Introduction
In the rapidly evolving world of decentralized finance (DeFi), blockchain security has become more crucial than ever. The DeFi ecosystem has experienced exponential growth, with billions of dollars locked in smart contracts across various platforms. However, this expansion has also made it a lucrative target for cybercriminals. In 2024, blockchain-related hacks resulted in staggering losses of approximately $730 million, highlighting persistent vulnerabilities within smart contracts and blockchain protocols.While this figure marks a decrease from the 1.15 billion lost in 2023, the sophistication and frequency of attacks have intensified. Hackers are employing advanced techniques to exploit flaws in projects. These incidents not only lead to significant financial losses but also undermine trust in the DeFi ecosystem.In this article, we position the attack vectors based on the number of incidents each type experienced in 2024, highlighting the most prevalent threats first. We explore the most significant attack vectors exploited in 2024, delving into case studies of some of the largest blockchain breaches. We analyze how these attacks were carried out, the specific vulnerabilities targeted, and the profound impacts on the affected platforms. By examining these incidents, we aim to uncover critical lessons and best practices that can enhance blockchain security moving forward.Whether you're a developer, investor, or user in the DeFi space, understanding these exploits is essential. Learning from past incidents equips the community with the knowledge to implement stronger security measures, protect assets, and contribute to a more resilient decentralized financial infrastructure. For teams building DeFi protocols on Ethereum and other EVM chains, a dedicated Solidity audit can help identify and fix many of these vulnerabilities before they are exploited. For Solana-based teams, a Rust Smart Contract Audit helps validate program logic and reduce the same classes of failure.

Most Exploited DeFi Vulnerabilities - Ecosystem
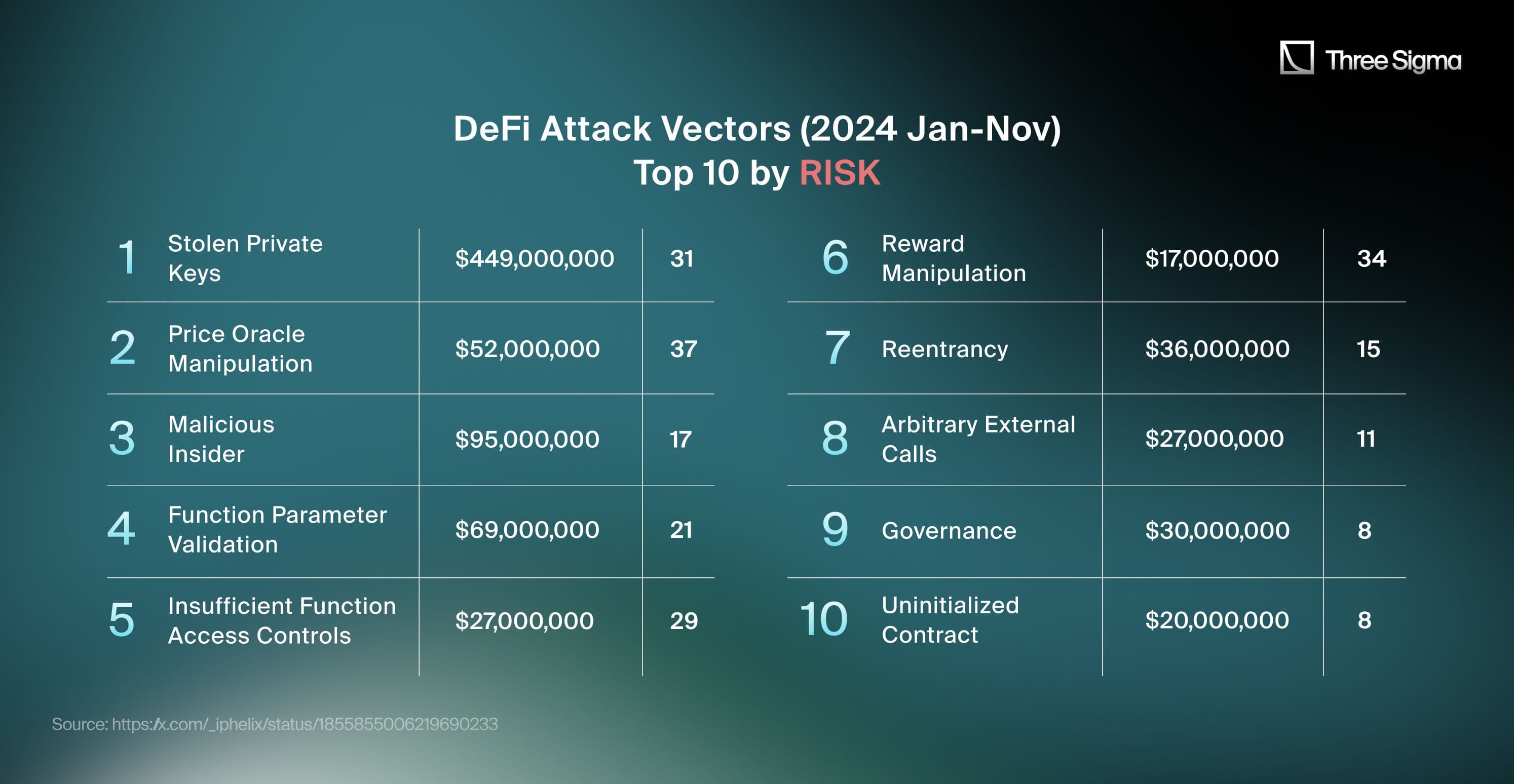
1. Stolen Private Keys

Stolen private keys emerged as the most damaging attack vector in 2024, accounting for a staggering $449 million in losses across 31 separate incidents. This attack method bypasses protocol security measures by directly targeting private keys, the cryptographic linchpin that grants full access to cryptocurrency assets.
How Stolen Private Key Hacks Happen

Case Study: DMM Bitcoin Hack
- Date: May 2024
- Amount Lost: $305 million
- Blockchain: Bitcoin
- Attack Vector: Private key compromise
Overview:DMM Bitcoin, a centralized cryptocurrency exchange, experienced one of the largest crypto hacks in recent history, resulting in a loss of $305 million. The incident involved the unauthorized transfer of 4502.9 BTC from the exchange’s wallets. While the exchange has not disclosed the root cause of the breach, the attack likely stemmed from a private key compromise, enabling the attacker to initiate unauthorized transfers.Steps of the Attack:
- Large Bitcoin Transfer Detected:A significant transfer of 4502.9 BTC to an unknown wallet raised initial alarms. The distribution of funds to multiple addresses complicated efforts to track the stolen assets.
- Private Key Compromise Suspected: It is speculated that the attacker gained access to private keys through either:Internal Mismanagement: Hot wallet keys might have been exposed. External Breach: Phishing attacks or malware targeting employees managing the wallets.
- Lack of Multi-Signature Wallets:The absence of multi-signature wallets for high-value accounts likely exacerbated the situation, allowing a single key compromise to result in significant losses.
- Exchange Response:DMM Bitcoin paused certain services and assured customers of secured deposits. The exchange provided limited transparency regarding the investigation's findings, leaving some uncertainty around the exact vulnerabilities exploited.
Root Cause:While the exact details remain undisclosed, the attack underscores the vulnerabilities associated with centralized management of private keys, especially in the absence of multi-signature wallets and robust credential security.
How to Mitigate Private Key Compromises

Lessons Learned
The DMM Bitcoin hack emphasizes the importance of robust private key security for centralized exchanges. As attackers grow increasingly sophisticated, exchanges must prioritize advanced security measures like multi-signature wallets, cold storage, and employee training. Transparency during post-incident reporting is also crucial for restoring user trust and preventing future incidents.
For a detailed analysis of the DMM Bitcoin exploit, read the detailed report.
2. Price Oracle Manipulation

Price oracle manipulation attacks ranked as the second most damaging attack vector in 2024, accounting for $52 million in losses across 37 incidents. These exploits leverage weaknesses in price oracles to manipulate asset values, resulting in undercollateralized loans, liquidity pool drains, and arbitrage opportunities that destabilize DeFi ecosystems.
How Price Oracle Manipulation Attacks Work

