Introduction
In the fast-paced world of Web3, most projects prioritize smart contract audits (e.g., a Solidity audit) and operational security. However, a key layer is often overlooked: SDKs—the software development kits that connect dApps, wallets, and blockchain networks. A SDK audit is an essential security service that ensures your developer tools are free from vulnerabilities that could compromise users, funds, or your reputation, and should sit alongside a broader Web3 audit.
In this guide, we’ll break down what SDK audits are, why they matter, and how they’re conducted. This will help you understand why adding SDK audits to your security strategy is not just smart, it's necessary, especially when paired with a Rust Smart Contract Audit for Solana programs. If you’re evaluating blockchain security services for your stack, explore our offerings.
What Are SDK Audits
A Software Development Kit (SDK) audit is a rigorous security evaluation of the libraries and tools developers use to build, extend, or integrate Web3 applications. That’s why a focused dapp audit complements SDK reviews, and if your SDK interfaces with Move-based smart contracts, a dedicated Move audit helps validate critical on-chain assumptions. For more context on the client layer, see our analysis of DeFi FrontEnd Exploits.
Since SDKs operate outside the blockchain’s on-chain consensus, they aren’t confined by the same security checks that protect smart contracts. As a result, a compromised SDK can easily bypass otherwise robust on-chain safeguards. If attackers exploit an insecure SDK, multiple dApps may be exposed at once—leading to large-scale breaches, lost funds, or irreversible reputational harm.
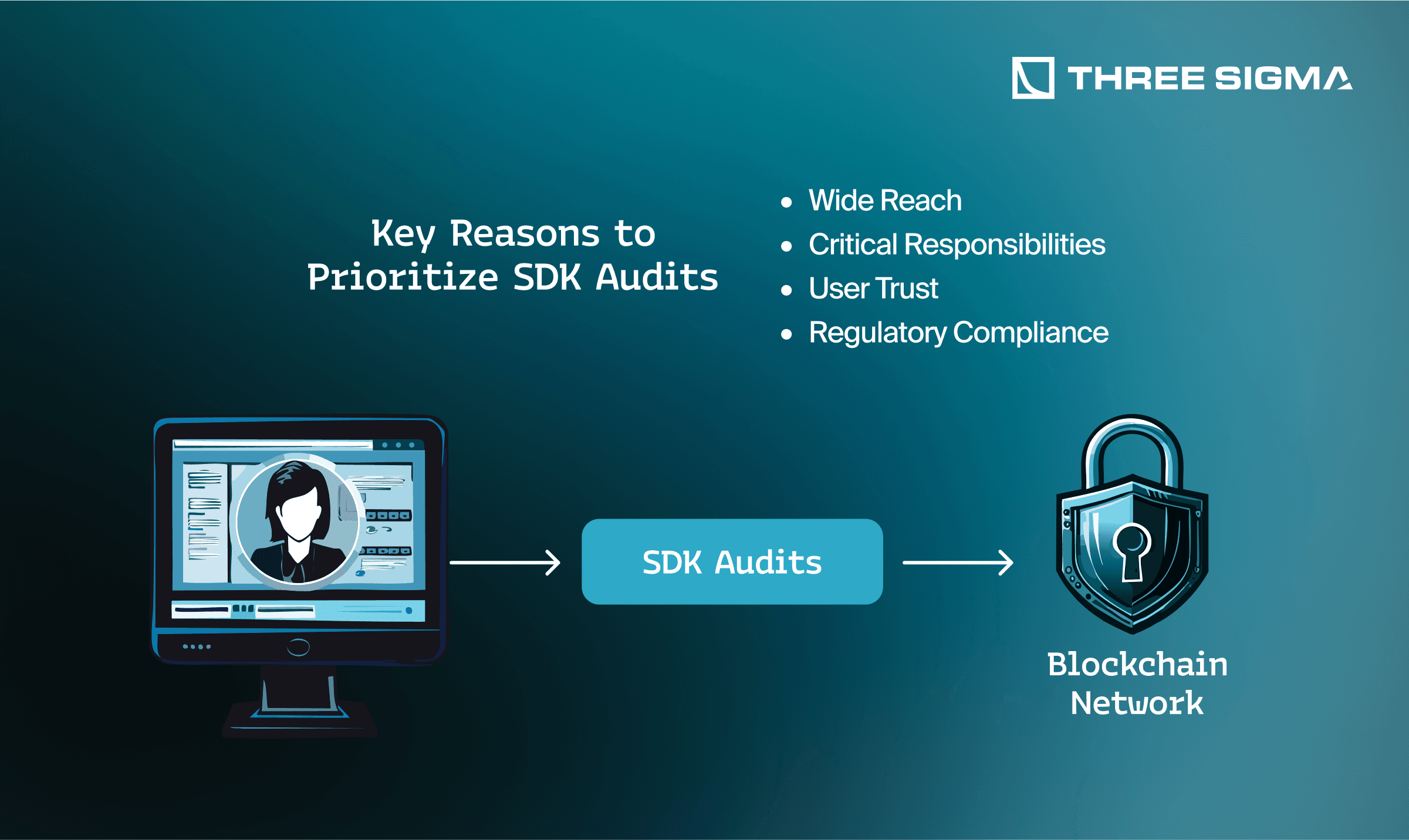
Key Reasons to Prioritize SDK Audits
- Wide Reach: Because many developers share the same SDK, a single vulnerability can snowball across countless projects.
