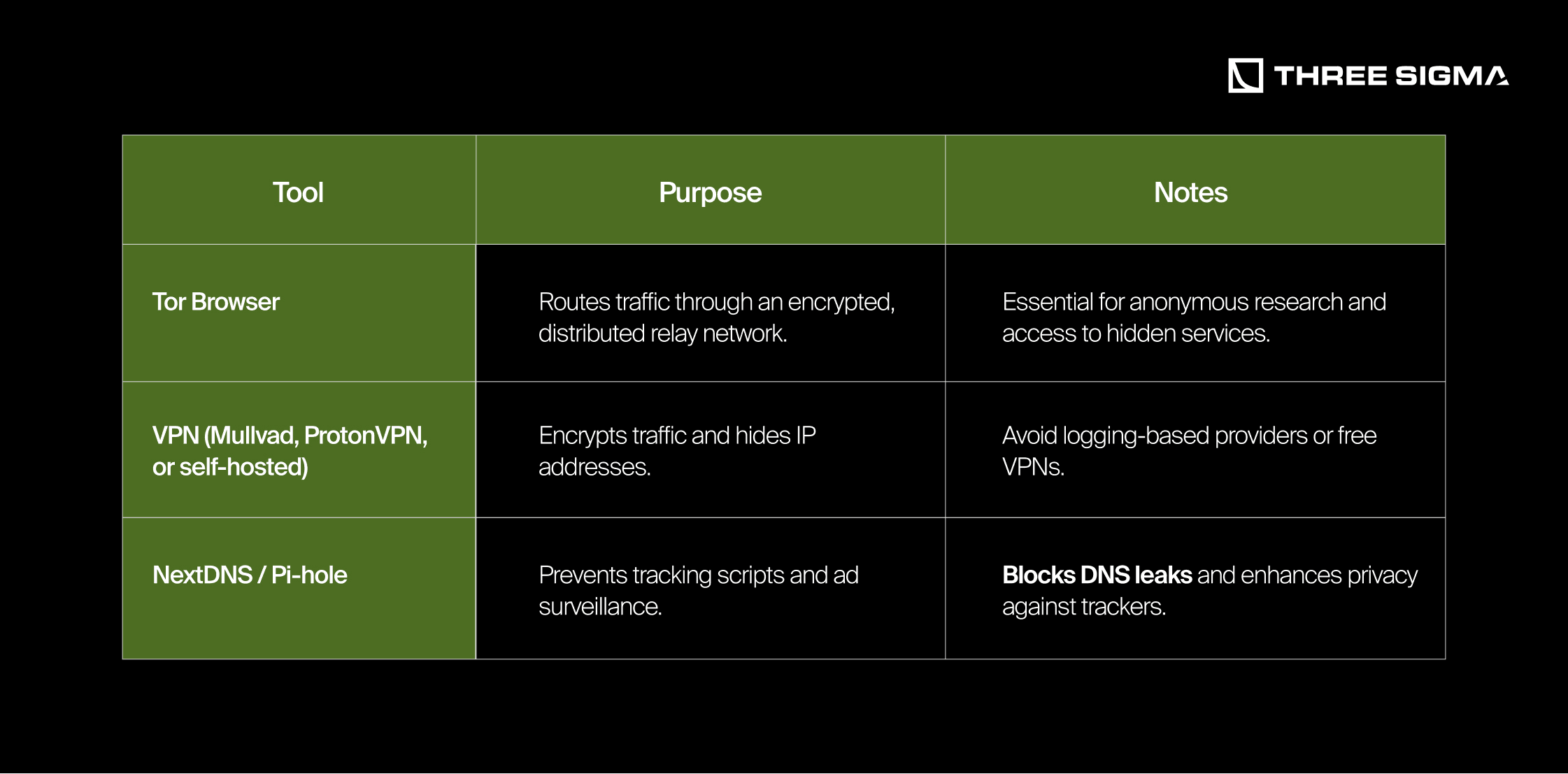
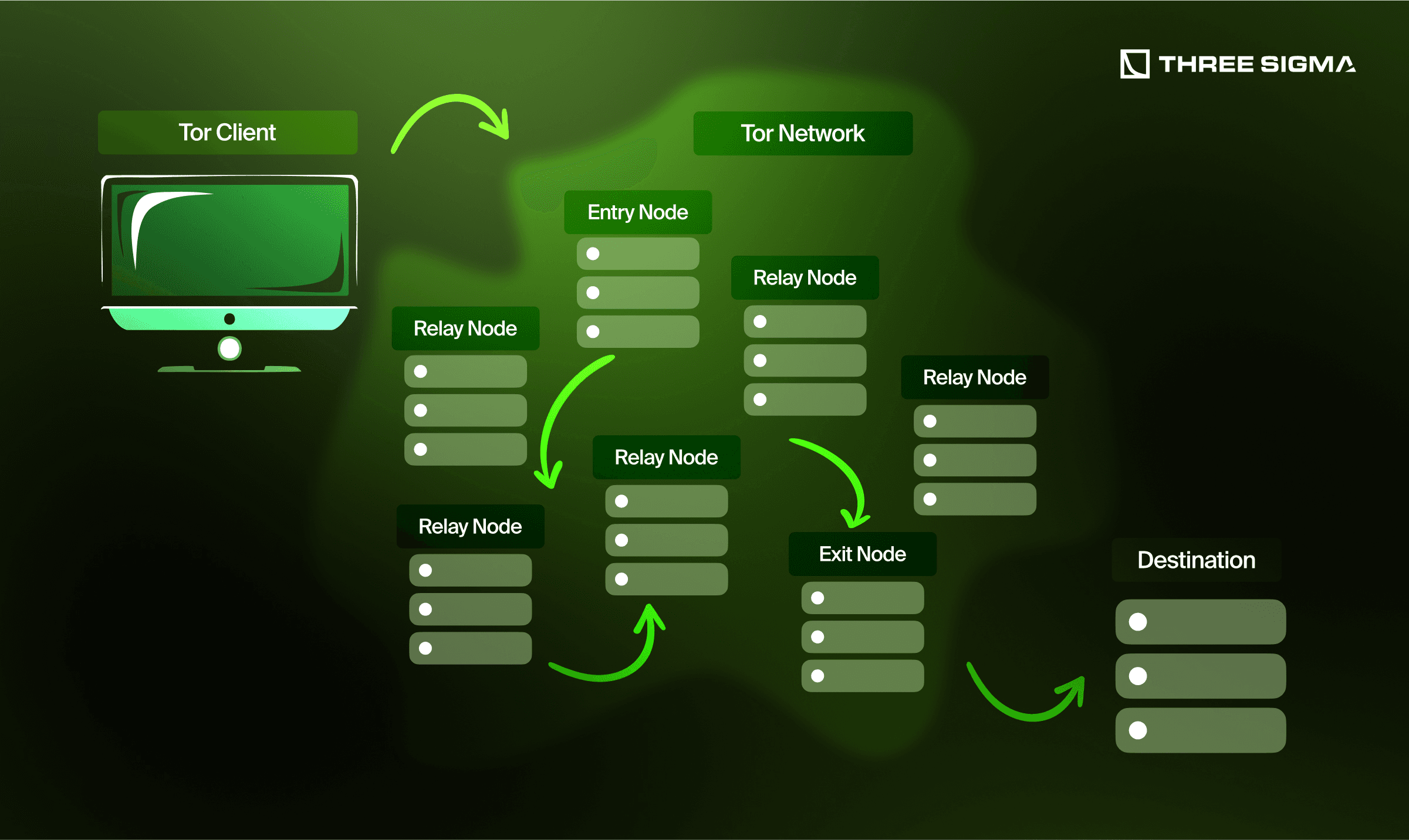
Warning: Using Tor incorrectly (e.g., logging into personal accounts) can de-anonymize you. Ensure proper OpSec when using privacy tools.