Case Study: Polter Finance Exploit
- Date: November 16, 2024
- Amount Lost: $12 million
- Blockchain: Fantom
- Attack Vector: Price oracle manipulation through liquidity pools.
Overview:Polter Finance, a decentralized lending protocol, fell victim to a price manipulation attack when an attacker exploited its reliance on SpookySwap’s liquidity pools for the BOO token price. By leveraging flash loans, the attacker artificially inflated the token’s price, enabling them to borrow far more than the collateral was worth.Steps of the Attack:
- Flash Loan Initiation:The attacker borrowed significant BOO token amounts, depleting liquidity from SpookySwap V2 and V3 pools. This caused the Automated Market Maker (AMM) formula to calculate an artificially inflated BOO price.
- Collateral Deposit:The attacker deposited a minimal amount of BOO as collateral. The manipulated price resulted in an inflated collateral valuation of $1.37 trillion.
- Overleveraged Borrowing:Using the falsely high collateral value, the attacker borrowed large amounts of other assets.
- Repayment and Profit:Flash loans were repaid, and the attacker retained the borrowed funds, draining Polter Finance's liquidity pools.
Root Cause:The ChainlinkUniV2Adapter oracle failed to validate the BOO token price against historical data or implement checks for extreme price deviations, leaving the protocol vulnerable to manipulation.
How to Mitigate Price Oracle Manipulation
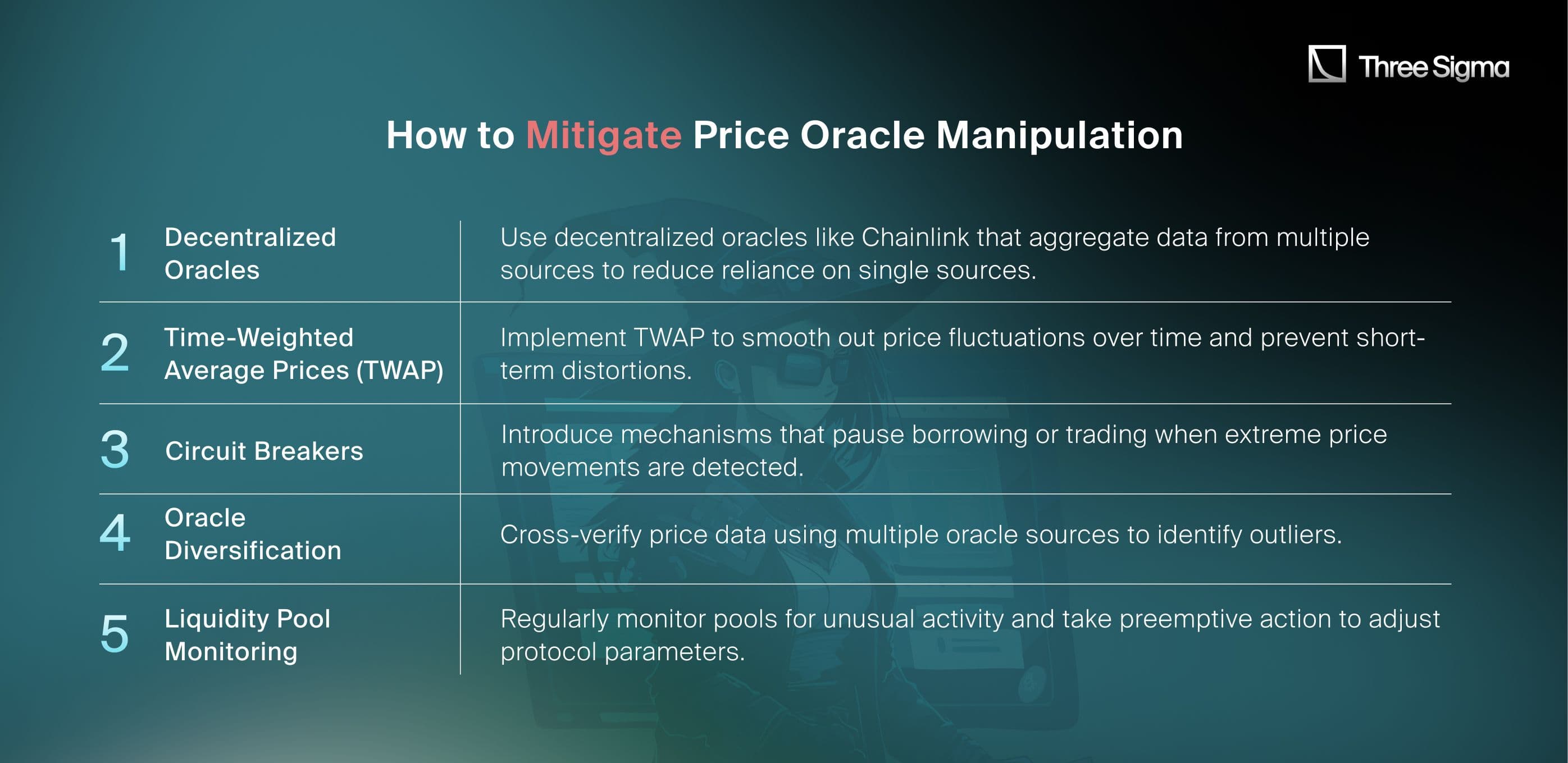
Lessons Learned
The Polter Finance exploit demonstrates the importance of robust oracle systems in safeguarding DeFi protocols. Single-source oracles and the lack of mechanisms to detect sudden price changes leave platforms vulnerable to manipulation. Moving forward, protocols must prioritize oracle diversification, implement TWAPs, and conduct independent security audits to avoid similar exploits.
For a detailed analysis of the Polter Finance exploit, read the detailed report.
3. Malicious Insider

Malicious insider attacks emerged as the third most critical threat vector in 2024, resulting in $95 million in losses across 17 incidents. These attacks involve individuals with authorized access exploiting their privileges to manipulate protocols, steal funds, or disrupt operations. In the DeFi ecosystem, insiders leverage their intimate knowledge of smart contracts and platform vulnerabilities to execute sophisticated exploits, undermining trust and stability within the ecosystem.
How Malicious Insider Attacks Work

Case Study: HAWK Crash

- Date: December 4-5, 2024
- Amount Lost: Approximately $95 million
- Blockchain: Solana
- Attack Vector: Insider manipulation and pump-and-dump scheme.
Overview:The HAWK crash involved the rapid depreciation of the HAWK memecoin, launched by influencer Hailey Welch. Initially achieving a market capitalization of nearly $500 million, the token’s value plummeted by over 90% within hours. Investigations revealed that a significant portion of the token supply was controlled by insiders and sniper bots, facilitating a coordinated pump-and-dump scheme that devastated retail investors.Steps of the Attack:
- Token Launch and Initial Pump:Hailey Welch launched the HAWK token on the Solana blockchain, leveraging her viral social media presence to attract substantial investment. The token quickly reached a market capitalization of approximately $500 million within minutes of launch, driven by hype and strategic marketing.
- Insider and Sniper Coordination:Between 80% and 90% of the HAWK supply was acquired by insiders and sniper bots immediately after launch. These entities, having significant holdings, were positioned to execute large-scale sell-offs once the token price peaked.
- Rapid Sell-Off and Price Crash:Within 20 minutes, insider wallets began selling large quantities of HAWK tokens, flooding the market and causing the price to crash from $0.04916 to $0.002439. The sudden increase in supply and decrease in demand led to a dramatic loss in market capitalization, wiping out approximately $95 million in value.
- Aftermath and Investor Impact:Retail investors faced substantial losses, with some reporting losses of up to $43,000. The crash triggered regulatory scrutiny and legal actions, with law firms like Burwick Law offering services to affected investors and discussions about potential SEC involvement.
Root Cause:The HAWK crash was primarily driven by the concentration of token supply in the hands of insiders and automated sniper bots. The lack of adequate distribution mechanisms and safeguards allowed these entities to manipulate the market, executing a coordinated pump-and-dump scheme that exploited investor trust and market dynamics.
How to Mitigate Malicious Insider Attacks

