Introduction
At Three Sigma, we recognize the intricate opportunities within the Web3 space. Based in Lisbon, our team of experts offers premier blockchain audit services in development, security and economic modeling to drive your project's success. Whether you need precise code audits like our solidity audits, or you’re shipping a web UI and need a thorough dapp security audit, Three Sigma is your trusted partner. Building cross-chain?
Our blockchain bridge audit helps de-risk complex interoperability. We are not just experts in code, economic auditing, and blockchain engineering—we are passionate about breaking down Web3 concepts to drive clarity and adoption across the industry.
Pendle Finance
Pendle is a decentralized, permissionless protocol designed for yield trading, enabling users to implement a variety of yield management strategies. If you’re building in the Move ecosystem (e.g., Aptos/Sui), consider our move smart contract audit to validate core protocol assumptions.
To fully grasp how Pendle works, it is important to understand its three main components:
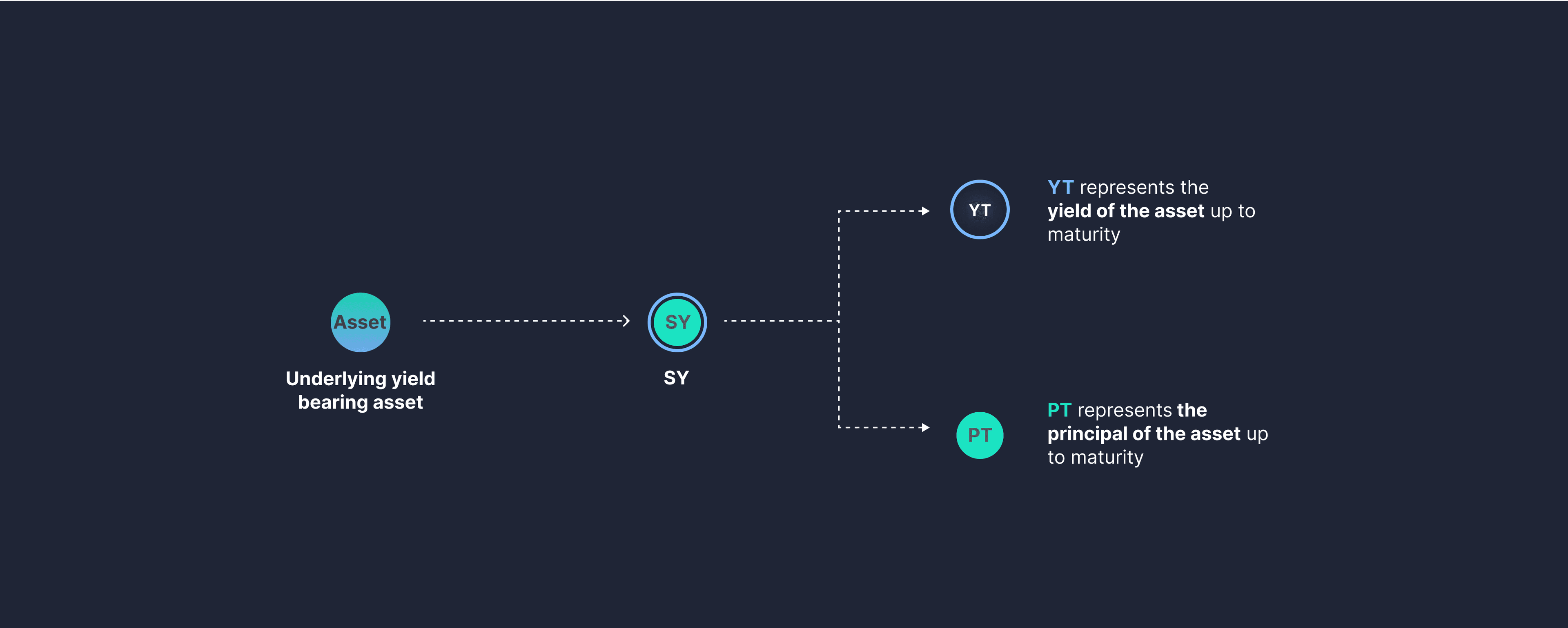
- Yield Tokenization Pendle allows users to wrap yield-bearing tokens into SY (standardized yield tokens), making them compatible with Pendle’s AMM. For instance, a yield-bearing token like stETH can be converted into SY-stETH. This SY token is then split into two parts: the PT (principal token) and the YT (yield token), representing the principal and yield portions of the asset. This process, called yield tokenization, separates the yield into its own tradable token.
