Introduction
“Move fast and break things.”
In the Web3 startup world, this mantra often morphs into a Fast Ship Fallacy, the belief that shipping your product quickly is all that matters and security can be handled later. As an early-stage Web3 founder, you’re laser-focused on building and scaling. It’s tempting to treat security as a later problem. After all, a web3 audit can be expensive and you’re racing to MVP.
But here’s the hard truth: security delays aren’t just dangerous, they’re potentially fatal to your project’s success. In 2024, crypto hacks and scams erased ∼$2.5 billion, and by May 2025 the industry has already lost roughly ∼$2 billion more. The good news? Early security isn’t a blocker to progress, it’s a force multiplier that can actually accelerate your growth.
In this article, we’ll explore why embedding security from day one is critical and show how you can weave security into your startup’s DNA without slowing down.
What “Early-Stage” Really Means (and Why Security Gets Ignored)
In the context of this discussion, “early-stage” Web3 projects are those in their infancy, perhaps a small team with a groundbreaking idea, pre-Mainnet or just launched on Testnet, and likely pre-audit. You might have a working prototype or MVP, a bit of seed funding, and a tight race to iterate and find product-market fit. Early-stage often means wearing multiple hats and making tough trade-offs. Founders in this phase commonly postpone security due to limited resources and the pressing need to ship features. This is understandable: you might assume that with a small user base or little total value locked (TVL), “who would even attack us?”
Yet history shows that no project is “too small to hack.” Attackers frequently target young protocols precisely because they expect weaker defenses. And early-stage code is often untested and unaudited, making it low-hanging fruit. The Fast Ship Fallacy tricks founders into thinking security will only slow them down, when in reality a major security incident early on can halt your project permanently. Let’s break down why prioritizing security from day one is not just prudent, it’s essential for Web3 founders, and how it can actually propel your project forward.
5 Reasons to Prioritize Web3 Security from Day One
1. A Single Hack Can Kill Your Project

Early security mistakes can be devastating, sometimes outright fatal. In Web3, one exploit is all it takes to drain your funds, wreck your token’s value, and destroy user confidence overnight. Real-world example: Abracadabra Money, a DeFi lending protocol, learned this the hard way. In early 2024, an attacker leveraged a flaw in the protocol’s debt accounting logic to turn 1 ETH into $6.49 million of stolen funds. The vulnerability (an unchecked “shares” mechanism) let the attacker inflate their borrow balance and extract $6.4M in Magic Internet Money (MIM) stablecoins.
Want to see the exploit step by step? Check the full analysis we at Three Sigma crafted for you: “Abracadabra Money Exploit Analysis -1 ETH to $6.49M”.
Fast forward a year, and another exploit struck Abracadabra, this time draining $13M by bypassing solvency checks via a clever manipulation of failed collateral orders. Two massive hacks in two years, both rooted in early design oversights, underscored a painful lesson: if you don’t address security early, it will come back to bite you. And many projects don’t get a second chance, a serious hack can irreparably tarnish your brand or even bankrupt your treasury.
Get the complete post-mortem of the second attack in “Draining the Cauldron: Inside the $13M Abracadabra GMX V2 Exploit”.
The takeaway for founders is clear: don’t gamble your entire project on the hope that “we’ll handle security later.” By the time “later” comes, it might already be game over. Users and investors have long memories in crypto; a hack at launch can permanently label your project as unsafe. It’s far better to prevent the fire than to do damage control after the fact. Even if you manage to reimburse losses, the trust hit is hard to recover. Prioritizing security from day one is like vaccinating your startup against an otherwise lethal disease. It keeps your project alive long enough to thrive.
2. It Builds Trust and Confidence from the Start
Web3 is built on trust and transparency. Early adopters of your dApp or protocol are putting faith in your code, and nothing evaporates that goodwill faster than a security failure. By contrast, making security a core value from the beginning sends a powerful signal to users, partners, and investors. It shows you value their funds and data as much as they do. Consider how user trust compounds: a secure track record, even in the early stages, makes people more comfortable depositing assets or trying your innovative DeFi app. Conversely, one exploit (even if it’s “only” a few hundred thousand dollars) can sow doubt about your team’s competence.