On-Chain Privacy: Minimizing Transaction Traceability
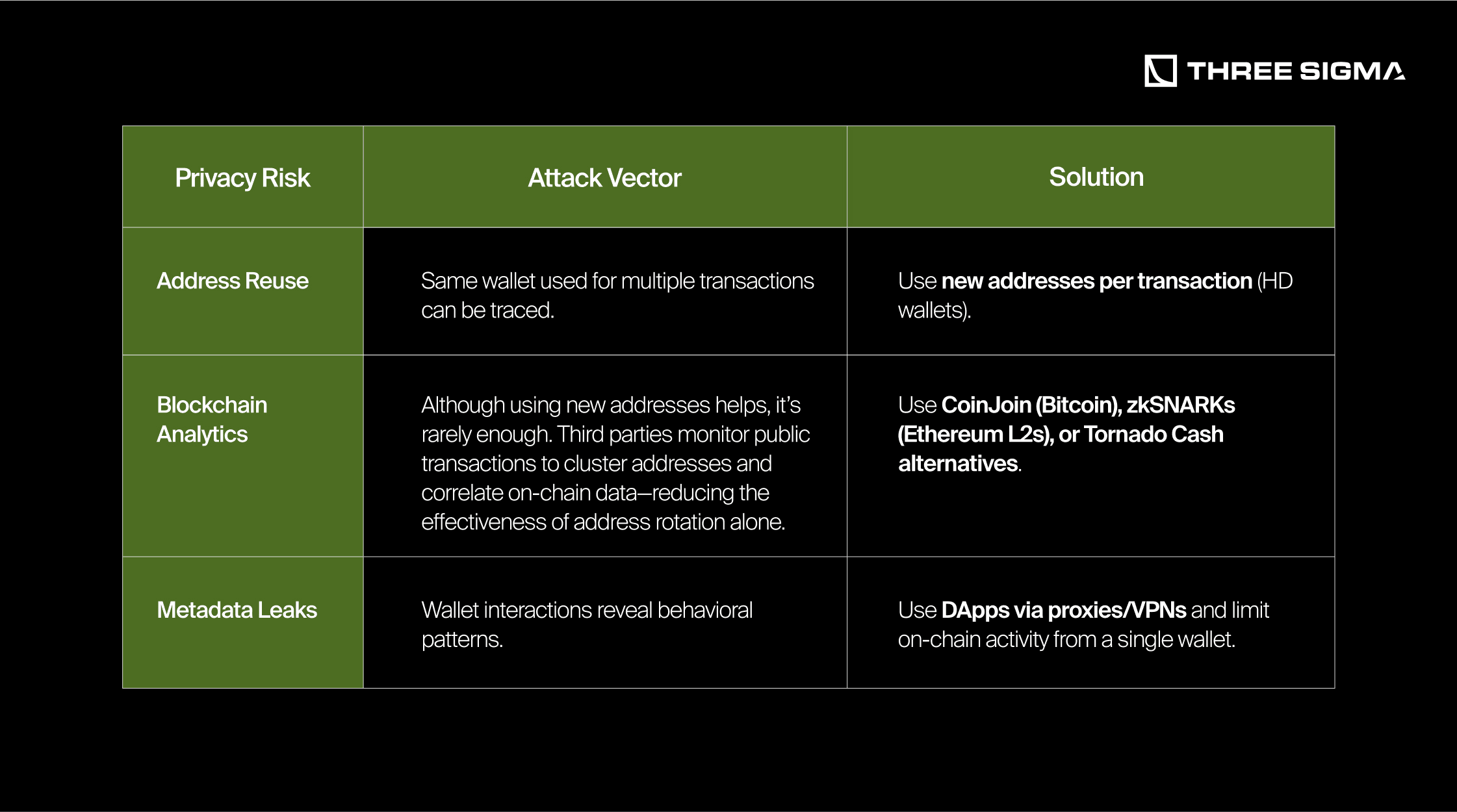
2.3 Real-World Threats & Privacy Risks
Understanding real-world privacy failures helps reinforce the importance of strong operational security.
