What is DeltaPrime in Web3? Protocol Overview
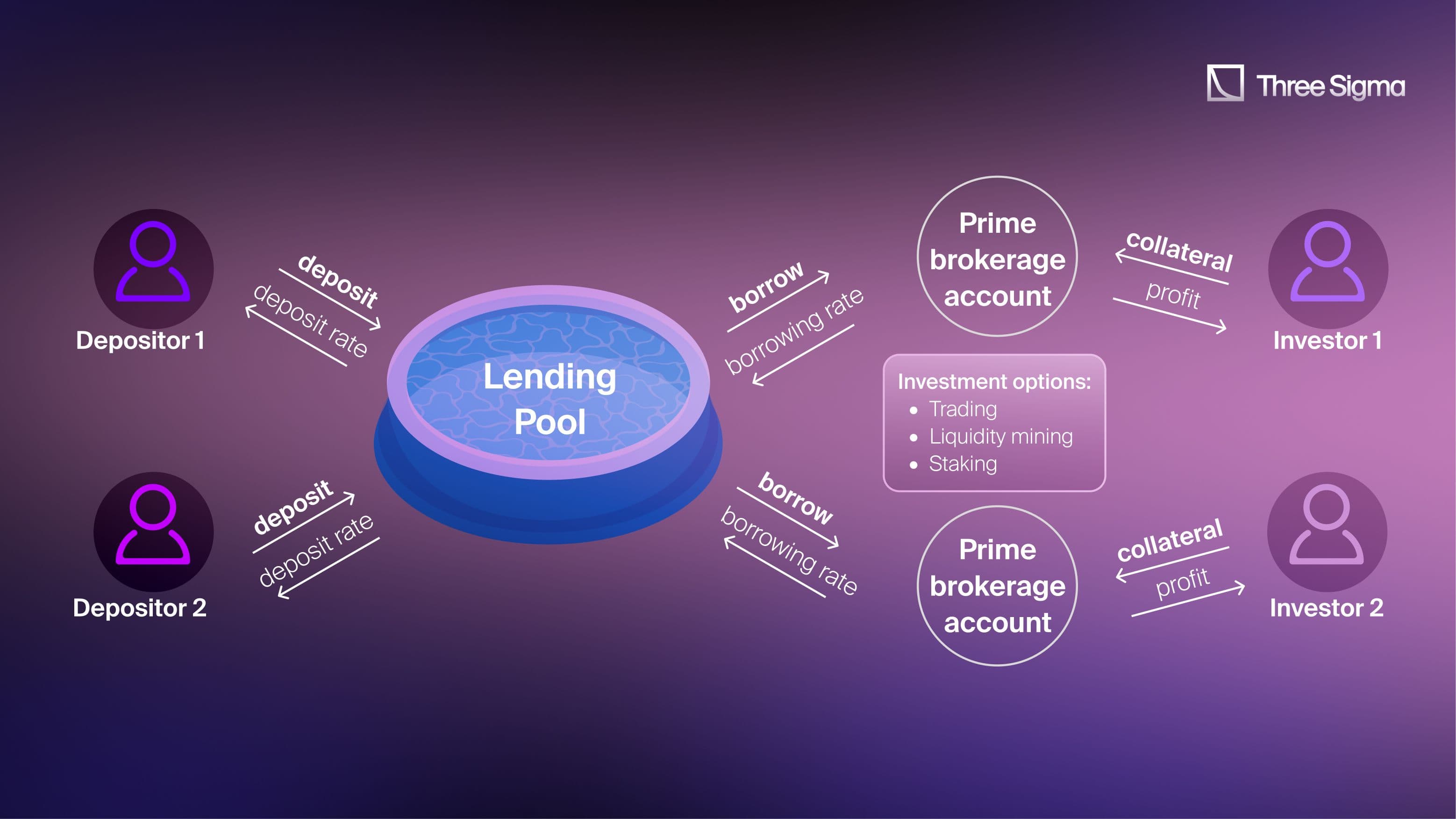
DeltaPrime is an undercollateralized lending protocol operating on the Avalanche blockchain, engineered to maximize capital efficiency through structured, trustless lending pools. The protocol allows users to deposit assets into liquidity pools and earn interest based on utilization rates. Borrowers can access these funds with partial collateral, deploying them across various DeFi platforms with integrated cross-margin capabilities.