- Pendle AMM Both PT and YT can be traded on Pendle’s AMM (automated market maker). While the AMM is central to Pendle’s functionality, understanding its mechanics isn’t necessary to trade PT and YT.
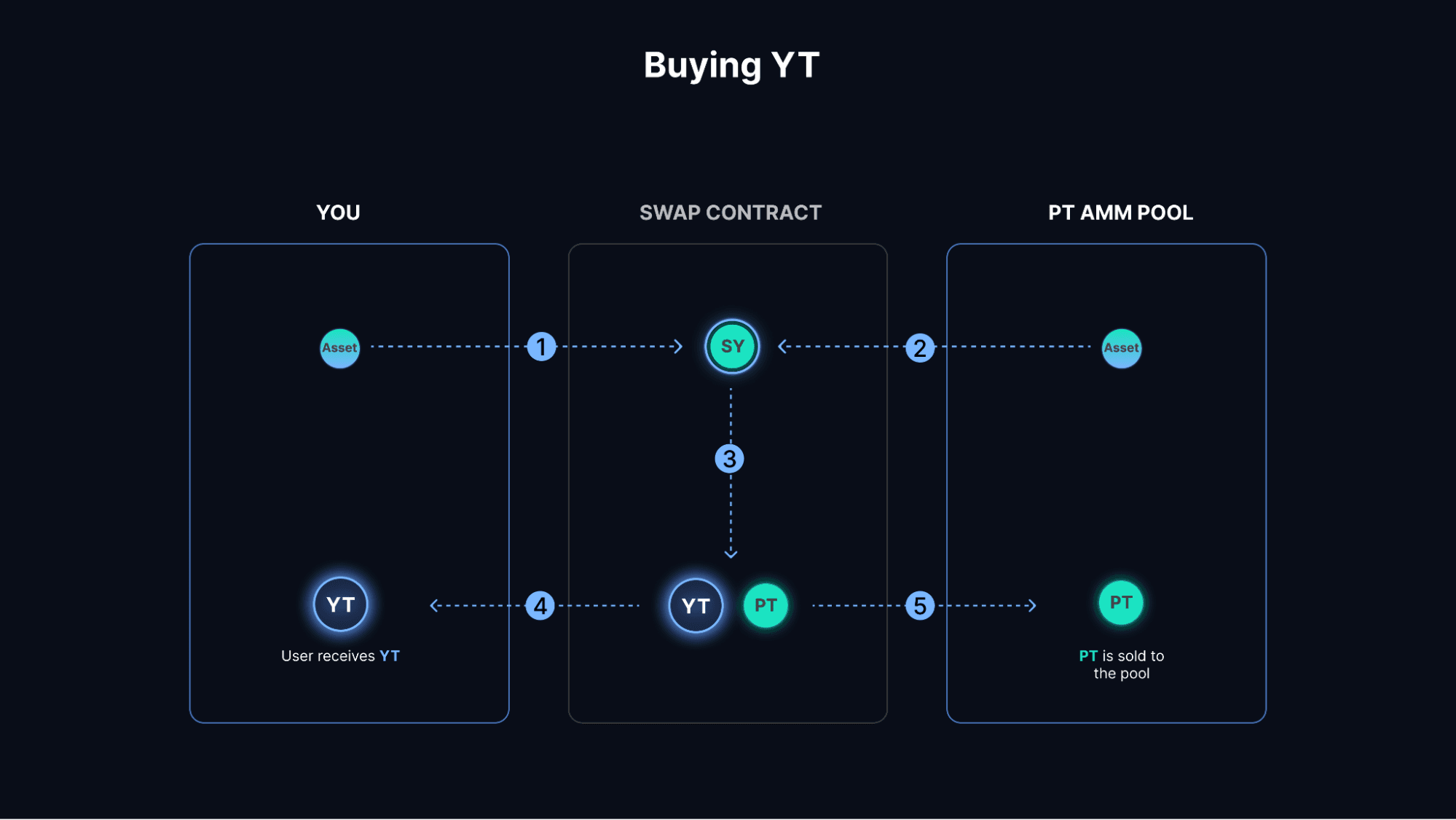
- vePENDLE Pendle’s governance is powered by vePENDLE. Users can lock PENDLE tokens to receive vePENDLE, with longer lock durations resulting in a higher vePENDLE value. The vePENDLE value decreases over time, but users can extend their lock duration to counteract this decay.
