What is a smart contract audit?
A smart contract audit is a comprehensive examination of the code that underlies a smart contract, such as Solidity, Move or Rust, performed by security experts. The purpose is to identify vulnerabilities, logical errors, and inefficiencies before deployment, ensuring the contract operates securely and as intended. Smart contracts are the foundation of blockchain technology, and getting them right is crucial. Any weakness in the code creates massive vulnerabilities for both projects and users. With billions of dollars flowing through DeFi platforms and NFT marketplaces, a single coding error can lead to devastating exploits and lost funds. That's why comprehensive web3 security audits are essential for protecting users and maintaining trust in the entire decentralized ecosystem.
How Smart Contract Audits Work
A smart contract audit typically follows a structured process to ensure all vulnerabilities are uncovered and addressed:
1. Preparation: The development team shares the final or near-final contract code and documentation with the auditors.
2. Automated Analysis: Auditors run static and dynamic analysis tools to detect common issues such as reentrancy, overflow/underflow, and gas inefficiencies. 3. Manual Review: Security experts manually inspect the code for logical errors, potential exploits, and areas where the contract could behave unexpectedly.
4. Testing & Simulation: Test cases and simulations are run in controlled environments to replicate possible attack scenarios.
5. Reporting: A detailed report is prepared, highlighting vulnerabilities, severity levels, and recommendations.
6. Remediation & Re-audit: Developers fix identified issues and may request a follow-up audit to confirm all fixes are secure.
The Importance and Benefits of Smart Contract Audits
A blockchain security audit is a comprehensive examination of a smart contract's source code by blockchain security experts. The primary goal is to identify and resolve potential security vulnerabilities, logical errors, or performance issues before deployment. This proactive approach ensures the smart contract operates as intended and is resilient against malicious attacks, playing a vital role in how to secure DeFi platforms with audits.
Key Benefits of Blockchain Security Audits
- Mitigating Security Risks: Uncovering bugs and weaknesses that could be exploited by hackers, significantly reducing the risk of breaches.
- Ensuring Code Integrity: Identifying and correcting flaws before deployment to ensure correct functionality.
- Building Trust with Users and Investors: Reassuring stakeholders that the code is secure and reliable.
- Facilitating Scalability and Adoption: Contributing to the ongoing reliability of blockchain applications, supporting wider adoption.
In a blockchain environment where code is law, conducting smart contract audits provides essential protection against technical vulnerabilities and reputational risks. By proactively securing smart contracts, developers strengthen the reliability and credibility of their projects, following the best blockchain security practices.
Common Vulnerabilities Found in Smart Contracts
Audits often uncover vulnerabilities that could lead to loss of funds or system failure, including:
• Reentrancy Attacks: Exploiting recursive calls to drain funds.
• Integer Overflow/Underflow: Arithmetic errors causing incorrect balances or logic.
• Access Control Issues: Functions left unprotected, allowing unauthorized changes.
• Front-Running: Attackers exploiting transaction ordering for financial gain.
• Logic Flaws: Contract behavior that doesn’t match the intended design. Identifying and mitigating these risks is critical for ensuring user trust and protocol stability.
Why Do You Need a Smart Contract Audit to Ensure User and Fund Security?