In this section we explain what Delta Prime is, how PrimeLoans and cross-margin work, and why these mechanics mattered in the Delta Prime hack.
How DeltaPrime Operates
PrimeLoans System
At the heart of DeltaPrime lies the PrimeLoans system, which enables undercollateralized lending. Instead of directing borrowed funds straight to a user’s wallet, DeltaPrime utilizes special-purpose smart contracts called Prime Accounts to manage each loan (solidity audits help ensure their safety).
These Prime Accounts enforce strict solvency by continuously monitoring transactions to ensure asset values remain above safe thresholds. This mechanism offers borrowers a Prime Brokerage experience, enhanced with increased liquidity and cross-margin functionalities.
Solvency and Liquidation Mechanism
DeltaPrime incorporates a decentralized liquidation mechanism to maintain loan solvency. If a loan’s value-to-collateral ratio becomes precarious due to market fluctuations, anyone can trigger a partial repayment by liquidating some collateral. This process preserves the protocol’s overall risk posture by ensuring loans remain solvent.
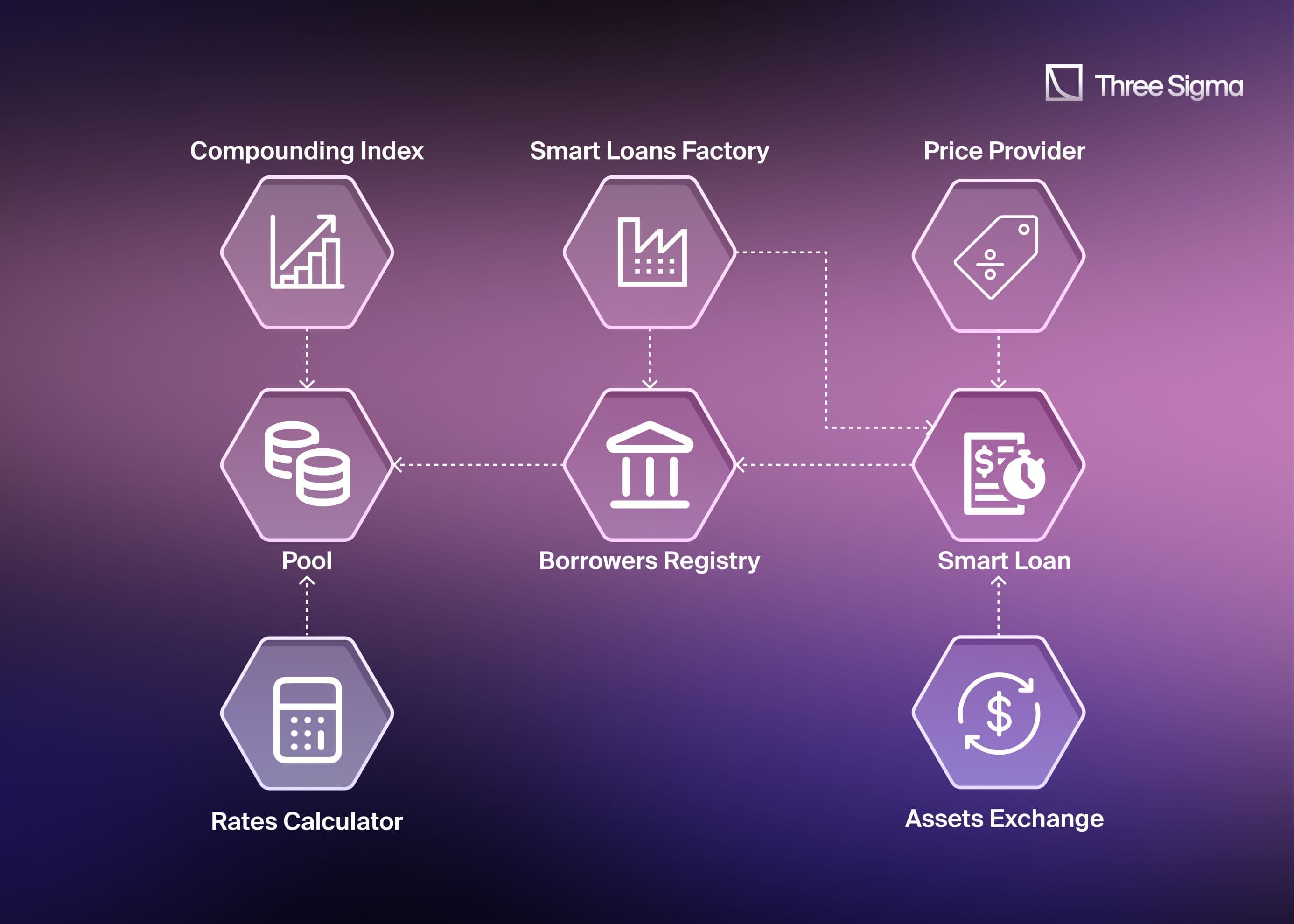
Smart Contracts Architecture
DeltaPrime's smart contracts are categorized into two primary groups:
Lending Contracts
- Pool.sol: This core contract aggregates deposits and borrowings, keeping track of user balances and liabilities. Interest is calculated in real-time through the
setRatesCalculatormodel, dynamically adjusting based on pool utilization. Only verified accounts, validated by a linked contract, can borrow. - LinearIndex.sol: A helper contract for efficient interest calculations, LinearIndex uses a global index snapshot on each user interaction, allowing O(1) balance updates to minimize gas costs.