- Critical Responsibilities: An SDK often manages transaction signing, user authentication, and communication channels—core functions that attackers love to exploit.
- User Trust: A security lapse in your off-chain tooling can swiftly damage user confidence, even if your on-chain code is flawless.
- Regulatory Compliance: Especially in regulated industries, comprehensive security measures (including SDK audits) demonstrate both due diligence and adherence to high governance standards.
How SDK Audits Differ from Smart Contract and OpSec Audits
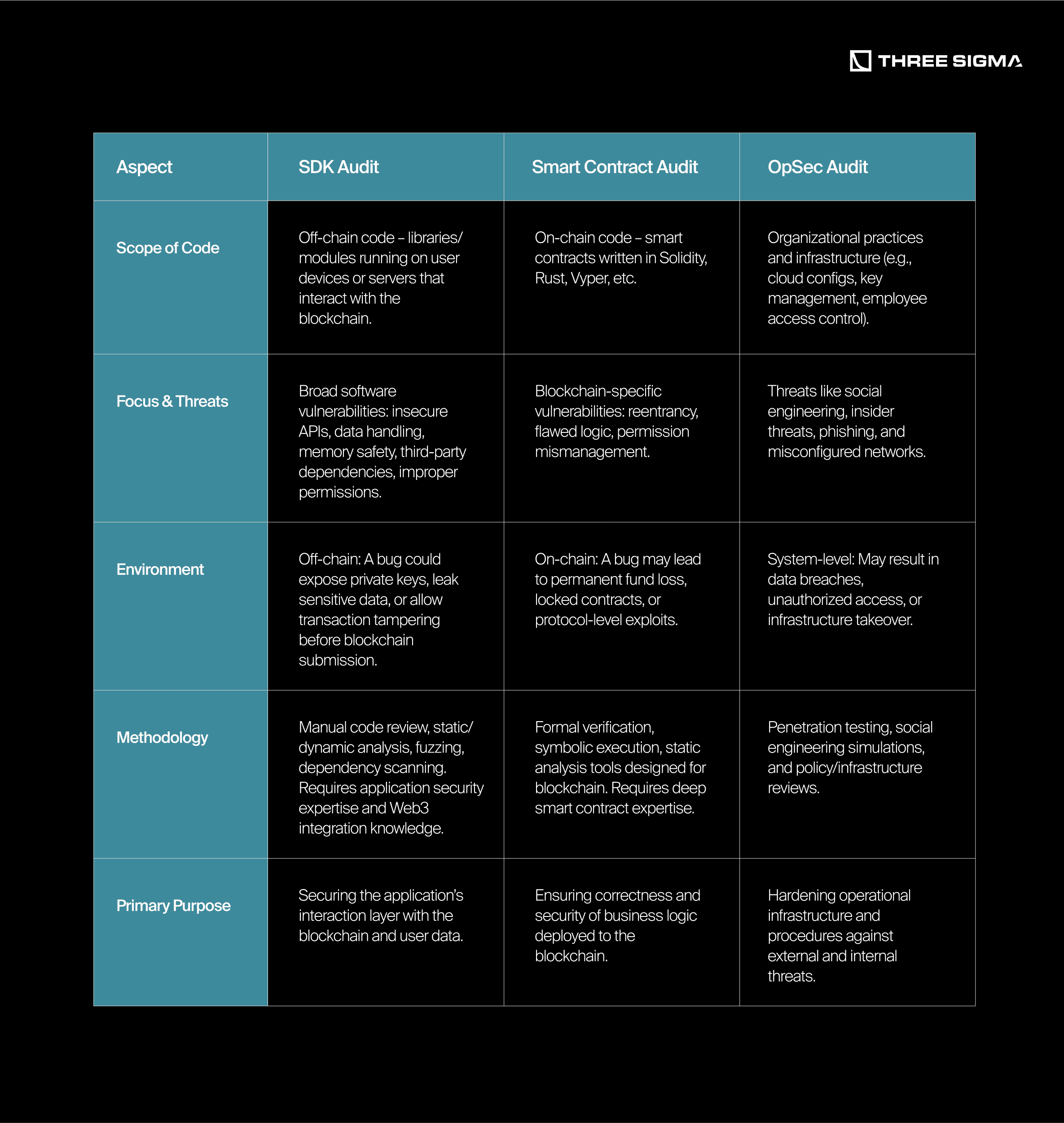
SDK audits focus on securing the off-chain tools that interact with blockchain systems. While smart contract and OpSec audits cover critical areas, SDK audits fill the essential gap between them—securing the glue that connects your application, users, and the blockchain.
Want to dive deeper?
At Three Sigma, we don’t just specialize in SDK audits—we’ve also written comprehensive guides explaining what Smart Contract Audits and OpSec Audits are:
What Is a Smart Contract Audit and How to Choose the Right Security Partner
Crypto OpSec Guide (Part 1): Private Key, Phishing & Security
Key Components and Areas Evaluated in a SDK Audit
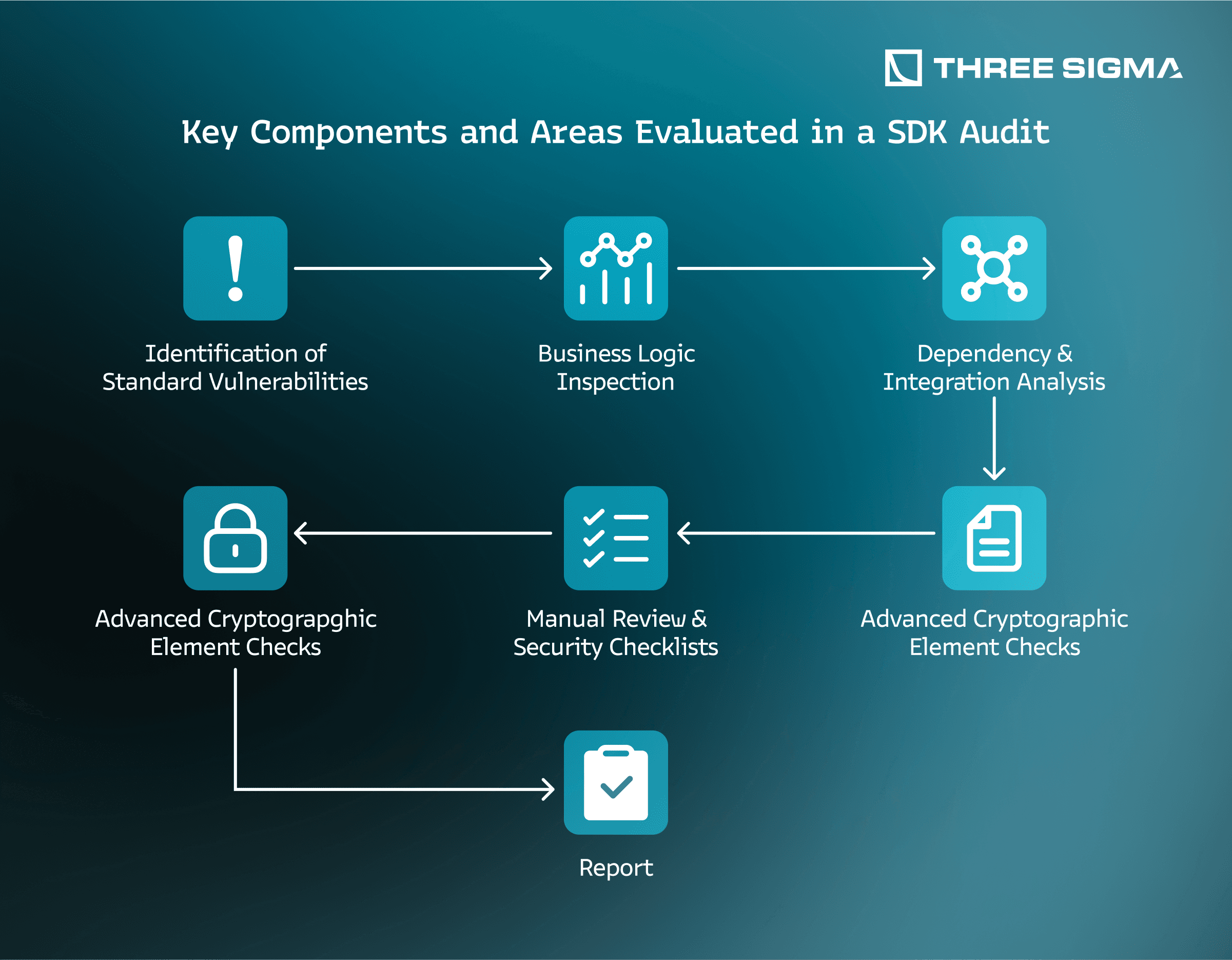