Security-focused founders gain a reputation advantage. For example, projects that go through rigorous audits or release formal security reports early often see community praise. In investor meetings, being able to point to your security processes, code reviews, and audit plans can set you apart from the pack of “move fast, break things” startups. In fact, many savvy investors now do security due diligence, they’ll ask if you’ve had an audit or what your plan is to mitigate risks. Showing that you’ve thought about secure smart contract design and operational security from day one can tip the scales in your favor. It demonstrates maturity and foresight.
In short, early security is a trust multiplier. Just as an insecure product can scare away users, a robustly secure product (even in beta) can attract a loyal following that appreciates your professionalism. This trust will be crucial as you grow and face competitors. Users will stick with a project that has kept them safe. And when you eventually expand to managing more value, you’ll already have proven practices to safeguard it, giving everyone, including your team, more confidence to innovate rapidly.
3. It’s Easier (and Cheaper) to Fix Issues Now vs. Later

Security debt is like technical debt, it compounds over time and becomes exponentially harder (and costlier) to address later. Founders often think they’re “saving time” by skipping security steps early on, but in reality they’re accruing a hidden liability. A design flaw in a smart contract architecture might be trivial to fix when it’s just a few hundred lines of code and a handful of users. But if you only discover that flaw during a late-stage audit or, worse, after a breach in production, the fix could require major refactoring, delays, and public disclosures that damage your credibility.
Think of it this way: you wouldn’t build a skyscraper without laying a solid foundation on day one. Trying to reinforce a shaky foundation when the building is half-built is infinitely harder. Likewise, secure smart contract design baked in from the start means you won’t have to rip apart critical components right before launch because “oops, we forgot to handle re-entrancy properly” or “we used an outdated library.” Addressing such issues early costs far less than emergency patching under duress. As one example, the first Abracadabra exploit mentioned earlier could potentially have been caught with more thorough design review of the debt share logic (which turned out to be flawed). Fixing that design before deployment would have been routine; cleaning up a $6M mess afterward was an ordeal.
Moreover, security incidents can kill your business outright and in the best-case scenario, they’re still incredibly expensive, not just in lost funds, but in opportunity cost. Time spent on incident response, forensic analysis, legal issues, and communicating to angry users is time not spent improving your product. By contrast, investing a bit of time in preventative security (like code reviews and testing) early on can save you weeks or months of firefighting later. In practical terms, scheduling a smart contract audit well before your mainnet launch (or even a lighter audit for your MVP) helps you catch critical bugs when they are cheapest to fix. Many auditors, including Three Sigma, even offer design reviews or architecture consultations, allowing you to validate your approach before you write thousands of lines of vulnerable code. Catching a design-level bug in a one-day review beats discovering it after you’ve built an entire ecosystem around it.
4. Your Attack Surface Is Bigger Than You Think (Front-Ends, SDKs & OpSec)
When founders hear “Web3 security,” they usually think smart contracts. But in reality, your app’s security is only as strong as its weakest link, and that might not be the solidity code at all. Many high-profile attacks have targeted the off-chain components of Web3 projects: front-end websites, developer tools (SDKs), or the operational security of the team. Front-end exploits are especially insidious. A DeFi dApp’s user interface can be hacked or spoofed to trick users into signing malicious transactions, even if the smart contract itself is sound. Remember the Curve Finance DNS hijack? Attackers briefly took over Curve’s front-end via a domain hack, redirecting users to a phishing site and draining wallets, a painful reminder that securing the UI and DNS is as crucial as securing the contract. As a founder, if you neglect front-end security, you’re leaving the door wide open for attackers. A compromised front end can trick users into signing malicious transactions, which are then sent to your smart contracts. Even if your contracts are secure, they’ll execute the signed instructions, because from the contract’s perspective, the user willingly authorized them. Simply put, front-end code needs audits and protection just like your contracts do. Common vectors include DNS hijacking, script injection, and supply chain attacks via NPM libraries. (Yes, even a humble JavaScript dependency can backstab you, in late 2024, a compromised NPM package @solana/web3.js exposed private keys and let hackers steal funds from thousands of wallets!)
Read our field report “DeFi Front-End Exploits: Security Attacks & Risks” to learn practical counter-measures.
SDKs and developer tools pose another hidden risk. As Three Sigma’s guide on SDK audits explains, these software development kits often handle critical operations off-chain, wallet connections, transaction signing, etc. If an SDK you rely on is insecure, it can bypass even the most robust on-chain safeguards.
