Anatomy of a Wallet Drainer
Wallet drainers are one of the most damaging tools in the crypto scam arsenal. They combine social engineering, front-end deception, and automated scripts to siphon assets directly from victims’ wallets. The core idea is simple: convince users to authorize a transaction that, on the surface, appears safe, but in reality, grants the attacker full control. That’s why wallet security needs the same discipline as a web3 audit, assume the UI can lie, and validate the actual execution path.
Drainers often impersonate legitimate dApps using fake websites spread through hijacked accounts, Discord bots, and sponsored ads. Once the victim lands on the site, they are encouraged to mint NFTs, claim tokens, or verify wallets. These actions trigger malicious approve() calls that authorize the attacker to move assets via transferFrom(), which is why protocols need a smart contract audit to catch approval design flaws and dangerous call paths.
These attacks often present transaction prompts with misleading UI labels, inflated calldata payloads, and contract self-destruction to evade both static detection and transaction simulation. Moreover, some drainers specifically target the human layer, convincing users through urgency, fake support channels, and even clone sites seeded through sponsored search results.
Even experienced users have fallen victim, including founders and wallet developers. With over 330,000 wallets impacted in 2024 alone resulting in losses totaling around $494 million, wallet drainers remain a critical threat vector requiring both technical and behavioral countermeasures.
Simulation Assumptions and Drainer Evasion
A crucial problem with transaction simulation is that wallets simulate transactions based on the current state of the blockchain, which can change before execution. Smart contracts, DEX balances, or proxy logic can mutate between simulation and execution. Drainers exploit this time-of-check/time-of-use (TOCTOU) gap to deceive users. This is particularly dangerous in transactions involving delegate-call-based proxies, where logic can be dynamically rewired after simulation.
A contract may detect when it's running inside a simulation and behave safely ("Red Pill" behavior), but revert to malicious logic post-signature.
Programmable EOAs: The New Phishing Frontier
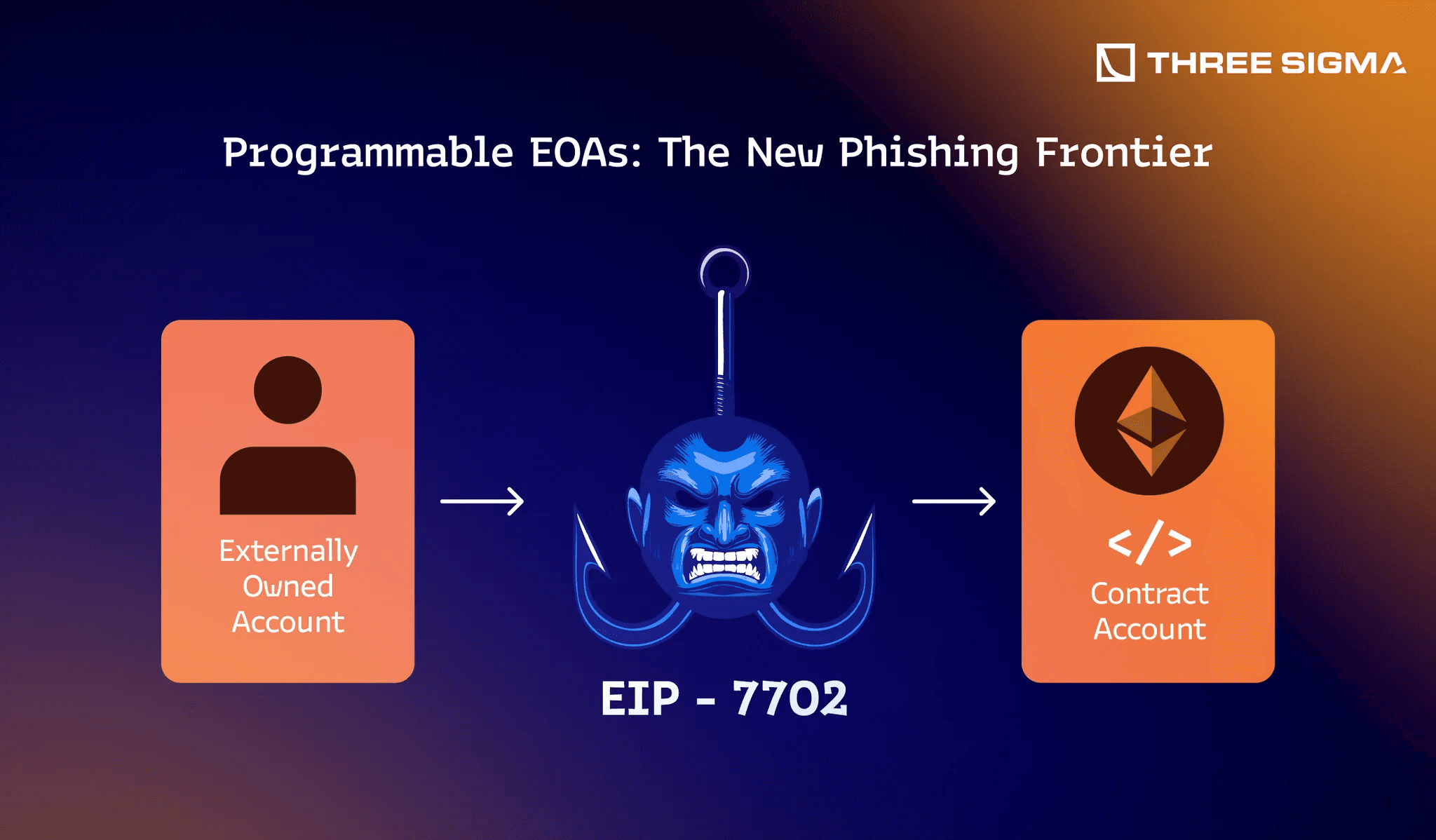
With the activation of EIP-7702, EOAs (Externally Owned Accounts) can now delegate execution rights to smart contracts, effectively blurring the boundary between EOAs and contract accounts. While this brings powerful features like atomic transactions and programmable wallets, it also creates a new class of phishing risk: delegation-based wallet drainers.