4. Function Parameter Validation

Article
ReplySee new posts
Conversation
Three Sigma@threesigmaxyzPromote2024 Exploits Recap: Top 10 Most Exploited DeFi Vulnerabilities and How to Prevent Them11346.4KStolen keys, hacked oracles, and millions lost! 2024's DeFi exploits revealed shocking vulnerabilities. Why did these attacks work, and what can be done to prevent them? 🕵️
Introduction
In the rapidly evolving world of decentralized finance (DeFi), blockchain security has become more crucial than ever. The DeFi ecosystem has experienced exponential growth, with billions of dollars locked in smart contracts across various platforms. However, this expansion has also made it a lucrative target for cybercriminals. In 2024, blockchain-related hacks resulted in staggering losses of approximately $730 million, highlighting persistent vulnerabilities within smart contracts and blockchain protocols.While this figure marks a decrease from the $1.15 billion lost in 2023, the sophistication and frequency of attacks have intensified. Hackers are employing advanced techniques to exploit flaws in projects. These incidents not only lead to significant financial losses but also undermine trust in the DeFi ecosystem.In this article, we position the attack vectors based on the number of incidents each type experienced in 2024, highlighting the most prevalent threats first. We explore the most significant attack vectors exploited in 2024, delving into case studies of some of the largest blockchain breaches. We analyze how these attacks were carried out, the specific vulnerabilities targeted, and the profound impacts on the affected platforms. By examining these incidents, we aim to uncover critical lessons and best practices that can enhance blockchain security moving forward.Whether you're a developer, investor, or user in the DeFi space, understanding these exploits is essential. Learning from past incidents equips the community with the knowledge to implement stronger security measures, protect assets, and contribute to a more resilient decentralized financial infrastructure.
1. Stolen Private Keys
Stolen private keys emerged as the most damaging attack vector in 2024, accounting for a staggering $449 million in losses across 31 separate incidents. This attack method bypasses protocol security measures by directly targeting private keys, the cryptographic linchpin that grants full access to cryptocurrency assets.
How Stolen Private Key Hacks Happen
Case Study: DMM Bitcoin Hack
- Date: May 2024
- Amount Lost: $305 million
- Blockchain: Bitcoin
- Attack Vector: Private key compromise
Overview:DMM Bitcoin, a centralized cryptocurrency exchange, experienced one of the largest crypto hacks in recent history, resulting in a loss of $305 million. The incident involved the unauthorized transfer of 4502.9 BTC from the exchange’s wallets. While the exchange has not disclosed the root cause of the breach, the attack likely stemmed from a private key compromise, enabling the attacker to initiate unauthorized transfers.Steps of the Attack:
- Large Bitcoin Transfer Detected:A significant transfer of 4502.9 BTC to an unknown wallet raised initial alarms. The distribution of funds to multiple addresses complicated efforts to track the stolen assets.
- Private Key Compromise Suspected: It is speculated that the attacker gained access to private keys through either:Internal Mismanagement: Hot wallet keys might have been exposed. External Breach: Phishing attacks or malware targeting employees managing the wallets.
- Lack of Multi-Signature Wallets:The absence of multi-signature wallets for high-value accounts likely exacerbated the situation, allowing a single key compromise to result in significant losses.
- Exchange Response:DMM Bitcoin paused certain services and assured customers of secured deposits. The exchange provided limited transparency regarding the investigation's findings, leaving some uncertainty around the exact vulnerabilities exploited.
Root Cause:While the exact details remain undisclosed, the attack underscores the vulnerabilities associated with centralized management of private keys, especially in the absence of multi-signature wallets and robust credential security.
How to Mitigate Private Key Compromises
Lessons Learned
The DMM Bitcoin hack emphasizes the importance of robust private key security for centralized exchanges. As attackers grow increasingly sophisticated, exchanges must prioritize advanced security measures like multi-signature wallets, cold storage, and employee training. Transparency during post-incident reporting is also crucial for restoring user trust and preventing future incidents.
For a detailed analysis of the DMM Bitcoin exploit, read the detailed report.
2. Price Oracle Manipulation
Price oracle manipulation attacks ranked as the second most damaging attack vector in 2024, accounting for $52 million in losses across 37 incidents. These exploits leverage weaknesses in price oracles to manipulate asset values, resulting in undercollateralized loans, liquidity pool drains, and arbitrage opportunities that destabilize DeFi ecosystems.
How Price Oracle Manipulation Attacks Work
Case Study: Polter Finance Exploit
- Date: November 16, 2024
- Amount Lost: $12 million
- Blockchain: Fantom
- Attack Vector: Price oracle manipulation through liquidity pools.
Overview:Polter Finance, a decentralized lending protocol, fell victim to a price manipulation attack when an attacker exploited its reliance on SpookySwap’s liquidity pools for the BOO token price. By leveraging flash loans, the attacker artificially inflated the token’s price, enabling them to borrow far more than the collateral was worth.Steps of the Attack:
- Flash Loan Initiation:The attacker borrowed significant BOO token amounts, depleting liquidity from SpookySwap V2 and V3 pools. This caused the Automated Market Maker (AMM) formula to calculate an artificially inflated BOO price.
- Collateral Deposit:The attacker deposited a minimal amount of BOO as collateral. The manipulated price resulted in an inflated collateral valuation of $1.37 trillion.
- Overleveraged Borrowing:Using the falsely high collateral value, the attacker borrowed large amounts of other assets.
- Repayment and Profit:Flash loans were repaid, and the attacker retained the borrowed funds, draining Polter Finance's liquidity pools.
Root Cause:The ChainlinkUniV2Adapter oracle failed to validate the BOO token price against historical data or implement checks for extreme price deviations, leaving the protocol vulnerable to manipulation.
How to Mitigate Price Oracle Manipulation
Lessons Learned
The Polter Finance exploit demonstrates the importance of robust oracle systems in safeguarding DeFi protocols. Single-source oracles and the lack of mechanisms to detect sudden price changes leave platforms vulnerable to manipulation. Moving forward, protocols must prioritize oracle diversification, implement TWAPs, and conduct independent security audits to avoid similar exploits.
For a detailed analysis of the Polter Finance exploit, read the detailed report.
3. Malicious Insider
Malicious insider attacks emerged as the third most critical threat vector in 2024, resulting in $95 million in losses across 17 incidents. These attacks involve individuals with authorized access exploiting their privileges to manipulate protocols, steal funds, or disrupt operations. In the DeFi ecosystem, insiders leverage their intimate knowledge of smart contracts and platform vulnerabilities to execute sophisticated exploits, undermining trust and stability within the ecosystem.
How Malicious Insider Attacks Work
Case Study: HAWK Crash
- Date: December 4-5, 2024
- Amount Lost: Approximately $95 million
- Blockchain: Solana
- Attack Vector: Insider manipulation and pump-and-dump scheme.
Overview:The HAWK crash involved the rapid depreciation of the HAWK memecoin, launched by influencer Hailey Welch. Initially achieving a market capitalization of nearly $500 million, the token’s value plummeted by over 90% within hours. Investigations revealed that a significant portion of the token supply was controlled by insiders and sniper bots, facilitating a coordinated pump-and-dump scheme that devastated retail investors.Steps of the Attack:
- Token Launch and Initial Pump:Hailey Welch launched the HAWK token on the Solana blockchain, leveraging her viral social media presence to attract substantial investment. The token quickly reached a market capitalization of approximately $500 million within minutes of launch, driven by hype and strategic marketing.
- Insider and Sniper Coordination:Between 80% and 90% of the HAWK supply was acquired by insiders and sniper bots immediately after launch. These entities, having significant holdings, were positioned to execute large-scale sell-offs once the token price peaked.
- Rapid Sell-Off and Price Crash:Within 20 minutes, insider wallets began selling large quantities of HAWK tokens, flooding the market and causing the price to crash from $0.04916 to $0.002439. The sudden increase in supply and decrease in demand led to a dramatic loss in market capitalization, wiping out approximately $95 million in value.
- Aftermath and Investor Impact:Retail investors faced substantial losses, with some reporting losses of up to $43,000. The crash triggered regulatory scrutiny and legal actions, with law firms like Burwick Law offering services to affected investors and discussions about potential SEC involvement.
Root Cause:The HAWK crash was primarily driven by the concentration of token supply in the hands of insiders and automated sniper bots. The lack of adequate distribution mechanisms and safeguards allowed these entities to manipulate the market, executing a coordinated pump-and-dump scheme that exploited investor trust and market dynamics.
How to Mitigate Malicious Insider Attacks