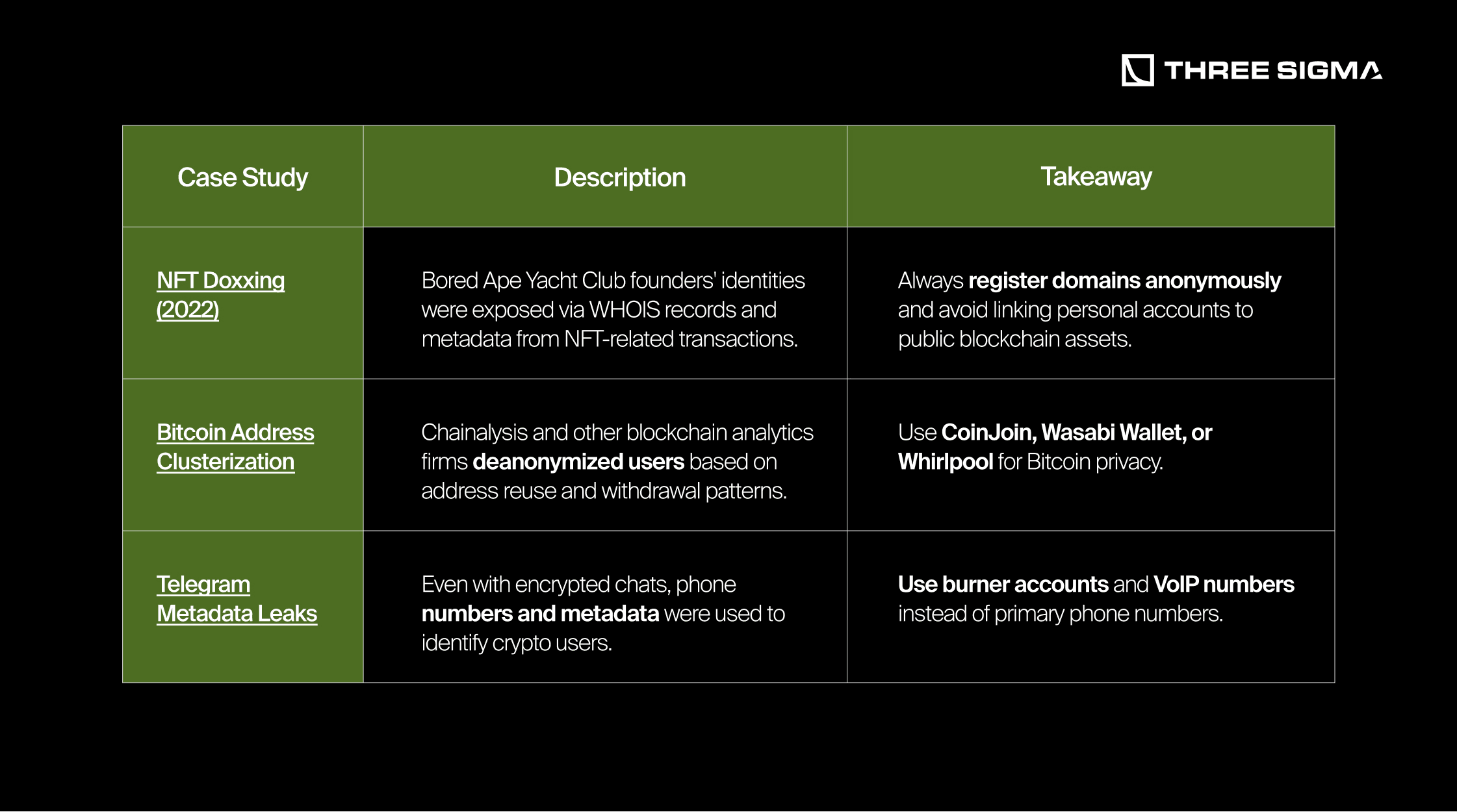
Key Takeaways
- Choose the right privacy level based on your threat model—whether fully public, pseudonymous, or completely anonymous.