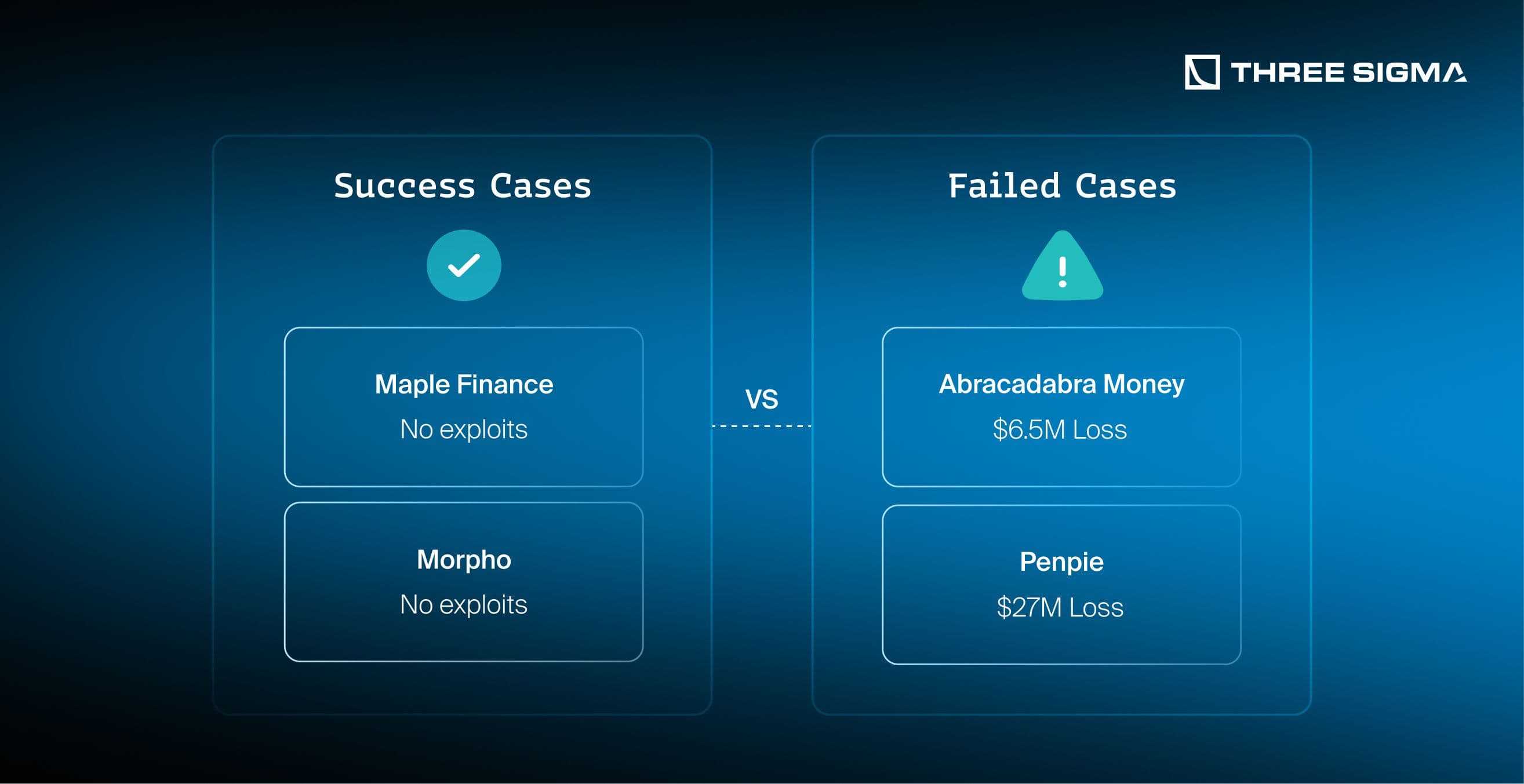
Understanding the necessity of smart contract security is crucial for any blockchain project. A comparison of successful and failed projects illustrates the impact of thorough auditing practices on security and user trust. Let’s explore how smart contract audits protect against vulnerabilities and ensure the integrity of decentralized applications. The importance of smart contract audits for blockchain is highlighted by the real-world impact audits can have on user safety and fund protection.
Types of Smart Contract Audits
• Automated Audits: Use scanning tools to quickly detect known vulnerabilities and coding errors.
• Manual Audits: Human experts review code for complex logical flaws and unique risks.
• Formal Verification: Mathematically proving that a contract’s logic matches its specifications.
• Hybrid Audits: Combining automated tools with manual expertise for the most comprehensive coverage. At Three Sigma, we combine automated scans, expert manual reviews, and, where needed, formal verification into a tailored hybrid audit approach that maximizes security and efficiency for each client.