Penpie
Penpie is a next-generation DeFi platform specifically designed to enhance the yield and governance capabilities for users of Pendle Finance. It focuses on locking PENDLE tokens, allowing users to benefit from increased governance rights and enhanced yield opportunities within Pendle Finance’s ecosystem. By leveraging Pendle Finance's veTokenomics model, Penpie offers users new ways to maximize their returns and governance power.
Penpie introduces a mechanism where PENDLE token holders can convert their tokens into mPENDLE at a 1:1 ratio. This conversion enables users to earn maximized PENDLE rewards through the platform. Once PENDLE tokens are converted into mPENDLE, Penpie locks the original PENDLE as vePENDLE within Pendle Finance. This process allows Penpie to accumulate vePENDLE, which grants the platform access to enhanced PENDLE rewards and increased governance power within Pendle Finance.
Reentrancy Hack: Attack Analysis
On September 3, 2024 (6:23 PM UTC), the Penpie hack exploited a reentrancy hack path to steal over $27M on Arbitrum and Ethereum. By creating a fake Pendle market, the attacker manipulated reward accounting, inflated balances, and repeatedly harvested funds before state updates.
The stolen assets included wstETH, sUSDe, agETH, rswETH, and other Pendle-related YT tokens.
Vulnerability Exploitation
The incident was caused by two major factors:
- Lack of reentrancy protection in
PendleStaking::batchHarvestMarketRewards() - Penpie’s acceptance of all Pendle Markets as valid pools, despite Pendle Markets, PT, and YT tokens being permissionlessly created.
Attack Breakdown:
- Creation of a Fake Market: The attacker created a fake Pendle Market using a fraudulent SY token, which also served as the attack contract. The attacker created a pool, minted YT and PT tokens for the Pendle Market, and then deposited the market into Penpie.

- Flashloan Execution: The attacker took a flashloan from Balancer in agETH, rswETH, egETH, and wstETH, then deposited the funds into the fake SY contract.

- Reentrance: The attacker invoked
PendleStaking::batchHarvestMarketRewards()with the malicious market as the argument. During this call, the attacker was able to re-enter the function becausePendleMarket::redeemRewards()was called on the fake SY market.

- Manipulating Reward Calculations: Initially, the fake market returned the desired token types that would be stolen by the
PendleMarket::getRewardTokens()function, and these tokens were recorded in thebonusTokensarray.
Afterward, the token balances of thePendleStakingcontract were recorded in theamountsBeforearray. Next, thePendleMarket::redeemRewards()function was called on the fake market, which deposited the flash-loaned tokens into legitimate markets viaPendleStaking::depositMarket(). Although this function had anonReentrantmodifier, the modifier was bypassed because, as mentioned earlier, thebatchHarvestMarketRewards()function lacked such protection.
This resulted in an increase in thePendleStakingbalance, which made the contract incorrectly assume that the balance increase was due to redeemed rewards rather than deposited funds. This led to significantly larger rewards being reflected in theamountAfterarray.