- Compartmentalization is critical—never mix real-world credentials with crypto accounts.
- Use privacy-focused operating systems like GrapheneOS, Qubes OS, or Whonix for secure transactions.
- Encrypt communications and limit metadata leaks with anonymous browsing (Tor), VPNs, and private messaging apps.
- For on-chain privacy, utilize CoinJoin, stealth addresses, zk-proofs, or mixers to prevent transactional linkability.
- Assume blockchain activity is permanent—your transactions are forever visible unless proactive measures are taken.
Conclusion
By applying rigorous device security measures—dedicated machines, sandboxed environments, secure network practices, and consistent monitoring—you greatly reduce the likelihood of being caught off-guard by hidden malware, phishing links, or advanced hacking attempts. Protecting the devices that handle your crypto is every bit as important as safeguarding your private keys themselves. Remember, security in the crypto world is an ongoing process. Stay vigilant, keep your software and techniques up to date, and don’t let complacency undo all your hard work.
Ready to Take Your Security Further?
Even the best personal OpSec can’t protect an organization with weak internal practices. At Three Sigma, we offer comprehensive OpSec Audits for teams, DAOs, and protocols.
We assess:
- Key management & access controls
- Multisig governance setups
- Social engineering & insider risk
- Infrastructure attack surface
Don't wait for a breach to test your defenses.
Frequently Asked Questions (FAQ)
1. Do I really need a separate computer for crypto transactions?
Answer: Using a dedicated device (or a dedicated OS partition) cuts down on potential infection points. Mixing everyday browsing, gaming, or email with high-stakes crypto activity raises your risk of malware, phishing, or keylogging attacks.
2. What’s the benefit of using sandboxing or virtual machines?
Answer: Sandbox environments and VMs isolate suspicious files or unknown programs, preventing them from accessing or infecting your main system. It’s a simple yet powerful layer that keeps potential threats contained.
3. How do I prevent my device from being compromised through USB drives?
Answer: Avoid plugging in unknown USBs altogether. If you must use a USB drive, consider a “data blocker” and, if possible, open it only within a virtual machine or sandbox to mitigate possible malware or “Rubber Ducky” attacks.
4. Which VPN services are best for crypto security?
Answer: Look for providers with a no-logs policy and strong reputations, such as Mullvad or ProtonVPN. For even more control, host your own WireGuard or OpenVPN server if you have the technical know-how.
5. Why do I need full disk encryption if my computer is password-protected?
Answer: Passwords only protect your OS login, not the raw data on your drive. Full disk encryption ensures that if your device is stolen or lost, an attacker can’t just bypass your OS password by connecting your hard drive to another system.
6. How can I safely use public Wi-Fi if there’s no other option?
Answer: If absolutely necessary, use a trusted VPN or Tor for all traffic, and avoid logging into critical accounts or making crypto transactions. Public networks are prone to man-in-the-middle attacks and snooping.
7. Should I enable automatic updates on my crypto device?
Answer: Generally, no. It’s safer to review update notes to confirm they come from a trusted source, then manually apply them. Automatic updates can introduce risks if an attacker compromises the update channel.
8. Are privacy-focused OSes like Tails or Qubes necessary for everyday users?
Answer: They can be overkill for casual users but are invaluable if you have a high threat model or handle large amounts of crypto. Even then, the learning curve is worth it if maximum security is your priority.
9. What’s the best way to handle a lost or stolen device?
Answer: Immediately assume it’s compromised. Change all relevant passwords, revoke any wallet permissions, and move funds to a fresh wallet if possible. Full disk encryption is your best bet against data theft.
10. How often should I review or audit my device security measures?
Answer: At least a couple of times per year. Check for critical OS updates, firmware releases, and new threats. A quick routine review can catch outdated software or overlooked vulnerabilities.
From SIM swaps to compromised laptops, most attacks hit people not contracts. Our OPSEC Audit service helps crypto teams harden endpoints, isolate key material, and stay safe without slowing down workflows.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.