Instead of tricking users into signing a traditional approve() call, attackers now coax victims into delegating execution to malicious contracts, often by disguising this action as a “wallet upgrade,” “security enhancement,” or “AI assistant authorization”. These delegated contracts can implement logic to transfer tokens, exploit re-entrancy in vulnerable contracts, or batch malicious transactions, all without additional user input.
The attack surface is broader: an EOA with a delegation set behaves like a contract, and calling that address may trigger arbitrary logic. Users may unknowingly sign a delegation that routes all future calls through hostile logic, behavior that may not be accurately previewed by current simulation tools, especially if the delegated contract uses proxy patterns, conditional logic, or obfuscated code to disguise intent.
To complicate matters, phishing kits now bundle EIP-7702 delegation payloads into SET_CODE (0x04) transaction templates. With a few lines of JavaScript, attackers can generate and simulate delegation-signed payloads, auto-fill them in wallet UIs, and trick users into setting persistent execution rights, no approvals needed.
As wallets and dApps race to support programmable EOAs, phishing infrastructure is evolving in parallel, making EIP-7702 delegation phishing one of the most critical threats to monitor in the post-Pectra Ethereum ecosystem.
Deployment Automation
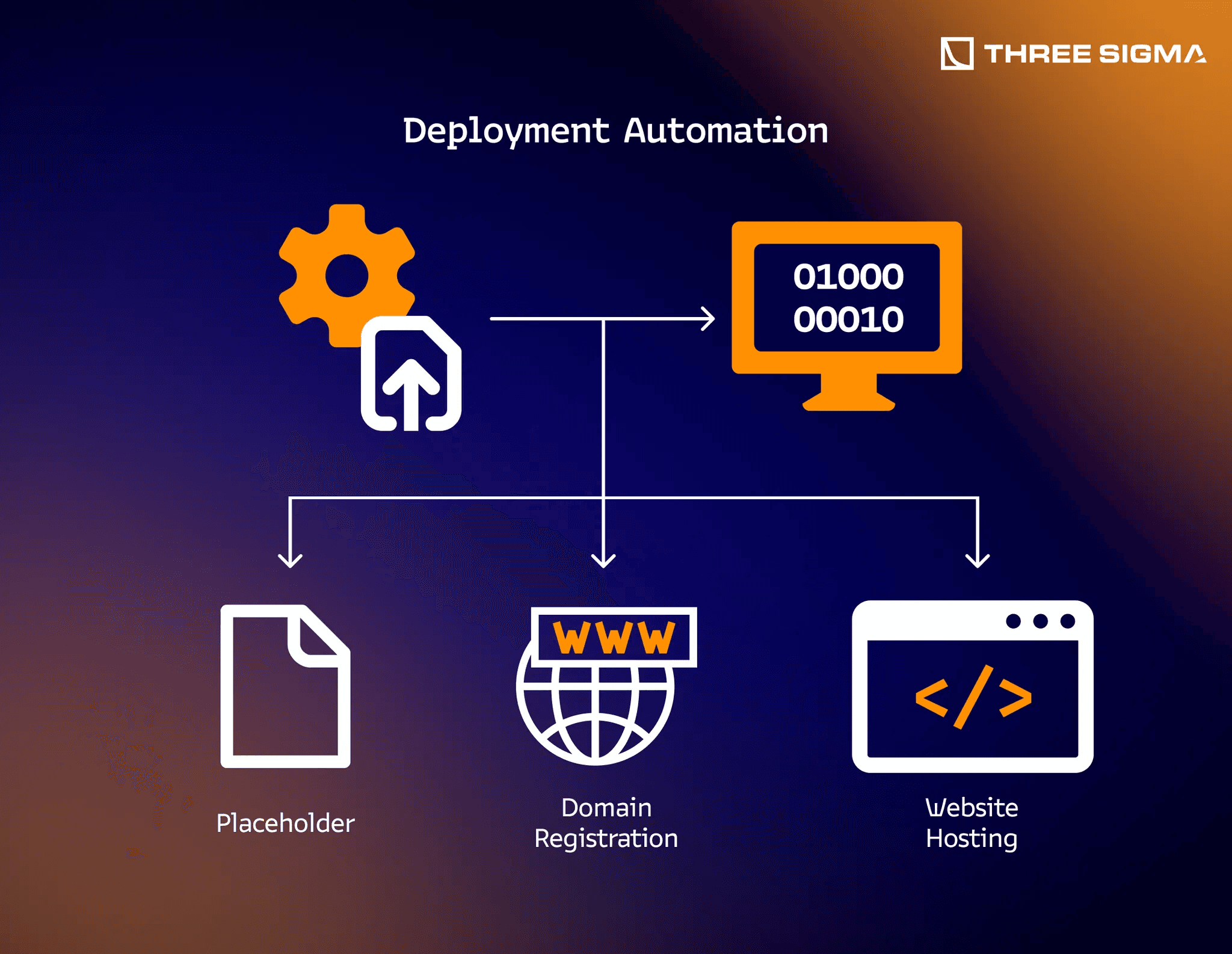
To scale their operations, crypto drainer groups automate significant portions of their phishing infrastructure. While the core draining logic resides in malicious scripts embedded within phishing websites, attackers focus on automating the creation and deployment of the surrounding infrastructure.
This infrastructure includes, registering numerous domain names, and hosting convincing front-ends on platforms like GitHub Pages, Webflow, or even compromised legitimate websites. Rather than innovating on-chain, scammers often recycle boilerplate contract code, altering it. These phishing pages mimic real dApps and wallet interfaces, tricking users into signing malicious approvals for legitimate tokens already in their wallets. Automation ensures each instance uses a fresh contract address and domain, complicating detection and blacklisting efforts.