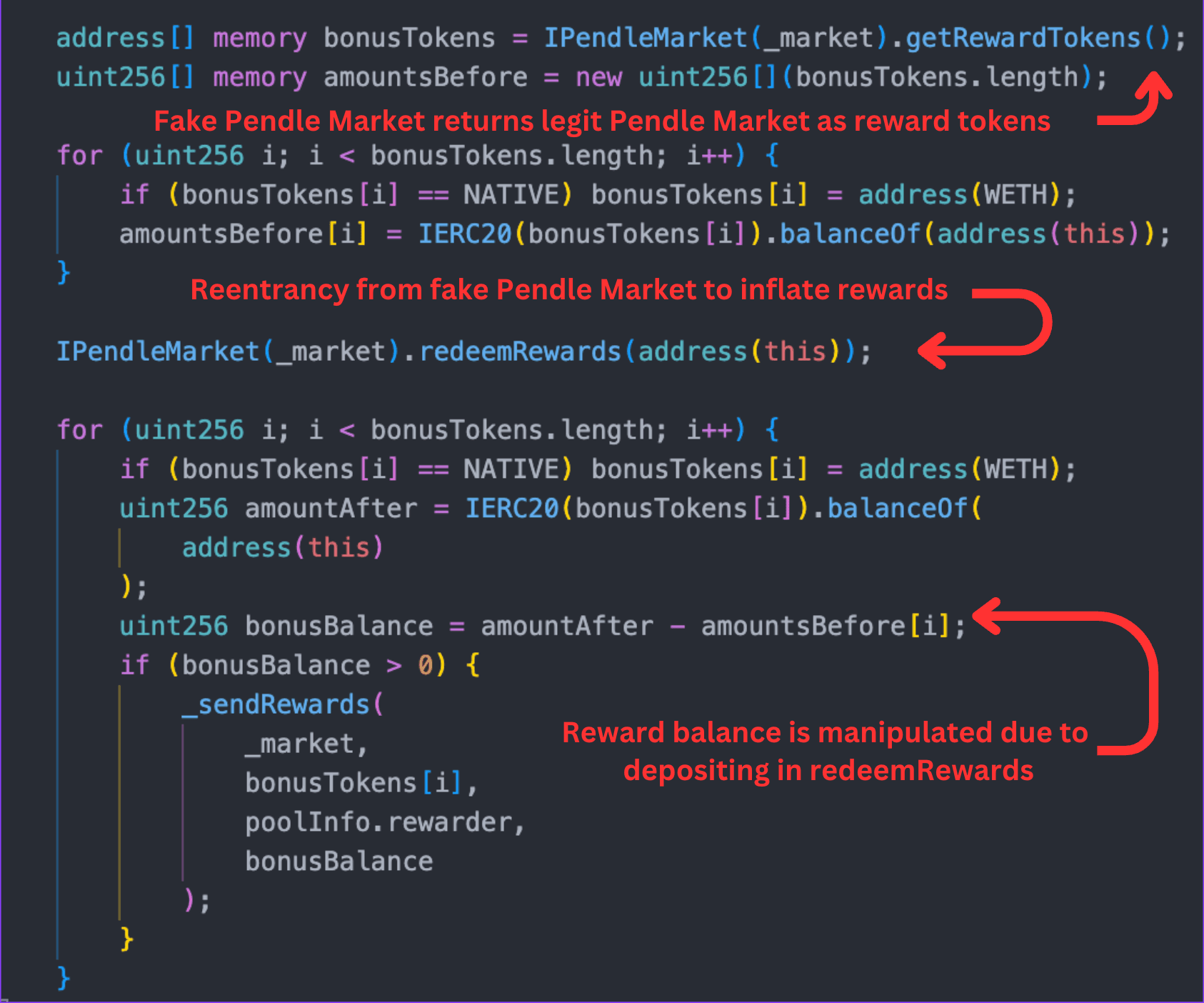

- Claiming Rewards:
PendleStakingthen sent the incorrect reward tokens (Pendle Markets) and amounts to theRewardDistributor, attributing those Pendle Markets to the fake Pendle Market depositor. Since the attacker was the sole depositor in the fake Pendle Market, they were able to claim all the rewards, including wstETH, sUSDe, egETH, and rswETH Pendle Market tokens. - Withdrawal and Conversion: The attacker then withdrew from the legitimate Pendle Markets they had deposited into and converted the Pendle Market tokens back into their original assets. Afterward, they repaid the flash loan and kept the remaining profit.

How the Attack Could Have Been Prevented
Although there was a reentrancy check in the PendleStaking::depositMarket() function, the batchHarvestMarketRewards() function lacked this protection, which allowed the Penpie hack to occur. Implementing a nonReentrant modifier on this function could have prevented the attack.