A real-world case: in 2023, Ledger’s Connect Kit SDK, used to integrate hardware wallets into dApps, was compromised through a supply chain attack. A former Ledger developer’s npm credentials were phished, and attackers published malicious versions of the SDK containing transaction-manipulating malware. Users interacting with apps that had unknowingly updated to the tainted version were tricked into signing transactions that sent funds directly to the attackers. Ledger responded quickly and patched the package, but the incident revealed just how devastating a compromised SDK can be, not due to flaws in the smart contracts, but through tampered developer tooling.
Because SDKs are widely shared across Web3 apps, a single vulnerability can cascade into a multi-project disaster. Early-stage teams often move fast with open-source packages, but without vetting, this can be a massive liability. Secure everything that touches users’ keys or transaction flows, and consider an SDK audit if your app heavily depends on one or ships its own.
Building or relying on an SDK? See “Why SDK Audits Are Critical for Web3 Security” for a checklist of pitfalls and best practices.
Finally, Operational Security (OpSec) for your team is part of your project’s security infrastructure. You and your co-founders might hold admin private keys, deploy contracts, manage multisig wallets, or control domain accounts. Attackers know this and will target you through phishing, malware, and social engineering. One of the largest DeFi thefts of 2024, the $50M Radiant Capital exploit, wasn’t a smart contract bug at all; it was caused by malware on developers’ computers, which let attackers hijack a multisig and issue fraudulent transactions. In other words, poor OpSec (unguarded devices, lack of key segregation) can trump even perfectly written code. Enterprise crypto OpSec should be treated as core infrastructure from day one. Simple steps like using hardware wallets for admin keys, requiring multi-factor authentication on all critical accounts, and segregating duties can prevent many attacks.
A secure product needs a secure team. Our comprehensive guide “Enterprise Crypto OpSec: A Guide for Companies” walks you through key-management, device hardening, and insider-threat defenses.
Don’t wait for a near-miss (or a disaster) to realize your operational security gaps, plan for them upfront. The bottom line is that holistic security (contracts and front-end and ops) must be part of your early roadmap. Ignoring any piece of the stack gives attackers an opening you can’t afford.
5. Security is a Growth Accelerator, Not a Roadblock
Perhaps the most counterintuitive reason: embedding security early will make you faster, not slower. The Fast Ship Fallacy paints security as friction, something that drags down development and delays launch. In practice, the opposite is true. When you integrate security mindset into your development process, you end up building a more solid product that you can scale and iterate on confidently. You spend less time putting out fires and more time adding features. Think of security as quality assurance: code that passes security muster is often higher quality code, with cleaner logic and fewer bugs. This reduces those “mysterious issues” that crop up later and eat up engineering time. Knowing that your contracts and infrastructure are secure also lets you move faster on growth, you can pursue partnerships, listings, and integrations without fear that some lurking vulnerability will derail the effort.
Security can even be a marketing edge. In a space rife with hacks, being one of the projects that didn’t get hacked is a selling point. Users will more readily try out new features or lock value in your protocol if they’ve seen you handle security diligently. This confidence internally and externally acts as a force multiplier. It’s much like race cars: they have powerful brakes so they can drive faster. In Web3, robust security practices are your “brakes”, they let you accelerate innovation because you know you can safely handle sharp turns. Moreover, many security best practices align with good development practices (like thorough testing, code reviews, and clear access controls), which naturally improve your development velocity and reduce costly rework.
Crucially, baking in security doesn’t mean you must achieve perfection or halt all development for audits. It means adopting a preventive mindset: thinking about how someone might abuse a feature while you design it, adding a checklist item for security in your definition of “done” for each sprint, encouraging your engineers to flag potential risks early, and so on. By doing this, you create a culture where security is everyone’s job, not a last-minute box to check. This culture pays dividends as you grow, new hires will follow the patterns you set, and security won’t remain a bottleneck that only external auditors handle once a year. Instead, it becomes an integral part of your agile process. In sum, security is a product feature that enhances your overall offering. Treating it as such from day one will propel your project forward, not hold it back.