Large Language Models (LLMs) are increasingly utilized not for generating contracts, but to vary front-end text, phishing instructions, or chatbot responses. By randomizing phrasing and branding, scammers reduce the effectiveness of pattern-matching tools. The result is a high-throughput fraud pipeline: thousands of lookalike decentralized applications (dApps) and sites, each pointing to a central draining script, deployed with minimal manual effort.
Defensive Patterns
Defending against wallet drainers and phishing kits involves multiple strategies due to inherent limitations of any single technique.
- Avoiding Raw Message Signing: The most crucial recommendation is avoiding signing raw
eth_signmessages entirely, as these cannot be clearly parsed or simulated reliably and remain highly exploitable. - Client-Side Simulation (with Limitations): Wallets like Rabby and MetaMask WalletGuard offer transaction simulation features, allowing users to preview transaction outcomes locally before approving. For example, Rabby simulates balance changes, highlighting potentially malicious token approvals or transfers. However, simulations can be circumvented by attackers through time-of-check/time-of-use exploits. Hence, users must not rely solely on these tools.
- Structured Signing (EIP-712): Adopting structured data signing via EIP-712 enables wallets to clearly show transaction intent, detailing specific tokens, amounts, and recipients. Unlike raw signatures, structured signing reduces user confusion by providing readable, verified intent screens. Widespread use of EIP-712 remains critical to safer transactions.
- Relay and Node-Level Defenses (Selective Chains): Some Ethereum-based MEV relay services, mining pools, or block builders voluntarily implement blacklists, refusing transactions interacting with known malicious contracts. Such defenses have emerged notably within Ethereum mainnet and certain L2 networks (Arbitrum, Optimism), yet remain less standardized and not universally applied across all blockchains.
In summary, no single precaution offers complete safety. Users should employ structured signing standards, transaction simulation cautiously, avoid raw signatures entirely, and remain skeptical of unsolicited or urgent transaction prompts.
Real-World Incident: “Inferno Drainer Reloaded” (Mar–May 2025)
In early 2025 investigators tracked a resurgent Drainer-as-a-Service operation nick-named Inferno Drainer Reloaded. Although its operators publicly “shut down” in late 2023, blockchain telemetry shows the core infrastructure never disappeared, instead it evolved, re-emerging with major upgrades that helped siphon >$9 million from 30 000 + wallets in just six months.