4. Function Parameter Validation

Improper function parameter validation emerged as a significant attack vector in 2024, exposing protocols to exploits that bypass logical checks or manipulate contract behavior. With $69 million lost across 21 incidents, this vulnerability remains a critical challenge for DeFi developers striving to secure their smart contracts.
How Improper Input Validation Exploits Work
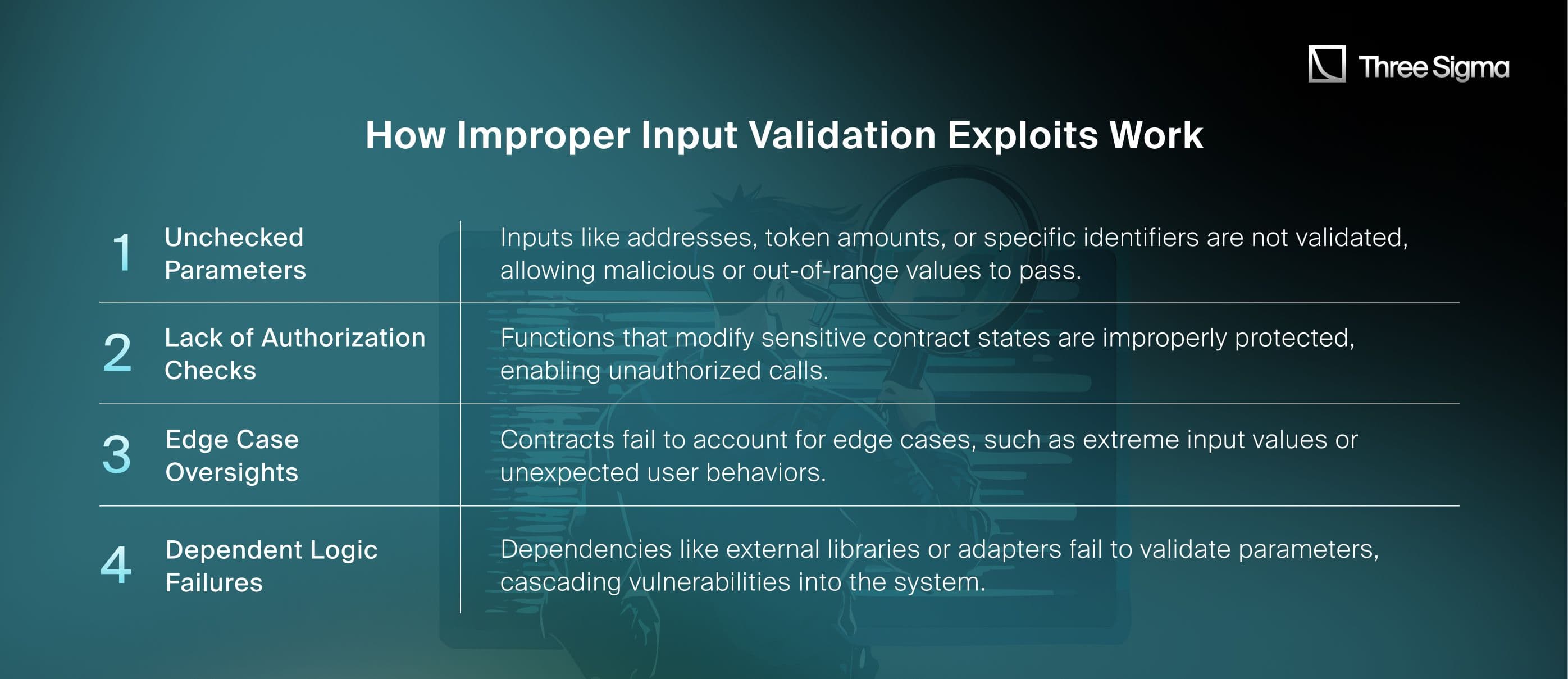
Case Study: DeltaPrime Protocol Exploit
- Date: November 11, 2024
- Amount Lost: $4.85 million
- Blockchain: Avalanche and Arbitrum
- Attack Vector: Improper input validation in debt swap and reward mechanisms.
Overview:DeltaPrime, an undercollateralized lending protocol, faced a severe exploit when an attacker manipulated unchecked inputs in the swapDebtParaSwap and claimReward functions. The vulnerabilities allowed unauthorized borrowing and manipulated reward claims, draining liquidity from the protocol.Steps of the Attack:
- Flash Loan Acquisition:The attacker acquired a flash loan of 59.958 WETH to fund the exploit, providing temporary liquidity.
- Exploiting swapDebtParaSwap:The _repayAmount parameter was not validated before being processed. The attacker used 59.9 ETH as collateral, borrowed 1.18 WBTC, and transferred it to a malicious contract without triggering repayment logic.
- Manipulating claimReward:The attacker passed a malicious contract to the pair parameter in the claimReward function. This allowed the attacker to manipulate DeltaPrime's reward system and withdraw unearned rewards worth 59.9 ETH.
- Post-Exploit Asset Management:Instead of dispersing the stolen assets, the attacker reinvested them in DeFi protocols on Avalanche to generate passive income.
Root Cause:The swapDebtParaSwap function failed to validate input parameters like _repayAmount, and the claimReward function lacked checks for malicious external contracts, exposing the system to manipulation.
How to Mitigate Improper Input Validation
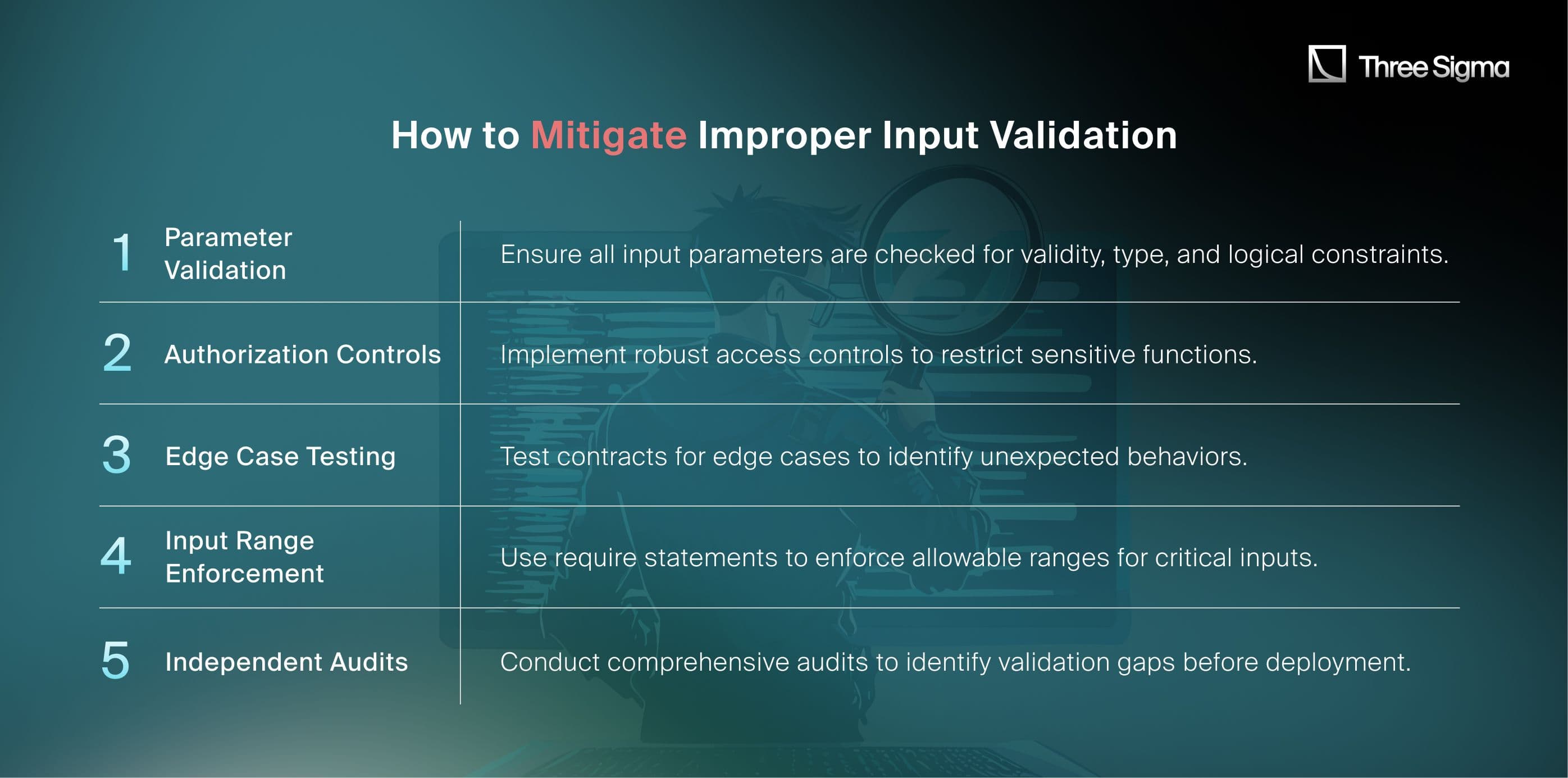
Lessons Learned
The DeltaPrime exploit underscores the importance of rigorous input validation in smart contracts. Unchecked inputs, especially in critical financial operations, can have catastrophic consequences. Implementing validation mechanisms, thorough testing, and external audits are essential to mitigating such vulnerabilities.
For a detailed analysis of the DeltaPrime exploit, read the detailed report.
5. Insufficient Function Access Controls