Successful Cases
Maple Finance
Maple Finance has demonstrated a strong commitment to blockchain security by undergoing multiple audits with top-tier firms, including Spearbit, Trail of Bits, 0xMacro, and our team at Three Sigma.
Over several releases, these audits have addressed vulnerabilities of varying severity and strengthened the robustness and reliability of Maple’s smart contracts.
Audits Summary:
- Total Audits Conducted: 9
- December 2022 Release: 3 audits (Trail of Bits, Spearbit, Three Sigma)
- June 2023 Release: 2 audits (Cantina via Spearbit, Three Sigma)
- December 2023 Release: 2 audits (Three Sigma, 0xMacro)
- August 2024 Release: 2 audits (Three Sigma, 0xMacro)
Bug Bounty: Maple maintains an active bug bounty program with Immunefi, offering incentives to white-hat hackers for identifying potential vulnerabilities, and providing another layer of protection.
Key Security Practices:
- Multiple Audits: Subjecting their protocol to numerous audits and addressing all relevant issues prior to each release.
- Collaboration with Leading Security Firms: Leveraging specialized expertise to enhance security.
- Transparent Reporting: Publicly sharing audit reports and security measures.
Example Vulnerability Fix: During the audit of Maple's fixed-term loan system, a critical vulnerability was identified where an unchecked fee manager address could be modified by attackers to redirect funds maliciously. By implementing an isInstanceOf check to whitelist fee managers, Maple mitigated the risk of unauthorized access to loaned funds, reinforcing both contract integrity and user trust.
Notably, following our June 2023 audit, no subsequent reviews by other firms have identified vulnerabilities of high severity or greater, a testament to the depth and meticulous approach of our assessment.
Outcome: Strengthened protocol security, enhanced user confidence, and contributed to the platform's success.
Morpho
Morpho has shown its commitment to blockchain security by undergoing multiple audits with top-tier firms, including Spearbit, OpenZeppelin, and Trail of Bits. Over several releases, these audits have addressed vulnerabilities of varying severity, reinforcing the robustness and reliability of Morpho’s smart contracts.
Audits Summary:
- Total Audits Conducted: 27
- 2022: 11 audits (Spearbit, Chainsecurity, Omniscia, Trail of Bits, Pessimistic, Securing)
- 2023: 10 audits (Cantina Contest, Spearbit, OpenZeppelin, Pessimistic)
- 2024: 1 audit (Spearbit)
Bug Bounty: Morpho maintains an active bug bounty program, offering incentives to white-hat hackers for identifying potential vulnerabilities, providing another layer of protection.
Key Security Practices:
- Multiple Audits: Subjecting their protocol to numerous audits and addressing all relevant issues prior to each release.
- Collaboration with Leading Security Firms: Leveraging specialized expertise to enhance security.
- Transparent Reporting: Publicly sharing audit reports and security measures.
Example Vulnerability Fix: During a recent audit of Morpho’s Vaults, a high-risk issue was identified: if an individual Morpho Blue market’s Interest Rate Model (IRM) fails, the vault could become inoperable, effectively locking users’ funds. Specifically, if an IRM malfunction occurs, key operations such as withdrawals, reallocations, and deposits may revert. To mitigate this, Morpho was advised to extensively document this scenario, ensuring that protocol stakeholders are aware of these risks and prepared to respond if an individual market failure impacts the vault.
Outcome: Strengthened protocol security, enhanced user confidence, and contributed to the platform's success.
Failed Cases
Abracadabra Money Exploit
A vulnerability in Abracadabra’s debt calculation mechanism within its CauldronV4 contracts allowed an attacker to inflate borrow shares while keeping total borrow assets low, resulting in approximately $6.5 million in losses. The exploit occurred after changes were made to the contracts, and these changes were not audited.
Technical Breakdown: The attack began with a flash loan, leveraging Abracadabra's DegenBox and CauldronV4 contracts. The core issue lay in how the protocol calculated the asset-to-share ratio in its debt model. When the attacker triggered the repayForAll function, it incorrectly adjusted totalBorrowAssets without updating totalBorrowShares, creating a discrepancy. By repeatedly cycling through borrow and repay actions, the attacker artificially inflated their borrow shares without increasing the total assets.