When we at Three Sigma audit a SDK, we follow a multi-stage process designed to uncover both obvious and deeply embedded vulnerabilities. By integrating standard checklists, thorough code reviews, and targeted testing strategies, we ensure your SDK adheres to industry-best security practices. Below are the core facets we evaluate:
1. Identification of Standard Vulnerabilities
SDKs can suffer from a variety of known weaknesses:
- DoS (Denial-of-Service) Susceptibility: Verifying large or malformed inputs cannot crash or overwhelm the system.
- Malicious Library Injections: Examining dependencies for compromised or planted packages.
- Input Validation Flaws: Ensuring all external/user-provided data is properly sanitized to prevent injections.
- Storage Issues: Catching uninitialized, unused, or insecure variables that may lead to vulnerabilities.
2. Business Logic Inspection
Even if an SDK passes standard vulnerability checks, logical flaws can still pose significant risks:
- Workflow & Data Flow Diagrams: Mapping each function to detect potential loopholes, backdoors, or hidden threats.
- Math & Calculations Review: Confirming arithmetic accuracy in crypto or transaction operations to avoid overflows.
- Access Control & Roles: Ensuring privileges, roles, and permissions are robustly enforced with no unintended escalations.
3. Dependency & Integration Analysis
Since most SDKs rely on external libraries:
- 3rd-Party Packages: We verify if each library is up-to-date, free of known CVEs, and properly maintained.
- Integration Tests: Confirming stable, secure communication with external APIs or services.
- Supply Chain Security: Spotting malicious or high-risk dependencies introduced indirectly.
4. Manual Review & Security Checklists
Manual, line-by-line code review remains indispensable:
- Protocol Decomposition: Building an interaction scheme to visualize all data and function flows.
- Backdoor & Deadlock Checks: Searching for hidden code paths and infinite loops.
- Automated Tools & Static Analysis: Complementing human oversight with specialized security scanners.
- Storage & Documentation: Investigating how sensitive data is stored and ensuring clear, consistent documentation.
5. Testing Stage & Validation
This phase validates or refutes potential issues flagged in prior reviews:
- Edge Case Testing: Specialized tests target suspect functions or known problematic inputs.
- Fuzzy & Mutation Tests: Generating random or distorted data to prompt unexpected behaviors.
- Integration & Unit Tests: Checking that cryptographic modules, third-party calls, and core functionalities perform reliably.
- Cross-Compatibility Checks: For SDKs spanning multiple languages (e.g., Rust & TypeScript), confirming they behave consistently across environments.
6. Advanced Cryptographic Element Checks
Cryptographic modules demand a higher scrutiny level:
- Key Management: Ensuring private keys remain encrypted or stored securely.