The Penpie protocol was paused on all chains. The Penpie team joined a War Room alongside Pendle Finance and the Security Alliance (SEAL 911). Pendle Finance posted on X to inform users that their platform was unaffected, although they acknowledged that Penpie had been targeted in the attack, leading to a security compromise. The Penpie team also filed a report with the Kampong Java Neighbourhood Police Centre.
The team also started working with Hypernative to track the hacker’s movements. One positive development is that Pendle’s logging system identified the attacker’s VPN IP address when they used Pendle’s frontend to perform a YT swap. The VPN IP address was reported to the Singapore Technology Crime Senior Investigation Officer, who will forward the cybercrime incident to the VPN provider for further information.
Also the team Initiated communication with Binance Security, Slowmist, and Chainalysis/zeroShadow to demix the Tornado Cash deposits.
Consequences
Approximately $27 million was stolen across multiple chains. Unfortunately, the attacker did not respond to any messages (TX) and began transferring the stolen funds to Tornado Cash in batches of 100 ETH from different accounts (TX), effectively laundering the money.
Pendle Finance briefly paused its contract, protecting roughly $70 million (excluding vePENDLE positions) that could have been further drained from Penpie. Moving forward, the team will continue to attempt negotiations with the attacker in hopes of reaching a whitehat settlement.

Reach out to Three Sigma, and let our team of seasoned professionals guide you confidently through the Web3 landscape. Our expertise in smart contract security, economic modeling, and blockchain engineering, we will help you secure your project's future.
Contact us today and turn your Web3 vision into reality!
The Penpie exploit shows that even known risks like reentrancy can sneak in through edge cases and vault logic. Our Smart Contract Audit service rigorously tests for state management bugs, nested call vulnerabilities, and protocol-specific logic flaws.
Conclusion
The Penpie hack shows how a single reentrancy hack in reward harvesting can cascade across permissionless markets. Lock down harvest functions with nonReentrant, restrict market acceptance, and complete a focused Pendle audit before shipping similar flows. Post-incident, apply demixing crypto procedures to separate tainted outputs and accelerate recovery paths.
Addresses
Deployment of Malicious Markets
- https://etherscan.io/tx/0xfda0dde38fa4c5b0e13c506782527a039d3a87f93f9208c104ee569a642172d2
- https://etherscan.io/tx/0x7e7f9548f301d3dd863eac94e6190cb742ab6aa9d7730549ff743bf84cbd21d1
- https://etherscan.io/tx/0x7961b0d3382bddff4c777e432902ea0b6940414ec16aa1a1dcebc4ebcbd8f867
- https://etherscan.io/tx/0xca87f257280e19378dc1890a478514195f068857affacde0b92c851b897dff9e
- https://arbiscan.io/tx/0x67c5400da117b906f8c0fc5f5149e4ea10ed6358cd9ea2ec0ed8f559d757b7df
Attacks
- https://etherscan.io/tx/0x56e09abb35ff12271fdb38ff8a23e4d4a7396844426a94c4d3af2e8b7a0a2813
- https://etherscan.io/tx/0x42b2ec27c732100dd9037c76da415e10329ea41598de453bb0c0c9ea7ce0d8e5
- https://etherscan.io/tx/0x663b55a1ee992603f7636ef23ff5cf19d3b261ab81494d06e218c86482df5342
Exploiter Wallets
- https://etherscan.io/tx/0x663b55a1ee992603f7636ef23ff5cf19d3b261ab81494d06e218c86482df5342
- https://etherscan.io/address/0x28e3fd9edca8fccb912fe3ab36c78f96cfc74769
- https://etherscan.io/address/0x69751b7e52dbbd64281ec9049dfa623c7ecdeb52
- https://etherscan.io/address/0x2f2dde668e5426463e05d795f5297db334f61c39
- https://etherscan.io/address/0xd440d2c13e9c0b86f54da4f515f68c56f0c36cc3
- https://etherscan.io/address/0x2dc15e0ff02f39d4d23a96d6ef2595df3d1e18a0
- https://etherscan.io/address/0x10f8c81386a2563f687011f4ebc8f2091cb501e8
- https://etherscan.io/address/0x8c37ad70ce51e54d2d75da40668e9530d337f26b
- https://etherscan.io/address/0x688413d6cae1c0e0882e274a98e0b901fdf7233c