Common Security Pitfalls of Early-Stage Projects
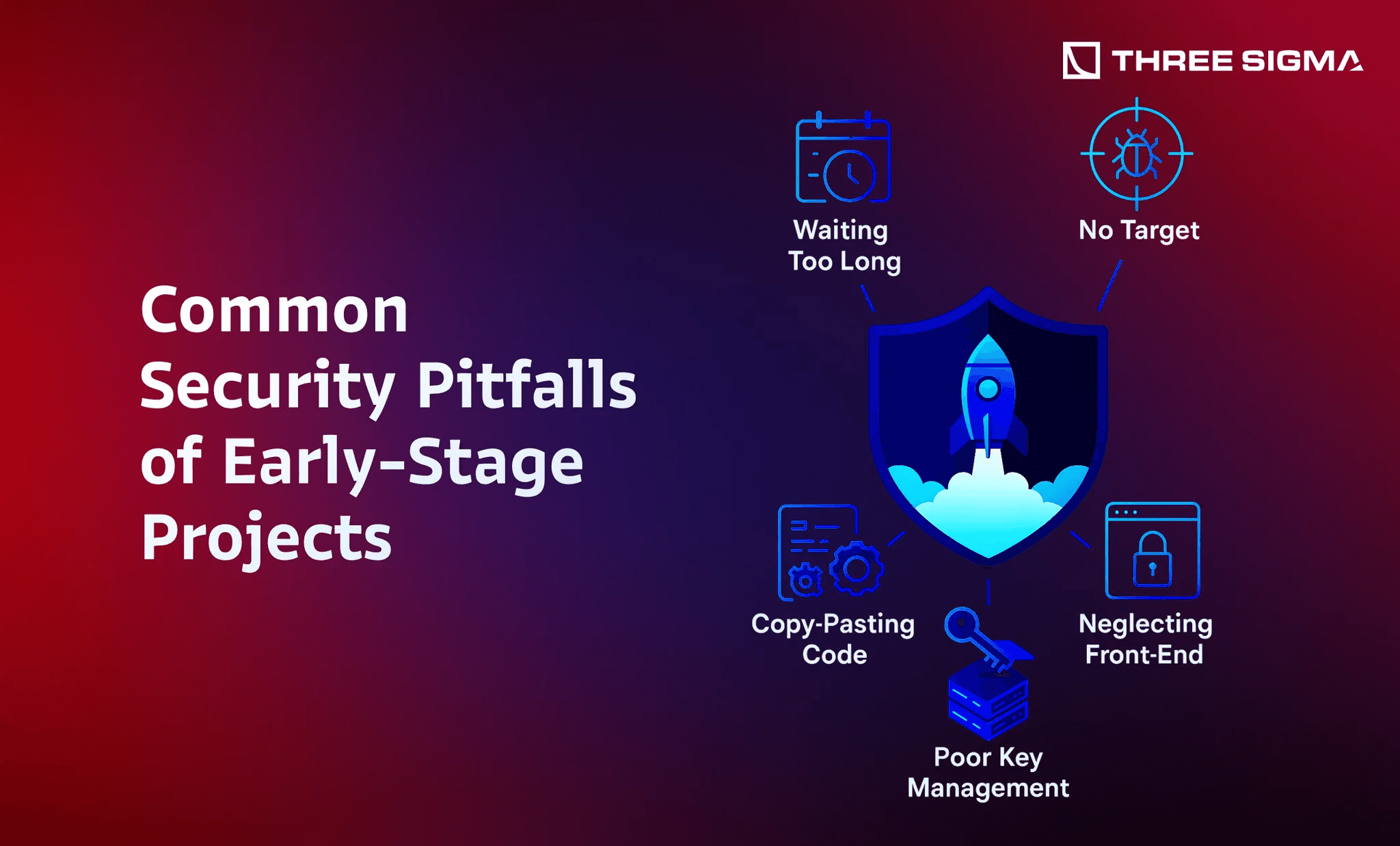
Even with the best intentions, young Web3 startups often fall into a few classic security traps. Here are some common mistakes early-stage founders should beware of:
- “We’ll Audit Right Before Mainnet”, Waiting Too Long: One of the biggest pitfalls is deferring the security audit until the very end. This often leads to last-minute panic when auditors find critical issues that require deep changes. It’s far better to engage with auditors early (even informally) or do interim audits on critical components. Don’t cram all security fixes into the week before launch.
- Assuming Small Scale = No Target: Just because you’re early-stage doesn’t mean attackers won’t bother. Hackers often target contracts with low TVL or new projects to front-run your growth. Never assume “nobody will notice our dApp yet”, automated bots and scanners are always prowling for exploits. If your contracts hold any value or control any keys, you’re a target.