Access control vulnerabilities ranked as a major attack vector in 2024, leading to $27 million in losses across 29 incidents. These exploits occur when protocols fail to enforce proper restrictions on sensitive functions, allowing attackersunauthorized access to manipulate or extract funds.
How Access Control Vulnerabilities Exploits Work
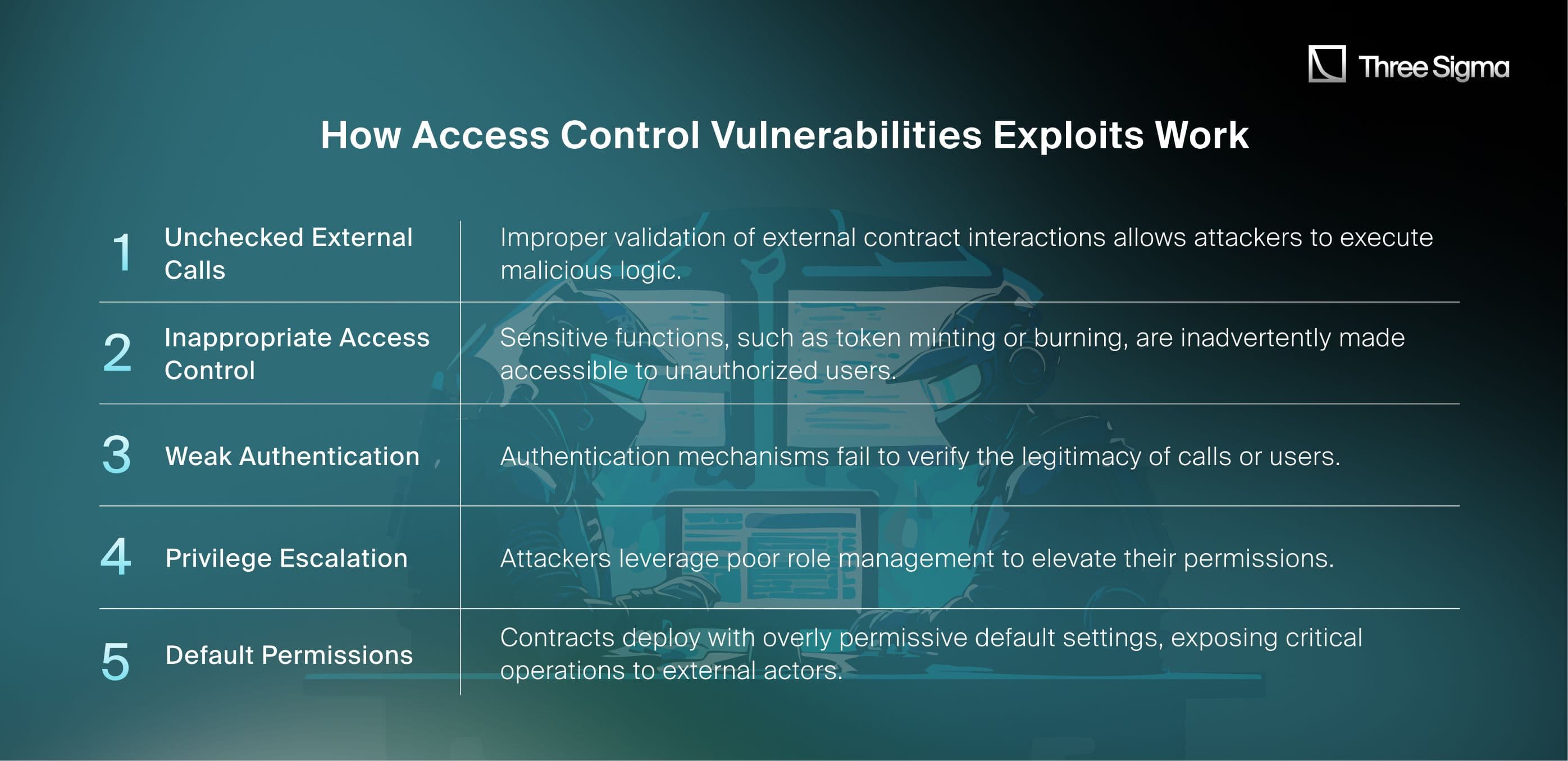
Case Study: Nexera Protocol Exploit
- Date: August 7, 2024
- Amount Lost: $449,000
- Blockchain: Ethereum and Avalanche
- Attack Vector: Credential compromise and weak access control over staking contracts.
Overview:The Nexera Protocol suffered an exploit when attackers gained unauthorized access to credentials managing smart contracts. Using these credentials, they transferred $NXRA tokens from staking contracts and manipulated ownership of key contracts. While attackers initially stole 47.24 million$NXRA tokens, Nexera recovered 32.5 million tokens, limiting their losses to 14.75 million$NXRA (equivalent to $449,000).Steps of the Attack:
- Credential Compromise:Attackers executed malicious code to obtain credentials for managing Nexera Fundrs smart contracts.
- Ownership Takeover:At 05:05 UTC, attackers transferred ownership of Ethereum contracts, blocking Nexera’s ability to upgrade or reassign ownership.
- Unauthorized Token Transfer:At 05:28 UTC, attackers transferred $NXRA tokens from the Fundrs staking contract and began selling on Uniswap.
- Token Freezing and Recovery:Nexera paused the $NXRA token contract at 06:28 UTC, freezing remaining funds and recovering 32.5 million $NXRA tokens.
Root Cause:The attack stemmed from compromised credentials, exacerbated by insufficient role-based access controls on key contract functions.
Case Study: Nexera Protocol Exploit
- Date: August 7, 2024
- Amount Lost: $449,000
- Blockchain: Ethereum and Avalanche
- Attack Vector: Credential compromise and weak access control over staking contracts.
Overview:The Nexera Protocol suffered an exploit when attackers gained unauthorized access to credentials managing smart contracts. Using these credentials, they transferred $NXRA tokens from staking contracts and manipulated ownership of key contracts. While attackers initially stole 47.24 million$NXRA tokens, Nexera recovered 32.5 million tokens, limiting their losses to 14.75 million$NXRA (equivalent to $449,000).Steps of the Attack:
- Credential Compromise:Attackers executed malicious code to obtain credentials for managing Nexera Fundrs smart contracts.
- Ownership Takeover:At 05:05 UTC, attackers transferred ownership of Ethereum contracts, blocking Nexera’s ability to upgrade or reassign ownership.
- Unauthorized Token Transfer:At 05:28 UTC, attackers transferred $NXRA tokens from the Fundrs staking contract and began selling on Uniswap.
- Token Freezing and Recovery:Nexera paused the $NXRA token contract at 06:28 UTC, freezing remaining funds and recovering 32.5 million $NXRA tokens.
Root Cause:The attack stemmed from compromised credentials, exacerbated by insufficient role-based access controls on key contract functions.
How to Mitigate Access Control Vulnerabilities
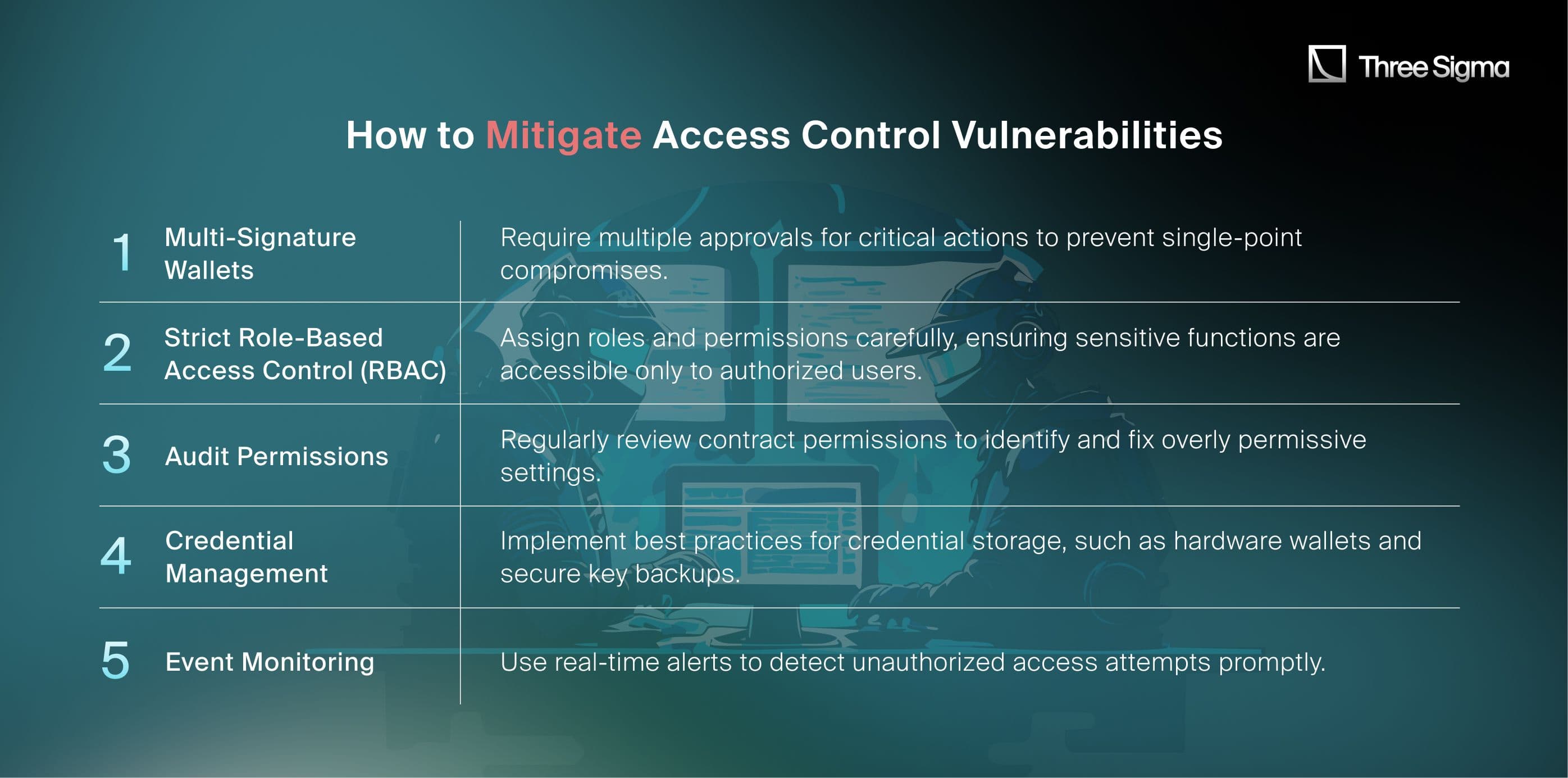
Lessons Learned
The Nexera exploit highlights the importance of robust access control mechanisms and secure credential management. Credential compromise and poor access restrictions can lead to catastrophic losses. By enforcing strict permissions, employing multi-signature wallets, and continuously monitoring for anomalies, DeFi protocols can mitigate such risks effectively.
For a detailed analysis of the Nexera exploit, read the detailed report.