- VariableUtilisationRatesCalculator.sol: This interest model adjusts rates based on the pool’s usage ratio, incentivizing deposits when demand is high and discouraging excessive borrowing, thus balancing capital supply and demand.
- IBorrowersRegistry.sol: This registry maintains a bidirectional mapping of borrowers, using the
canBorrowfunction to verify borrowing eligibility and ensure security.
Investment Contracts
- SmartLoan.sol: This is the main contract for loan and investment management. Key functions (
borrow,repay,invest,redeem) are safeguarded by a remainsSolvent modifier to prevent LTV from exceeding safe limits. If solvency is breached, theliquidatefunction allows anyone to sell collateral and partially repay debt, with rewards for the liquidator. Borrowers can also manage their LTV by adjusting their deposited funds (fundorwithdraw). - SmartLoansFactory.sol: A streamlined contract that facilitates loan creation and initial funding in a single transaction. It also acts as a Borrowers Registry for efficient record-keeping of active loans.
- PangolinIntermediary.sol: An exchange intermediary that enables AVAX-based asset conversions on Pangolin DEX, allowing borrowers to diversify investments through DeltaPrime’s integration with Avalanche.
Attack Analysis
On November 11, 2024, DeltaPrime faced a major security breach across the Arbitrum and Avalanche networks, resulting in a loss of approximately $4.85 million. The breach exploited two critical vulnerabilities: unchecked logic in the swapDebtParaSwap function and improper validation of the pair parameter in DeltaPrime's periphery adapter contract and reward mechanisms. These weaknesses allowed unauthorized borrowing and manipulation of reward calculations. Below is a comprehensive technical analysis of the exploit's execution, the attacker’s methodology, and its broader implications for DeltaPrime's security framework. For another cross-chain case study, see our LI.FI Protocol Exploit analysis.
Overview of the Exploit
The attacker leveraged vulnerabilities in two key functions within DeltaPrime’s smart contracts:
swapDebtParaSwapFunction- The function failed to validate the
_repayAmountparameter adequately. This allowed the attacker to redirect borrowed assets to a malicious contract without triggering repayment logic.
- The function failed to validate the
claimRewardFunction- The vulnerability arose from insufficient validation of the
pairparameter. This flaw allowed the attacker to pass a malicious contract as input, manipulate internal balances, and withdraw unearned rewards.
- The vulnerability arose from insufficient validation of the
These weaknesses enabled the attacker to siphon significant funds across multiple liquidity pools.
Detailed Breakdown of the Attack
Step 1: Flash Loan Acquisition
The attack began with the acquisition of a flash loan totaling approximately 59.958 WETH, providing the attacker with temporary liquidity to execute subsequent steps.

Step 2: Exploiting swapDebtParaSwap Function
The root cause of the exploit lies in unchecked input validation in the swapDebtParaSwap function and arbitrary external contract input in the claimReward function. These flaws allowed the attacker to borrow assets exceeding their collateral and withdraw collateral as rewards without proper validation.
- The
_repayAmountparameter was not validated before being passed to theswapAdapter. As a result, borrowed WBTC was transferred out of the attacker’s account to a malicious contract (0x52ee). - The attacker leveraged 59.9 ETH as collateral to borrow 1.18 WBTC, then used the
swapAdapterto transfer the borrowed WBTC to a separate address without triggering a repayment check.