- Copy-Pasting Code Without Understanding: Using open-source code (like forking a DeFi protocol or using libraries) is common, but doing so blindly is dangerous. Founders sometimes import contracts from GitHub hoping the original authors got it right, only to inherit bugs or misconfigure them. Always vet and test any borrowed code. Just because code is public or even previously audited doesn’t guarantee it’s bug-free or fits your use-case.
- Poor Key and Admin Privilege Management: In early development, teams may use a single wallet for deployment, share private keys over chat, or neglect to secure admin accounts. This is a huge risk. All it takes is one leaked key or one phished team member to compromise your whole protocol. Avoid using externally owned accounts with broad privileges; prefer multi-signature wallets for admin controls even in testing, and never expose private keys on an internet-connected machine.
- Neglecting Front-End and Infrastructure Security: Many founders tunnel vision on the smart contract and ignore everything else. They leave their front-end web server, DNS, or APIs with default security, or they don’t monitor for phishing sites. This makes an attacker’s job easy, why fight your code if they can just trick your users via a fake website or a compromised DNS record? Failing to audit your front-end, dependencies, and cloud configs can undermine all the solidity work you did.
By being aware of these common missteps, you can proactively steer your project clear of them. Next, let’s look at what practical steps you can take right now to shore up your early-stage security posture.
What Founders Can Do Early: A Security Jump-Start Checklist
Security isn’t all-or-nothing; there are plenty of pragmatic steps you can take in the early stages of development before you invest in full formal audits. Think of this as your founder security checklist for the MVP-to-Mainnet journey:
- Secure the Design First, Do a Threat Modeling Exercise: Before writing a single line of code (or at least before finalizing your architecture), take time to identify how your system could be attacked. Gather your team and brainstorm potential threats: Where could an attacker manipulate inputs? What happens if price oracles give wrong data? Could someone abuse the smart contract functions in an unexpected sequence? Writing down these scenarios will highlight areas to fortify. If possible, engage professionals for an architecture/design review. We at Three Sigma offer early design consultations where we examine your system design for weaknesses. This can catch high-level issues (like flawed collateral accounting or unchecked assumptions) that would be expensive to fix later.
- Establish Coding Standards and Internal Reviews: As you develop, enforce secure coding best practices. Simple rules like using the recent compiler, adhering to known secure patterns (e.g., checks-effects-interactions in Solidity), and avoiding deprecated functions go a long way. Have a second pair of eyes on every critical piece of code, if you’re the solo developer-founder, consider bringing in an advisor or using an open-source audit community to review your contracts. An internal security checklist can be helpful: e.g., verify access controls on admin functions, validate all external inputs, handle arithmetic safely, etc., for each contract.
- Invest in Testing and Automated Analysis: Testing is your first line of defense. Aim for broad unit test coverage of your smart contracts, covering both expected flows and edge cases (what happens if someone tries a negative amount? What if an address calls a function that only a contract should?). Use property-based tests or fuzz testing to discover unexpected behaviors. High test coverage will also make any audit smoother and faster (auditors appreciate well-tested code!).
- Don’t Forget Front-End and SDK Security: If your project has a web front-end or uses a Web3 SDK, treat that code as part of your attack surface. Lock down your DNS (use registrars with 2FA and DNSSEC), and consider serving your app on IPFS or ENS for extra safety. Review the third-party packages in your app, remove or update any with known vulnerabilities. Down the line, schedule a frontend security audit or penetration test to catch issues like XSS (cross-site scripting), CSRF, or logic flaws in how transactions are generated. The same goes for any custom SDK or backend service: get a security review of those components. Remember, an exploit via a compromised SDK can be just as disastrous as a smart contract hack.
- Implement Basic OpSec Hygiene for the Team: As a founder, set the security tone for your team’s operations. Use hardware wallets or multi-sigs for deploying contracts and managing treasury funds, no private keys sitting on a laptop! Require 2FA on all critical accounts (GitHub, domain registrar, cloud servers). Segregate duties so that no single person is an undue point of failure (e.g., have multiple approvers for contract upgrades or moving funds). Create an incident response plan, even a simple one, so that if something goes wrong, you know how to pause the protocol (consider adding a safe “circuit breaker” in your contracts), contact stakeholders, and involve experts. Operational security might not be top of mind during coding sprints, but it’s essentially free insurance against very costly disasters.