- Algorithm Usage: Verifying the SDK avoids outdated or proprietary crypto in favor of well-established standards (e.g., secp256k1, SHA-256).
- OWASP & CCSSA (C4) Benchmarks: Aligning cryptographic components with recognized security frameworks where relevant.
7. Comprehensive Reporting & Recommendations
Upon completion, we deliver an in-depth report detailing:
- Identified Risks & Vulnerabilities: Categorized by severity and potential impact.
- Mitigation Strategies: Specific instructions for patching or mitigating each issue.
- Long-Term Security: Recommendations on improving documentation, test coverage, and sustainable development practices.
By adopting this thorough auditing methodology, Three Sigma provides a holistic assessment of your SDK’s security posture—ensuring you can address weaknesses proactively and maintain a robust defense against potential exploits.
Real-World SDK Vulnerability Examples and Lessons Learned

Below are actual cases of exploited vulnerabilities in popular SDKs. Each scenario highlights a unique risk area—ranging from dependency attacks to cryptographic oversights—and underscores the critical need for rigorous off-chain security audits.
Unsafe Dependencies / Supply Chain Attacks
Solana Web3.js Library (2024) – The official Solana JavaScript SDK was compromised when an attacker gained control of an npm publisher account. They released two malicious updates of @solana/web3.js that injected backdoor code capable of stealing private keys and draining funds from any applications (such as bots) using those versions. This supply-chain attack did not affect the Solana blockchain itself, but it targeted the off-chain SDK; projects that unknowingly updated during the brief window had their secret keys exposed.
Ledger Connect Kit (2023) – Ledger’s Connect Kit SDK (used to link hardware wallets to dApps) was briefly hijacked through an npm supply-chain attack. A former Ledger developer’s npm credentials were phished, allowing a malicious release of the package (v1.1.5-1.1.7) with embedded malware. The tampered SDK altered transaction logic – it “allowed hackers to manipulate the functions visible to users, leading them to unintentionally send funds to the attackers” instead of their intended recipients. Ledger’s team caught and fixed the issue within hours, but it highlights how compromised dependencies can inject unauthorized code and redirect crypto assets.
API Vulnerabilities and Logic Flaws
WalletConnect Verify API (2023) – WalletConnect, a popular Web3 wallet connection protocol, introduced a “Verify API” to warn users about suspicious dApp domains. However, a logic flaw (reflected XSS vulnerability) in this web API allowed attackers to inject malicious scripts into the verification prompt. In practice, an attacker could craft a phishing page that triggers the API’s warning but with a payload that deceives users into approving unintended transactions (e.g., granting token allowances without noticing). The root cause was insufficient output sanitization in the API’s domain handling, leading to a classic web vulnerability in a Web3 context.
Cryptographic Weaknesses
Profanity Vanity Address Tool (2022) – Profanity, an off-chain tool used to generate “vanity” Ethereum addresses, was found to have a severe cryptographic weakness. Instead of relying on secure entropy, it used only a 32-bit random seed to generate 256-bit private keys—drastically reducing the effective key space. This allowed attackers to reverse-engineer the vanity address generation process and recover private keys in a fraction of the time it would take with properly generated keys.
The flaw enabled attackers to map public addresses back to their original low-entropy seeds by simulating the deterministic key generation logic. This led to the compromise of several wallets, most notably causing the DeFi market maker Wintermute to lose approximately $160 million.
Permission and Access Control Issues
Stellar Freighter Wallet (2023) – The Freighter browser wallet SDK (for Stellar) contained an access control bug that allowed any website to interact with privileged wallet functionality without user consent. Specifically, due to improper message handling in the extension, a malicious site could send a crafted request indistinguishable from the wallet’s own UI, tricking Freighter into revealing the user’s secret recovery phrase in the background. This meant an attacker could extract the private key (recovery phrase) just by luring a user to visit a webpage – no click or approval needed.
Coin98 Wallet Extension (2023) – A similar logic flaw affected the Coin98 browser wallet. Its internal API exposed a developer flag that, when set (isDev:true), made the wallet treat incoming messages as if they were authorized UI actions. An attacker’s webpage could send such a message to unlock the wallet and even trigger transactions without any user approval. In effect, this access control lapse allowed remote, invisible draining of funds – the wallet would sign and broadcast transactions as though the user had confirmed them.