Reward manipulation attacks rank as a significant DeFi attack vector in 2024, leading to $17 million in losses across 34 incidents. These exploits occur when attackers manipulate reward distribution mechanisms in protocols, often through market manipulation or exploiting improper incentive logic.
How Reward Manipulation Attacks Work

Case Study: Gamma Finance Exploit
- Date: January 4, 2024
- Amount Lost: $6.3 million
- Blockchain: Ethereum
- Attack Vector: Price manipulation of liquidity pools affecting reward distributions.
Overview:Gamma Finance suffered a significant exploit due to improper configurations in its deposit proxy settings. The attacker manipulated price thresholds of liquidity pools to claim a disproportionate amount of LP tokens and rewards. The core issue was an overly generous price change threshold of -50% to +100%, which allowed for significant price manipulation without triggering safeguards.Steps of the Attack:
- Flash Loan Execution:The attacker initiated flash loans from Uniswap and Balancer to manipulate the price of gDAI in the gDAI-DAI vault.
- Price Manipulation:The flash loans inflated the pool price of gDAI, bypassing the high price change threshold.
- Looping Deposits and Withdrawals:Exploiting the inflated price, the attacker deposited gDAI and received an excessive number of LP tokens. The attacker withdrew funds, repeating the process in multiple transactions to maximize rewards.
- Profit Extraction:The attacker redeemed the LP tokens for rewards and withdrew manipulated funds, draining the vault.
Root Cause:The overly permissive price change threshold allowed price manipulation to occur without triggering deposit restrictions, enabling the attacker to generate rewards far exceeding their actual contributions.
How to Mitigate Reward Manipulation

Lessons Learned
The Gamma Finance exploit highlights the risks of improperly configured reward mechanisms and the need for robust safeguards against price manipulation. Reward distribution logic must account for edge cases, ensure accurate price tracking, and cap excessive claims. By implementing tighter controls and thorough testing, protocols can protect against similar exploits.
For a detailed analysis of the Gamma Finance exploit, read the detailed report.
7. Reentrancy

Reentrancy attacks remain a critical vulnerability in the DeFi ecosystem, leading to $47 million in losses across 22 incidents in 2024. These attacks exploit a contract's inability to manage state changes effectively during external calls, allowing attackers to manipulate funds or logic through repeated function reentry.
How Reentrancy Attacks Work

Case Study: Penpie Finance Reentrancy Exploit
- Date: September 3, 2024
- Amount Lost: $27 million
- Blockchain: Arbitrum and Ethereum
- Attack Vector: Missing reentrancy protection in reward harvesting functions.
Overview:Penpie Finance suffered a significant exploit when an attacker created a fake Pendle Market to manipulate the batchHarvestMarketRewards() function. The missing nonReentrant modifier allowed the attacker to re-enter the function, manipulate reward calculations, and claim unauthorized funds.Steps of the Attack:
- Fake Market Creation:The attacker created a fake Pendle Market using a malicious smart contract and deposited it into Penpie.
- Flash Loan Execution:The attacker used Balancer flash loans to deposit large amounts of assets into the fake market, inflating its value.
- Reentrant Reward Manipulation:The attacker called batchHarvestMarketRewards() on the fake market. The lack of reentrancy protection allowed the attacker to call back into the function through PendleMarket::redeemRewards(), manipulating the reward calculations. The manipulated rewards were attributed to the fake market, enabling the attacker to claim them.
- Withdrawal and Conversion:The attacker withdrew the rewards and converted them back to the original assets, repaid the flash loan, and pocketed the profits.
Root Cause:The batchHarvestMarketRewards() function lacked a nonReentrant modifier, allowing the attacker to exploit the reentrant behavior during reward calculation and distribution.
How to Mitigate Reentrancy Attacks
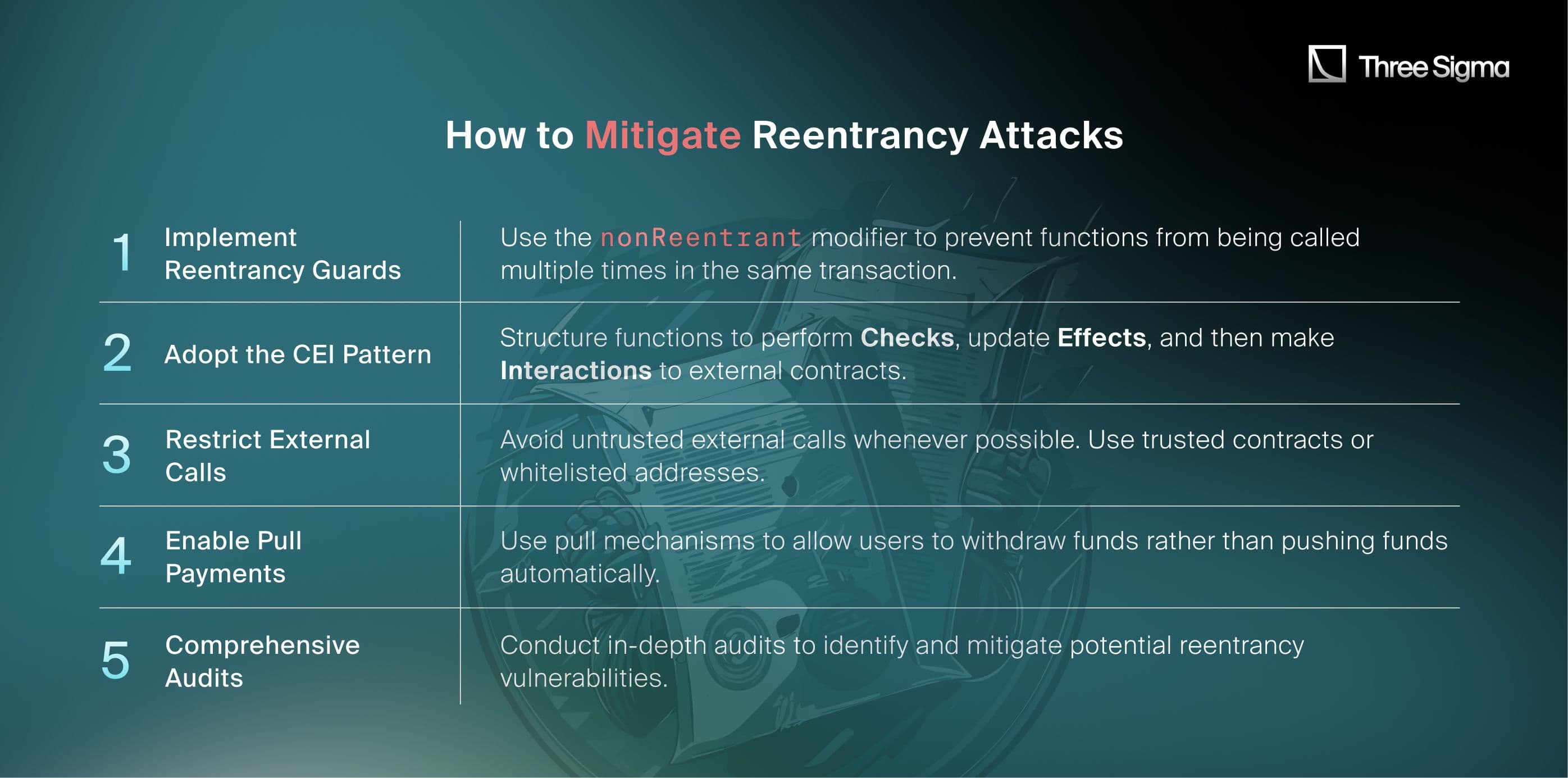
Lessons Learned
The Penpie exploit highlights the dangers of missing reentrancy protection in critical functions. Without robust guards and proper state management, protocols remain vulnerable to repeated reentrant calls that can drain funds or alter logic. By adopting best practices like the CEI pattern, reentrancy guards, and pull payments, protocols can safeguard their users and prevent similar exploits.
For a detailed analysis of the Penpie Finance exploit, read the detailed report.
8. Arbitrary External Calls