Preventive Measures: A smart contract audit could have identified this discrepancy in the debt-to-share calculation. Implementing stricter checks on totalBorrowAssets and totalBorrowShares ratios, along with enhanced invariant checks to prevent disproportionate increases, would mitigate such risks. Auditing the changes made to the contracts would have been crucial in detecting this vulnerability.
Detailed Analysis: Abracadabra Money Exploit Explained.
Penpie Reentrancy Exploit
A reentrancy vulnerability in Penpie’s batchHarvestMarketRewards function allowed an attacker to create a fraudulent Pendle Market, manipulate staking rewards, and siphon $27 million across Ethereum and Arbitrum. This exploit occurred after changes were introduced to the contract, which were not subjected to a security audit.
Technical Breakdown: The exploit involved creating a fake market using a crafted smart contract, then leveraging a flash loan to manipulate reward calculations. The attacker invoked Penpie’s batchHarvestMarketRewards function, which lacked a reentrancy guard, allowing them to repeatedly enter the function and inflate their staking balance. This resulted in unauthorized reward allocations, which the attacker subsequently withdrew.
Preventive Measures: A smart contract audit could have detected the absence of a nonReentrant modifier on the batchHarvestMarketRewards function. Implementing reentrancy protection is essential in functions that handle reward calculations and interact with external contracts, ensuring these high-risk areas are safeguarded against recursive calls. Auditing the changes made to the contracts would have been crucial in detecting this vulnerability.
Detailed Analysis: Penpie Exploit Explained.
The stark contrast between successful security measures and the exploits underscores the critical need for smart contract audits. A thorough audit process is essential for identifying vulnerabilities, ensuring code integrity, and building user trust in blockchain projects.
Impact Analysis: Audited vs Non-Audited Smart Contract Exploits

Understanding the real-world impact of smart contract audits provides valuable insights into their effectiveness. Let's analyze notable examples from both audited and non-audited protocols to illustrate the difference in outcomes.
Audited Protocol Example: Radiant Capital
Summary
Despite having multiple audits from leading firms (OpenZeppelin, BlockSec, Peckshield, and Zokyo), Radiant Capital, a fork of Aave V2 on Arbitrum, suffered an exploit in January 2024 on its newly launched native USDC market, resulting in the theft of 1,900 ETH ($4.5M). Although the protocol underwent multiple audits, a well-known vulnerability was identified by an attacker and exploited within seconds of the new market's activation. This incident underscores the risks associated with forking protocols without updating mitigations, particularly in rapidly evolving security landscapes.
Technical Breakdown
Radiant's exploit revolved around an uninitialized or zeroed totalSupply parameter for the new USDC market, an issue previously noted and mitigated in Aave’s main protocol. The attacker leveraged a combination of flash loans and rounding errors to manipulate collateral value, exploiting a short window after market deployment to drain funds.
Attack Steps
- Identifying the Vulnerability: The attacker targeted a specific vulnerability in forked Aave V2 code affecting empty markets. By monitoring proposal updates, the attacker identified that Radiant’s USDC market was set to go live on Arbitrum on December 25th, allowing time to prepare an exploit.
- Flash Loan Execution: Upon the USDC market’s launch, the attacker quickly deployed a flash loan to inflate collateral value. They manipulated the
liquidityIndexusing a flaw in therayDivfunction, taking advantage of rounding errors that amplified their account’s balance. - Precision Manipulation: By supplying a small amount to the empty USDC market, the attacker manipulated the
liquidityIndexto inflate balances, then leveraged this distorted value to secure a disproportionate amount of ETH. - Siphoning Funds: Using repeated deposit and withdrawal operations, the attacker siphoned $4.5M in ETH.