Error Handling and Data Leakage
Coinbase WaaS SDK (Lindell17 Vulnerability, 2023) – Researchers uncovered a flaw in several wallet SDKs implementing the Lindell17 two-party ECDSA signing protocol. The issue (CVE-2023-33242) arose from improper error handling: if a signing attempt failed, the protocol’s implementation did not safely abort but leaked a small piece of the private key. An attacker with the ability to induce signing errors could repeatedly trigger failures and glean 1 bit of the key per attempt, eventually reconstructing the entire 256-bit private key after ~256 attempts. The root cause was deviating from the published protocol by ignoring abort conditions, leading to sensitive information disclosure through side-channel error data.
These vulnerabilities, while diverse, share a common theme: they are preventable with diligent oversight. To safeguard your dApp and protect user assets, a thorough SDK audit is essential.
Conclusion
A secure Software Development Kit is the cornerstone of any successful Web3 application. Even the most bulletproof smart contracts and well-hardened infrastructure can be compromised by weaknesses in off-chain code. SDK audits bridge this critical gap, ensuring that the developer tools you depend on are not silently jeopardizing user assets, brand reputation, and regulatory compliance.
By thoroughly inspecting your SDK’s architecture, code quality, cryptographic modules, and dependencies, you preempt vulnerabilities and build a fortress around your core functionalities. An SDK audit isn’t just a defensive measure—it’s a strategic investment that fosters user trust, expedites regulatory approvals, and preserves the long-term value of your project.
Ready to fortify your Web3 toolkit?
Schedule an SDK Audit with Three Sigma and secure the foundation of your decentralized ecosystem today.
Frequently Asked Questions (FAQ)
1. Why do I need an SDK audit if my smart contracts are already secured?
Securing your on-chain code is vital, but SDKs run off-chain and can introduce vulnerabilities just as serious as those found in smart contracts. By auditing your SDK, you ensure the tools connecting users to the blockchain are just as robust and trustworthy.
2. How often should I schedule an SDK audit?
Ideally, an SDK audit should be performed after every code update, particularly if you add new features, modify critical logic, or introduce new dependencies. Many teams still opt for periodic full-scope audits—such as yearly or biannual reviews—to stay ahead of evolving threats. However, smaller targeted audits after each code change are the best way to ensure ongoing security and minimize the risk of newly introduced vulnerabilities.
3. What is the typical timeline for an SDK audit?
Timelines vary depending on scope and complexity. A smaller SDK can be reviewed in a few days, while more extensive codebases with multiple integrations might take two to three weeks or longer.
4. Do SDK audits cover third-party libraries or only in-house code?
A comprehensive SDK audit includes all dependencies, integrations, and third-party libraries. This approach helps detect supply-chain risks—one of the most common vectors for malicious code injection.
5. Will the audit disrupt my ongoing development?
Most auditors work off existing code repositories and do not require access to production systems, so disruption is minimal. If fixes are needed, you can schedule patch releases or hotfixes as advised in the final audit report.
6. Does an SDK audit help with regulatory compliance?
Yes. Financial, gaming, and enterprise projects often rely on third-party audits to prove due diligence in risk management. An SDK audit can bolster compliance efforts by demonstrating that both on-chain and off-chain components meet rigorous security standards.
7. Will I receive a detailed security report after the audit?
Absolutely. You’ll get a comprehensive report that outlines each identified issue, its severity rating, potential impact, and clear recommendations for remediation. This final document also includes an executive summary that’s easy to share with stakeholders and non-technical team members.
8. What if my SDK is closed-source or proprietary?
Closed-source code can still be audited. Reputable auditors typically sign non-disclosure agreements (NDAs) to protect your intellectual property. Audits focus on identifying vulnerabilities and do not require code to be publicly accessible.
9. Can I request re-verification once issues are fixed?
Yes. Many auditing firms—including Three Sigma—offer re-verification services (sometimes called a “follow-up audit”) to ensure that patches and updates fully address any reported vulnerabilities.
10. Do SDK audits include performance optimization?
While the primary goal is security, an SDK audit can highlight performance bottlenecks—especially if they present a denial-of-service (DoS) risk. However, deeper performance optimizations usually require a separate assessment or specialized review.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.