This loophole allowed the attacker to bypass standard repayment logic and redirect funds for malicious purposes.

Step 3: Exploiting the claimReward Function
The second vulnerability stemmed from inadequate validation of the pair parameter within the claimReward() function. This weakness allowed the attacker to exploit DeltaPrime's reward system.
- Within the
TraderJoeV2ArbitrumFacetcontract, thepairparameter, used in the reward claim mechanism, was not properly validated. The attacker passed a malicious contract as input. - The malicious contract exploited the
wrapNativeToken()function to convert collateral (ETH) into WETH. This process disrupted DeltaPrime’s internal balance calculations, causing the system to interpret the wrapped ETH as valid reward assets. - By leveraging this flaw, the attacker manipulated the reward system, resulting in an erroneous payout of 59.9 ETH.
This step highlights the risks posed by weak parameter validation, as the absence of safeguards allowed the protocol's internal balance tracking to be exploited.

Step 4: Post-Exploit Asset Distribution
After successfully siphoning off approximately $4.85 million, the attacker employed a distinctive strategy for managing stolen assets. Instead of quickly dispersing the funds or laundering them through traditional means, they strategically reinvested the stolen funds into various DeFi protocols on Avalanche to generate passive income.
While many exploiters typically try to quickly launder or disperse stolen funds, this attacker took an unconventional approach by turning the stolen funds into an opportunity for yield generation on Avalanche.
How the Attack Could Have Been Prevented? (Lessons from an Arbitrum audit)
An Arbitrum audit of Delta Prime would have flagged stricter input validation for swapDebtParaSwap and claimReward (including range checks for _repayAmount and ownership checks for pair) to protect reward distribution integrity and block this abuse path. Parameters such as _repayAmount and pair must be thoroughly checked against valid ranges and ownership criteria.
This meticulous validation is essential for maintaining the integrity of the reward mechanism and safeguarding the protocol against malicious actors attempting to manipulate reward distributions. Independent dapp security audit and targeted mechanism design review help surface unsafe parameterization and reward logic before mainnet.
Consequences
The immediate consequence of the DeltaPrime attack was the loss of approximately $4.85 million across the Arbitrum and Avalanche networks. As this is the second significant breach within two months, it could have negatively affected user trust and the protocol's reputation. Such incidents may lead users to reassess the security of DeltaPrime, potentially resulting in decreased engagement and confidence. Rapid Crypto Incident Response & Exploit Recovery can help contain damage, coordinate communications, and accelerate remediation.
The DeltaPrime Protocol Response
As an immediate precautionary measure, DeltaPrime has paused all pools on both chains to contain the risk. The team has assured users that they will provide updates as soon as possible, emphasizing their commitment to safeguarding user assets and restoring the protocol's functionality. For builders, here’s why security in early-stage Web3 projects pays off long before incidents occur.
DeltaPrime’s loss stemmed from cross-chain logic interacting with DeFi primitives under different conditions. Our Smart Contract Audit service goes beyond EVM correctness. We test assumptions across networks, oracles, and economic boundaries.
Conclusion
The DeltaPrime hack shows how cross-chain assumptions break under pressure. If you’re deploying on Avalanche or Arbitrum, tighten your reward logic, validate parameters, and complete your Arbitrum audit before going live. Understanding what DeltaPrime is in Web3, how it works and how its moving parts failed here, helps teams avoid the next $4.85M lesson.
Addresses
Arbitrum Addresses
- Attacker Address on Arbitrum:
- Attack Contract on Arbitrum:
- First Blood on Arbitrum:
- Recipient Addresses on Arbitrum:
- 0x56e7f67211683857EE31a1220827cac5cdaa634C (49.91 ETH)
- 0x101723dEf8695f5bb8D5d4AA70869c10b5Ff6340 (16.62 ETH)
- 0x21032a57bb6cfed765b7b5543fe00a3831b1325dacd3c42b6e98db033da8f5da (2.96 WBTC bridged to Ethereum)
Avalanche Addresses
- Attacker Addresses on Avalanche:
- First Avalanche Strike:
- Stolen Funds on Avalanche:
- 0xd5381c683191EB0999a51567274abAB73a9Df0AD (465.35 AVAX)
- 0xd3d535141831F6Bd8B7DF92E2AE0463D60Af2413 (69,401 AVAX)

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.