Arbitrary external calls have emerged as a significant attack vector in the DeFi ecosystem in 2024, resulting in over $21 million in losses across 18 incidents. These attacks exploit insufficient validation and control over external contract calls, enabling malicious actors to manipulate protocol behavior or drain funds.
How Arbitrary External Call Attacks Work

Case Study: LI.FI Protocol Exploit
- Date: July 16, 2024
- Amount Lost: $9 million
- Blockchain: Ethereum and Arbitrum
- Attack Vector: Lack of input validation in GasZipFacet contract.
Overview:LI.FI, a multi-chain liquidity aggregation protocol, suffered a significant exploit due to inadequate validation in the newly deployed GasZipFacet contract. The vulnerability allowed an attacker to process arbitrary external transactions, stealing user funds through malicious transferFrom operations.Steps of the Attack:
- Malicious Contract Deployment:The attacker deployed a malicious smart contract designed to interact with the GasZipFacet contract.
- Crafting a Malicious Transaction:The attacker utilized the depositToGasZipERC20() function in GasZipFacet, providing manipulated callData encoding a malicious transferFrom function call.
- Exploiting the Low-Level Call:The LibSwap.swap() function in GasZipFacet executed the crafted callData, triggering unauthorized transferFrom operations on user tokens.
- Batch Execution:The attacker repeated this process across multiple transactions, stealing approximately $9 million in total.
- Fund Distribution:Stolen funds were transferred to multiple wallets and partially laundered using privacy tools like Tornado Cash.
Root Cause:The GasZipFacet contract failed to validate the callData parameter, allowing arbitrary operations to be executed during external calls.
How to Mitigate Arbitrary External Call Attacks

Lessons Learned
The LI.FI exploit highlights the dangers of insufficient validation and control over external calls in smart contracts. Properly validating external interactions and implementing strict safeguards are critical to preventing similar attacks. Moving forward, protocols must prioritize input validation, minimize trust in external calls, and thoroughly test new deployments to avoid catastrophic losses.
For a detailed analysis of the LI.FI exploit, read the detailed report.
9. Governance Attacks

Governance attacks are a critical vulnerability in decentralized finance (DeFi), exploiting weaknesses in protocol decision-making mechanisms to manipulate outcomes for personal gain. In 2024, governance attacks led to over $37 million in losses across various incidents, threatening not only individual protocols but the stability of the broader DeFi ecosystem.
How Governance Attacks Work
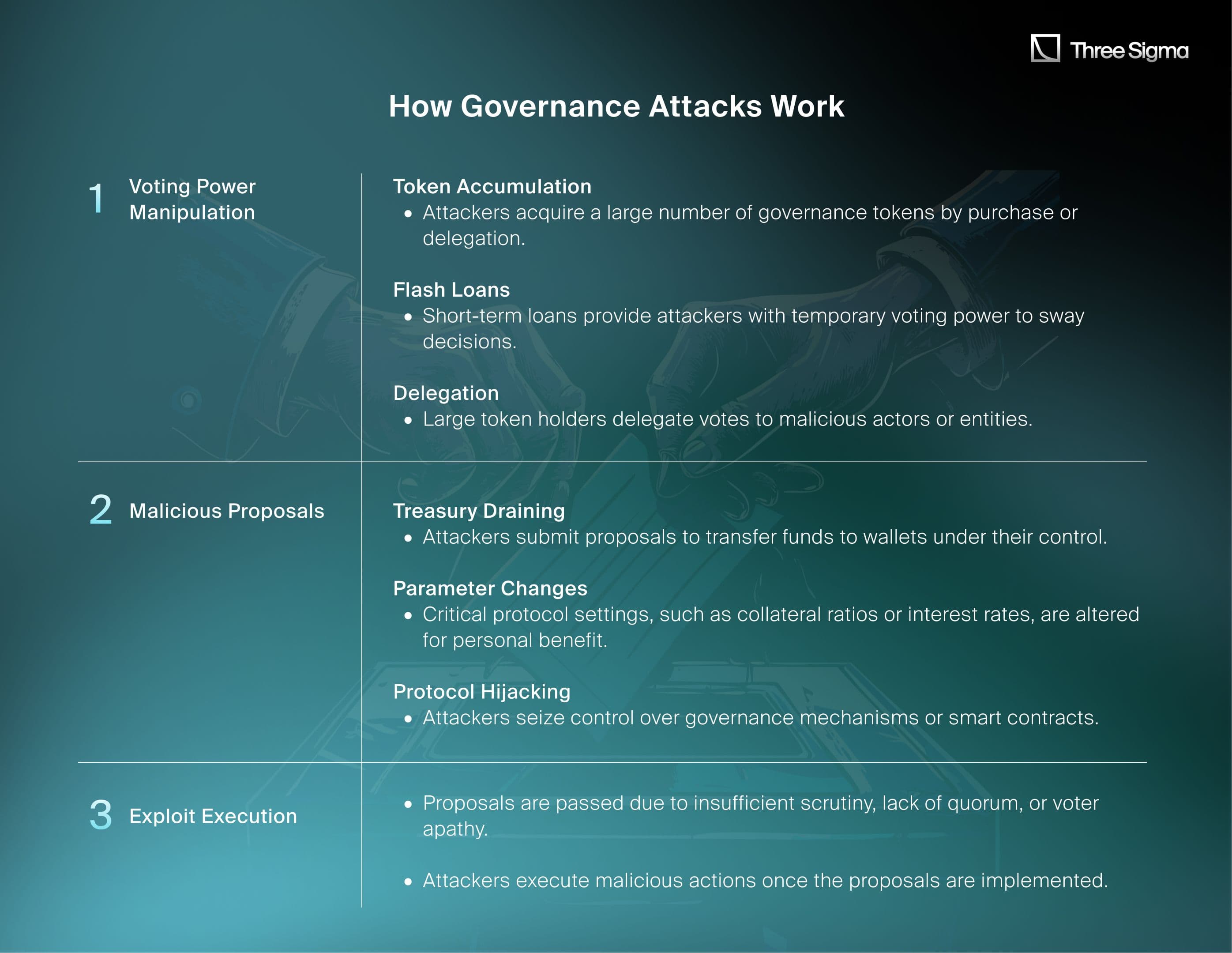
Case Study: Compound Protocol Governance Exploit
- Date: July 29, 2024
- Amount at Stake: $25 million
- Blockchain: Ethereum
- Attack Vector: Voting manipulation and malicious proposal submission.
Overview:Compound, a leading DeFi lending protocol, suffered a governance attack where Proposal 289 transferred 499,000 COMP tokens (5% of the treasury) to an unmonitored multisig wallet controlled by the "Golden Boys" team. This malicious proposal passed with a narrow margin due to coordinated voting by the attackers.Steps of the Attack:
- Proposal Submission:Proposal 289, introduced by the Golden Boys team, aimed to allocate treasury funds to the goldCOMP protocol. The proposal lacked community discussion and transparency.
- Voting Manipulation:Attackers used delegated votes and possibly flash loans to accumulate 682,000 votes in favor, narrowly surpassing the 633,000 opposing votes. Large-scale token movements and coordinated delegations were observed before the vote.
- Market Reaction:The approval caused widespread panic, leading to a 30% drop in COMP’s price within a week.
- Community Intervention:Security advisors flagged the suspicious activities and highlighted governance risks. Intense community discussions led to the proposal being rescinded after negotiations with the attackers.
Root Cause: The governance mechanism allowed attackers to manipulate voting outcomes by leveraging token concentration and voter apathy. The lack of safeguards against sudden proposals and insufficient community engagement exacerbated the risk.
How to Mitigate Governance Attacks