Impact Limitation Due to Audits
While the audits did not directly prevent further exploitation, only $4.5M out of Radiant Capital’s $100M+ TVL (less than 5% of total funds) was lost. This was primarily due to rapid incident response and isolated market exposure rather than specific preventive measures from the audits. The audits did help establish monitoring systems that enabled Radiant to act quickly, containing the impact on a single market without affecting other funds.
Technical Breakdown: Radiant Capital Exploit Analysis
Non-Audited Protocol Example: Ronin Network
Summary
The Ronin Network, an Ethereum sidechain developed for Axie Infinity without comprehensive security audits, suffered a catastrophic exploit in March 2022, resulting in the theft of 173,600 ETH and 25.5M USDC (approximately $624M). The attack went undetected for six days until a user reported being unable to withdraw funds. This incident highlights the critical risks of operating high-value bridges without thorough security audits and proper monitoring systems, particularly in protocols prioritizing speed over security decentralization.
Technical Breakdown
The exploit centered on Ronin's validator system, which used a Proof of Authority model requiring only 5 out of 9 validator signatures to approve transactions. Four validators were controlled by Sky Mavis (the development team), and a critical security oversight allowed the attacker to gain control of a fifth validator through an outdated permission that was never revoked.
Attack Steps
- Identifying the Vulnerability: The attacker discovered that Sky Mavis held four validator keys on centralized servers and identified a remaining access permission from November 2021 that allowed Sky Mavis validators to sign for the Axie DAO validator.
- Validator Compromise: Through a backdoor in the gas-free RPC node, the attacker gained access to Sky Mavis's four validator private keys. They then exploited the outdated permission to access the fifth validator key from Axie DAO.
- Permission Exploitation: Using the compromised validator keys, the attacker was able to forge legitimate-looking withdrawal approvals, as the system only required 5 out of 9 signatures to authorize transactions.
- Fund Extraction: The attacker executed two major transactions: first withdrawing 173,600 ETH, then 25.5M USDC, which they later converted to ETH through various exchanges.
Impact Without Audit Protection
- Complete bridge compromise with $624M stolen (100% of bridged assets)
- No detection for six days after the exploit
- No monitoring system in place to catch unauthorized withdrawals
- No emergency pause mechanism available
- Lack of proper key management and access control systems
Technical Breakdown: Ronin Network Exploit Analysis
What Does a Smart Contract Auditor Do?

A smart contract auditor is essential for ensuring security for dApps and blockchain applications. These professionals play a pivotal role in protecting decentralized systems and user assets from vulnerabilities.
If your UI talks to on-chain logic, consider a dApp & Frontend Audit alongside the code review. Specifically for projects built on Sui or Aptos, our Move smart contract audits apply Move-specific threat modeling and static analysis.
Here’s an overview of their primary responsibilities:
Key Responsibilities of a Smart Contract Auditor
Identifying Security Vulnerabilities
Smart contract auditors meticulously analyze code to uncover security flaws, ensuring the contract is robust against both common and complex threats. Business logic errors can lead to unintended behaviors within the smart contract, resulting in issues like incorrect fund distribution, improper execution of functions, or failures to enforce intended constraints.
Performing Gas Optimizations
In addition to security, auditors focus on gas optimization by reviewing the smart contract code for efficiency. Identifying areas where gas costs can be minimized not only reduces expenses for users but also improves the performance of decentralized applications (dApps).
Ensuring Best Practices
Smart contract auditors ensure compliance with industry standards and best practices. This includes proper use of design patterns, adherence to regulatory requirements, and implementation of effective governance mechanisms, often complemented by a DAO Audit for protocol-level controls.
Protecting Users and the Integrity of DeFi Projects
Auditors help safeguard DeFi projects, reducing the likelihood of hacks and supporting overall project reliability. Their diligent work contributes to the overall health of the blockchain ecosystem, fostering confidence in decentralized finance solutions.
The Smart Contract Audit Process

If you’re wondering how to audit a smart contract, the process involves pre-audit preparation, code review, testing, documentation, remediation, and a final review before deployment.