By tackling the above items, you’ll dramatically reduce your risk before you ever announce your product to the world. You’ll also make any future professional audit much more effective, because auditors can focus on the really subtle issues instead of pointing out basic mistakes. Think of these early actions as security debt payments, small investments now that prevent a huge bill later.
Conclusion: Security from Day One, The Only Way to Build in Web3

The Fast Ship Fallacy would have you believe that security is a luxury for later. But as we’ve explored, it’s a false economy and a dangerous gamble. For Web3 founders, security is the bedrock on which everything else is built, user trust, product integrity, growth, and even your own peace of mind. Prioritizing security early doesn’t hinder you; it empowers you. It means you can innovate faster, scale confidently, and sleep a little better at night knowing you’ve done the due diligence to protect your community and vision.
Web3 is unforgiving to the negligent but rewarding to the diligent. Founders who treat security as a product feature, not a checkbox, ultimately create more resilient, credible, and successful projects. You don’t need to be a security expert yourself; you just need to embrace the mindset and bring in the right help to implement it. Whether it’s learning from the post-mortems of exploits like Abracadabra’s or staying up to date with front-end attack trends, make security a continuous learning process in your startup.
Security isn’t a tax on speed, it’s a dividend. The earlier you invest, the greater the payoff in terms of saved time, avoided catastrophes, and user loyalty. By starting on day one, you ensure that by the time your project hits day 100 or day 1000, you have a solid foundation that won’t crumble under success.
If you’re an early-stage founder building the next big Web3 innovation, now is the time to embed security into your game plan. You don’t have to do it alone. Three Sigma is here to partner with you at every stage, from initial design reviews and threat modeling sessions, to smart contract audits (Solidity, Rust, Move or otherwise), front-end and SDK audits, and even comprehensive OpSec guidance for your team.
We’ve helped projects dissect exploits and harden their defenses, and we’re passionate about making security a growth enabler for startups. Don’t wait for a hack to make security a priority. Reach out to Three Sigma for a consultation or audit quote, and let’s build a secure and successful Web3 future together. Your project and your users deserve nothing less.
Frequently Asked Questions (FAQ)
1. Why should early-stage Web3 founders care about security before launch?
Because even a single exploit can drain funds, destroy token value, and permanently erode user trust. Building security in from day one prevents catastrophic losses and signals professionalism to investors and the community.
2. What is the “Fast Ship Fallacy” in Web3?
It’s the mistaken belief that shipping quickly is all that matters and security can wait. In reality, postponing security piles up “security debt” that becomes harder, and far more expensive, to fix later.
3. Are small, low-TVL projects really targets for hackers?
Yes. Attackers often scan for new or lightly defended protocols precisely because they expect weaker defenses. No project is “too small to hack.”
4. How does early security improve fundraising and partnerships?
Demonstrating threat modeling, code reviews, and audit plans reassures investors and partners that their capital and reputation are safe, giving your startup a competitive edge.
5. Besides smart contracts, what other components need protection?
Front-end code, SDKs, cloud infrastructure, and team operational security (OpSec) are equally critical. Many high-profile losses stem from DNS hijacks, malicious NPM packages, or stolen admin keys rather than Solidity bugs.
6. Is a full audit mandatory at the MVP stage?
Not always. Founders can start with lightweight architecture reviews, rigorous testing, and internal code checks, then schedule a formal audit before significant value goes on-chain.
7. How does “security debt” compare to technical debt?
Like technical debt, ignored security issues compound over time, but with the added risk of immediate financial loss and brand damage if exploited. Early fixes are faster, cheaper, and less disruptive.
8. What quick wins can founders implement right now?
Use hardware wallets or multisigs for admin keys, require 2FA on all accounts, conduct threat-model sessions, enforce code reviews, and add automated unit/fuzz tests to catch edge cases.
9. Can prioritizing security actually speed up development?
Yes. Secure, well-tested code reduces fire-drills and rollbacks, letting teams iterate faster and focus on growth rather than crisis management.
10. Where can founders get professional help with Web3 security?
Specialized firms like Three Sigma offer design reviews, smart-contract, front-end, and SDK audits, plus comprehensive OpSec guidance tailored to early-stage Web3 startups.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.