Lessons Learned
The Compound governance attack highlights the importance of robust, transparent, and participatory governance mechanisms in decentralized systems. Preventing such exploits requires a combination of technical safeguards, community vigilance, and continuous improvement of governance structures. By addressing these vulnerabilities, DeFi protocols can ensure fairer decision-making processes and enhance user trust.
For a detailed analysis of the Compound Protocol exploit, read the detailed report.
10. Uninitialized Contracts

Uninitialized contract vulnerabilities remain a significant attack vector in decentralized systems, allowing attackers to exploit improperly initialized parameters or unconfigured state variables. In 2024, these exploits accounted for over $25 million in losses across various incidents, highlighting the critical importance of rigorous initialization processes during deployment.
How Uninitialized Contract Attacks Work

Case Study: Ronin Bridge Exploit
- Date: August 6, 2024
- Amount Lost: $12 million
- Blockchain: Ethereum and Ronin
- Attack Vector: Uninitialized proxy parameters in the Ronin Bridge V2 contract.
Overview:The Ronin Bridge, a multi-signature bridge facilitating cross-chain transactions between Ethereum and Ronin, suffered an exploit due to the improper initialization of critical parameters during a contract upgrade. The oversight left _totalOperatorWeight uninitialized, allowing the attacker to bypass cross-chain transaction verification and drain funds. Fortunately, the attacker was a whitehat who returned the stolen assets.Steps of the Attack
- Proxy Upgrade Misconfiguration:During the upgrade, the Ronin team added two new initialization functions, initializeV3 and initializeV4. Only initializeV4 was executed, leaving _totalOperatorWeight in initializeV3 uninitialized and defaulting to zero.
- Unvalidated Withdrawal Execution:The attacker deployed a malicious contract to interact with the MainchainGatewayV3 contract via the proxy. The attack targeted the submitWithdrawal function, which calculated the minimumWeight parameter using _totalOperatorWeight.
- Exploitation of Zero Weight:_totalOperatorWeight was incorrectly set to zero, causing the minimumWeight check to pass without requiring valid signatures. The attacker successfully bypassed verification and triggered unauthorized asset transfers.
- Fund Withdrawal:The attacker withdrew approximately 4,000 ETH and 2 million USDC using two transactions. The exploit leveraged a crafted delegatecall to execute malicious logic within the Ronin Bridge.
Root CauseThe vulnerability stemmed from the incomplete execution of initialization functions during the proxy upgrade. By skipping initializeV3, the critical _totalOperatorWeight variable remained uninitialized, compromising the integrity of transaction verification.
How to Mitigate Uninitialized Contract Vulnerabilities

Lessons Learned
The Ronin Bridge exploit underscores the importance of meticulous initialization processes in smart contract development. Uninitialized parameters can render otherwise secure systems vulnerable, highlighting the need for robust deployment practices and rigorous testing.
For a detailed analysis of the Ronin Bridge exploit, read the full report.
Each 2024 exploit exposed more than code: it revealed repeatable design flaws and test failures.
Our Smart Contract Audit and other web3 audit services help prevent déjà vu by catching both technical and structural vulnerabilities before they become headlines. Mitigate proxy risks before mainnet.
Conclusion

The analysis of the Top 10 DeFi Attack Vectors in 2024 reveals a rapidly evolving landscape of blockchain security threats. While progress has been made in mitigating certain types of exploits, others continue to grow in sophistication, necessitating comprehensive security strategies.For DeFi projects looking to secure their smart contracts and protect user assets, we at Three Sigma offer comprehensive security solutions tailored to the evolving blockchain landscape. Contact us today to ensure your platform is safeguarded against the latest cybersecurity threats.
Key Takeaways
- Improved Defense Against Price Oracle and Reward Manipulation Attacks: Losses from these attack vectors dropped significantly—from approximately $400 million last year to around $70 million—thanks to the diligence of smart contract auditors, bug bounty hunters, and improved protocol designs. However, continuous vigilance is essential to maintain these gains.
- Emerging Threats: Function Parameter Validation and Access ControlsCode-related vulnerabilities such as improper input validation and insufficient access controls are on the rise. These issues highlight the critical need for rigorous testing and enhanced developer education.
- Private Key Theft: The Leading Attack VectorAccounting for the majority of losses, private key theft underscores the urgent need for robust operational security (OpSec) measures. Sophisticated attackers, including criminal organizations and nation-states, exploit spear-phishing, stealth malware, and poor key management practices to devastating effect.
- Malicious Insider Threats: A Growing ConcernAs the DeFi space matures and blockchain projects scale, insider threats have emerged as a top concern. Strengthening internal controls and fostering a culture of security awareness are vital steps to counter this risk.
- Expand Security Programs Beyond Code AuditsBlockchain projects must look beyond traditional code audits to address broader security concerns, including key management, infrastructure, endpoint security, and personnel training. Comprehensive security programs should prioritize holistic risk management to protect users and maintain trust.
Frequently Asked Questions (FAQ)
1. What were the most common DeFi attack vectors in 2024?
The most common attack vectors in 2024 included:
- Stolen Private Keys: Responsible for $449 million in losses.
- Price Oracle Manipulation: Caused $52 million in damages.
- Improper Function Parameter Validation: Resulted in $69 million in losses.
- Reentrancy Attacks: Accounted for $47 million in losses.
2. How can DeFi protocols prevent stolen private key attacks?
To prevent private key theft, protocols and users can:
- Implement multi-signature wallets for added security.
- Use cold storage solutions for large reserves.
- Regularly conduct security audits of wallet management systems.
- Educate employees and users on avoiding phishing and malware threats.
3. What is price oracle manipulation, and how does it work?
Price oracle manipulation involves distorting the price of an asset by exploiting weaknesses in price oracles. Attackers typically use flash loans to manipulate liquidity pools or exchange rates, enabling them to profit from undercollateralized loans or arbitrage.
4. What are some lessons learned from the 2024 DeFi exploits?
Key lessons from 2024 include:
- The importance of robust input validation and access controls.
- The need for decentralized, reliable, and diversified oracle systems.
- The value of education and security awareness to mitigate insider threats.
- Expanding security beyond audits to include infrastructure and operational security.
5. How do governance attacks threaten DeFi protocols?
Governance attacks occur when malicious actors manipulate voting mechanisms to pass proposals that drain funds or alter protocol parameters. Techniques include:
- Acquiring temporary voting power through flash loans.
- Submitting malicious proposals with insufficient scrutiny.
- Exploiting voter apathy or insufficient quorum requirements.
6. What measures can protect against reentrancy attacks?
Reentrancy attacks can be mitigated through:
- Using the nonReentrant modifier in smart contracts.
- Adopting the Checks-Effects-Interactions (CEI) pattern to update states before making external calls.
- Restricting untrusted external calls and enabling pull payments instead of push payments.
7. Why is input validation critical in DeFi smart contracts?
Improper input validation exposes protocols to exploits like:
- Manipulating sensitive parameters to bypass logical checks.
- Exploiting edge cases that developers might not anticipate.
- Leading to financial losses or protocol instability.
8. How can protocols enhance their defenses against exploits?
Protocols can improve security by:
- Conducting independent audits of smart contracts and infrastructure.
- Implementing multi-signature approvals for critical actions.
- Using circuit breakers to pause operations during suspicious activity.
- Educating developers on best practices for secure coding and testing.
9. What trends were observed in DeFi exploits between 2023 and 2024?
- Total Losses Decreased: From $1.15 billion in 2023 to $730 million in 2024.
- Shift in Attack Vectors: Insider threats and function validation flaws gained prominence, while price oracle manipulation saw reduced impact.
- Consistency in Private Key Theft: It remained the leading attack vector, responsible for the highest financial losses in both years.
10. How can users protect themselves when participating in DeFi?
Users can protect themselves by:
- Only interacting with audited protocols and using reputable wallets.
- Avoiding sharing private keys or storing them insecurely.
- Diversifying assets across multiple platforms to reduce risk.
- Staying informed about the latest DeFi exploits and vulnerabilities.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.