Pre-Audit Preparation
In the initial phase, auditors define the scope of the audit and gather essential documentation, including technical specifications and existing test cases. This preparation helps establish clear expectations and objectives for the audit.
Code Review
This in-depth examination of smart contract code is the cornerstone of the audit, where the most significant value is generated. Auditors meticulously analyze the code through both manual review and automated tools, focusing on uncovering vulnerabilities of varying severity and ensuring the contract functions as intended. This phase establishes the foundation for a secure and reliable contract, making it by far the most essential part of the audit.
Testing Phase
During this phase, auditors develop and execute comprehensive test cases to validate the contract's functionality. This includes unit tests for individual functions and integration tests to assess interactions with other components, ensuring that the contract behaves as expected under various scenarios.
Documentation and Reporting
Upon completing the vulnerability assessment, auditors create a detailed report outlining identified issues, their potential impacts, and recommended remediation strategies. This report serves as a critical resource for developers to understand and address vulnerabilities.
Remediation and Follow-Up
Auditors collaborate closely with developers to resolve identified issues and may conduct follow-up audits to verify the effectiveness of the implemented fixes. This collaboration ensures that the smart contract is secure before its deployment.
Final Review
In the final stage, auditors perform a comprehensive review of the updated smart contract code to confirm that all vulnerabilities have been addressed and that the contract meets the highest security standards, instilling confidence for deployment.
When Is the Right Time to Conduct a Smart Contract Audit?

Conducting a smart contract audit is not just a one-time event; it’s a strategic process that should align with key milestones in a project’s lifecycle. An audit at the right time can safeguard a project’s security, functionality, and reputation. Here are the optimal stages for conducting a smart contract audit to ensure maximum impact.
After Initial Development and Before Mainnet Deployment
Auditing before deployment is essential for identifying vulnerabilities early on and ensuring the security and functionality of the code before going live. During the initial development stage, an audit helps detect and address design flaws or security weaknesses while core functionality is being finalized. This early review provides valuable insights that can refine the code and potentially save time and costs by preventing issues from reaching the public stage.
As the project moves into the pre-launch phase, a final audit is performed on a frozen, finalized codebase, ensuring robustness and readiness for mainnet deployment. At this stage, minimal further development is expected, allowing auditors to conduct a focused assessment of any lingering vulnerabilities that could compromise user funds or reputation once the project is live. Together, these early and pre-launch audits establish a secure foundation and build confidence as the project advances toward deployment.
After Major Code Changes or Feature Additions
For projects that are already live but continue to evolve, audits are essential after implementing any significant updates or new features. Each addition or change can introduce fresh risks, so performing an audit after these adjustments ensures that the system’s integrity remains intact. This approach is particularly relevant for platforms in the DeFi space, where new functionalities such as token mechanisms or governance upgrades are common and require additional scrutiny.
How to Choose a Smart Contract Auditor?
Selecting the right smart contract auditor is crucial for ensuring the security and reliability of your blockchain project. Here are key factors to consider when making your decision:
Technical and Domain-Specific Expertise
Choose auditors with deep technical expertise and a proven track record, particularly in areas related to your project. Look for auditors who have successfully handled similar smart contract types, protocols, or ecosystems. Experienced auditors bring specialized insight that helps uncover potential vulnerabilities effectively.
Reputation and Industry Standing
A reputable auditor demonstrates their expertise through positive client reviews, community standing, and case studies from previous audits. Seek recommendations from other developers or projects and assess the auditor’s reliability and trustworthiness within the blockchain space.
Responsiveness and Communication
Evaluate the auditor's responsiveness and communication style throughout the engagement. A good auditor should be accessible and proactive in addressing your questions and concerns. Clear and timely communication is essential for a smooth collaboration, ensuring that you are informed throughout the audit process.
Auditing Methodologies
Inquire about the auditing methodologies used by the auditor. Effective auditors employ a combination of manual code reviews and automated tools to ensure a thorough examination. Understanding their approach will help you gauge the depth of their analysis and the reliability of their findings.
Types of Audits

In the realm of blockchain security, each audit type brings unique advantages, and a combination of all these methods is often the most effective approach to achieving robust protocol security.
Traditional Audits
Conducted by specialized firms, traditional audits offer a deep, systematic analysis of a project’s code, typically focusing on one-time assessments. At Three Sigma, we’re known for our structured approach to identifying and mitigating vulnerabilities, ensuring that critical security issues are addressed comprehensively.
Bug Bounties
Bug bounty programs provide an open invitation for security researchers to discover and report vulnerabilities. These programs are highly beneficial for protocols because they encourage ongoing, proactive security testing by a global pool of experts. Instead of relying on a single, time-limited audit, protocols gain continuous protection as researchers can report issues at any time. This approach not only increases the chances of finding critical vulnerabilities before malicious actors do, but it also builds trust with the community by demonstrating a commitment to security. A prime example of a bug bounty platform is Immunefi, the industry leader in web3 bug bounties, known for hosting some of the largest bounties and payouts in the blockchain space.
Contests
Audit contests invite multiple security researchers to analyze a protocol’s code within a set timeframe. Platforms like ImmuneFi, Code4rena, Sherlock, CodeHawks, and Cantina host these contests, creating competitive environments where many experts work simultaneously to uncover potential issues.
Why Choose Three Sigma as Your Security Partner?

At Three Sigma, we’re more than just auditors, we’re your dedicated security partner, committed to protecting every part of your blockchain application.
We don’t just check boxes; we work closely with your team to ensure your smart contracts are secure, resilient, and prepared to excel in Web3’s fast-evolving landscape.
Here’s what sets us apart:
Holistic Security Strategy: We don’t just perform audits; we develop a deep understanding of your project’s unique needs and goals, integrating security into every stage of development.
Ongoing Support and Guidance: Our team remains available beyond the initial audit, offering continuous insights and updates to help you adapt to evolving security challenges. We're with you every step of the way.
Proactive Risk Management: With our extensive experience across various blockchain applications, from DeFi protocols to NFTs and beyond, we anticipate potential vulnerabilities and provide actionable solutions before issues arise.
Long-Term Partnership: At Three Sigma, we view our relationship as a partnership, not a transaction. Your success is our priority, and we’re committed to securing your project for the long run.
Our Expertise
With over 100 successful audits, our team has a proven record of safeguarding blockchain applications across multiple domains, including AMMs, bridges, gaming, Layer 1 solutions, zero-knowledge (ZK) protocols, derivatives, stablecoins and more. We have identified and addressed more than 1000 vulnerabilities, collaborating with top-tier institutions to strengthen their platforms against the latest security threats.
Our Approach: Clear, Collaborative, Comprehensive
At Three Sigma, we ensure a thorough audit process that offers critical insights and actionable guidance:
- Define Scope and Timeline: We work closely with you to establish a clear audit scope, timeline, and transparent pricing from the start.
- Collaborative Repository Management: By forking the project repository, we enable seamless issue tracking and communication throughout the audit process.
- Fix Verification: After the initial audit, we conduct a dedicated review of all fixes to ensure they meet our high standards.
- Detailed Report Delivery: We provide a final report that outlines vulnerabilities, potential impacts, and recommended fixes, designed to enhance security and confidence in your platform.
Proven Results
Our effectiveness is reflected in our statistics:
- 90% of audits identify critical/high vulnerabilities
- Over 300 high/medium vulnerabilities found
- 100+ successful audits completed
Don’t leave your project’s security to chance. Choose the correct auditor for your smart contract auditing needs and ensure your users’ funds are protected.
Contact us today to schedule a consultation or request a quote, and let our experts safeguard your application!
Conclusion
Smart contract audits are not just a recommended security measure, they are an essential component of any successful blockchain project. As demonstrated throughout this article, the stark contrast between audited and non-audited protocols reveals the critical role these blockchain security audits play in protecting digital assets and maintaining user trust. The decision to invest in a smart contract audit can mean the difference between a thriving protocol and a devastating exploit. While audited projects like Polygon have demonstrated resilience against attacks, cases like the Ronin Network breach ($624M loss) serve as stark reminders of what can happen without proper security measures.
When selecting an auditor, projects should prioritize:
- Proven expertise in their specific niche (e.g., DeFi, bridges, or Layer 1 solutions)
- A comprehensive audit methodology that combines automated tools with manual review
- A strong track record of identifying and addressing vulnerabilities
- Clear communication and transparent reporting practices
The optimal timing for audits varies by project stage, but conducting thorough security assessments before mainnet deployment and after significant updates is crucial. Additionally, implementing multiple security layers—including traditional audits, bug bounties, and audit contests—provides the most robust protection against potential threats.
In an ecosystem where code is law and security breaches can have irreversible consequences, the value of professional blockchain security audits cannot be overstated. Employing best blockchain security practices and selecting experienced auditors helps to secure DeFi platforms, protect digital assets, and build trust among users and investors. Choosing the right partner is just as important as understanding what a smart contract audit is and why it is necessary. By following best practices and working with experienced auditors, you can ensure your blockchain projects remain secure and resilient.
Frequently Asked Questions (FAQ)
Why are smart contract audits essential?
Smart contract audits are critical for maintaining the security of decentralized applications (dApps) and protecting user assets. They help prevent exploits that could lead to financial losses and reputational damage, especially in high-stakes environments like DeFi and NFTs.
How often should smart contracts be audited?
Conducting a smart contract audit is not just a one-time event; it’s a strategic process that should align with key milestones in a project’s lifecycle. An audit at the right time can safeguard a project’s security, functionality, and reputation.
What are the benefits of having a smart contract audit?
The key benefits of a smart contract audit include:
- Risk Mitigation: Identifying and fixing vulnerabilities before they can be exploited.
- Code Integrity: Ensuring the contract functions correctly within immutable blockchain environments.
- User Confidence: Enhancing trust among users, investors, and stakeholders by demonstrating a commitment to security.
What types of vulnerabilities do audits typically identify?
Audits can uncover a range of vulnerabilities, including:
- Reentrancy attacks
- Access control issues
- Logic errors in business rules
What is the process of a smart contract audit?
The audit process generally involves several key steps:
- Pre-Audit Preparation: Defining the audit scope and gathering documentation.
- Code Review: Analyzing the code for vulnerabilities and best practices.
- Testing Phase: Executing unit and integration tests to validate functionality.
- Vulnerability Assessment: Identifying weaknesses and recommending solutions.
How much does a smart contract audit cost?
The cost of a smart contract audit can vary significantly based on the complexity of the contract, the scope of the audit, and the auditing firm’s expertise. Generally, prices range from a few thousand dollars to tens or hundreds of thousands, depending on the project’s requirements.
Who conducts smart contract audits?
Smart contract audits are typically conducted by specialized blockchain security firms or independent auditors with expertise in smart contract development and security. These professionals employ both manual and automated tools to ensure a thorough examination.
What are some examples of smart contract exploits?
Examples include:
- Abracadabra Money: A vulnerability allowed the inflation of borrow shares, resulting in $6.5 million in losses.
- Ronin Network: A major exploit that led to the theft of $624 million due to inadequate security measures.
Can audited smart contracts still be exploited?
While audits significantly reduce the risk of vulnerabilities, they cannot guarantee absolute security. New exploits can emerge, and existing contracts may have unforeseen weaknesses. Continuous monitoring, an Incident & Emergency Response plan, and regular audits are recommended for ongoing security.
What is the difference between immutable and upgradable smart contracts?
Immutable smart contracts cannot be altered once deployed, making audits even more critical to catch potential vulnerabilities beforehand. In contrast, upgradable contracts can be modified post-deployment, allowing developers to address issues but also introducing risks if not managed properly.
How do smart contract audits improve DeFi projects?
Audits enhance the security and reliability of DeFi projects by identifying potential threats before they can be exploited. This proactive approach builds trust with users and investors, contributing to the long-term success and sustainability of decentralized finance solutions.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.