Attack funnel
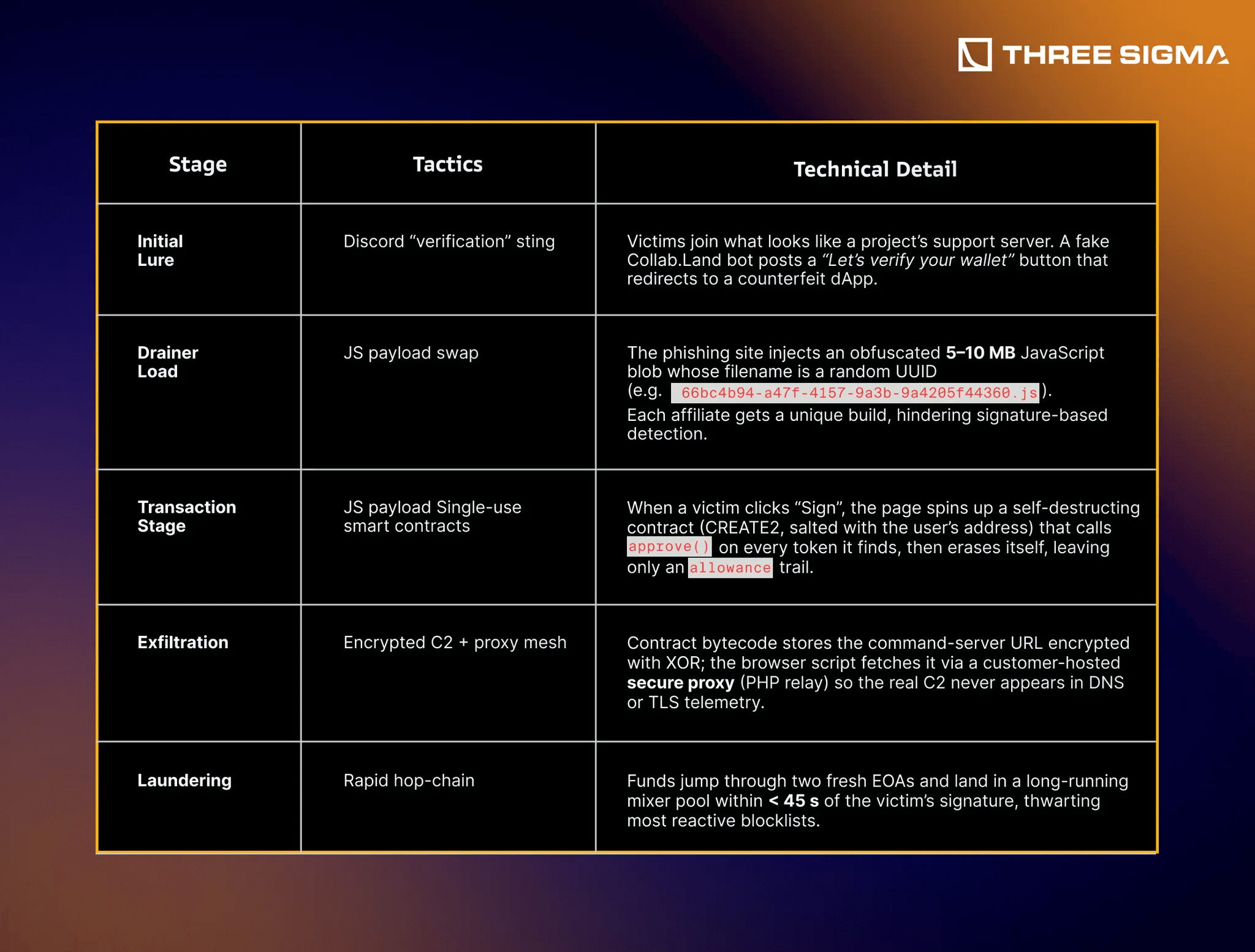
Why Inferno Drainer matters
- Technique escalation adds on-chain encrypted C2 and self-destruct contracts, defeating static IOC blacklists.
- Affiliate economy charges a flat 30 % cut of every theft; newcomers need only paste one line of script into a cloned webpage to start stealing.
- Cross-chain reach default templates handle Ethereum, BSC, Polygon and Base; auto-detect chain IDs and craft chain-specific RPC calls.
Conclusion
Drainers are evolving from basic phishing pages into sophisticated multi-chain, simulation-aware systems with programmable delegation and Red Pill detection. As EIP-7702 reshapes how EOAs operate, phishing kits adapt in parallel. Future defenses must combine structured signing, simulation integrity, constraint-based transaction modeling, and careful user behavior. Only by hardening both the technical and human layers can we reduce the impact of these increasingly scalable attacks.
Frequently Asked Questions (FAQ)
What is a crypto wallet drainer?
A wallet drainer is a malicious script or phishing toolkit designed to steal assets directly from a user's crypto wallet. It tricks users into signing deceptive transactions that grant attackers access to their funds, typically through fake websites that impersonate real dApps or wallet services.
How do wallet drainers trick users into giving access?
Users are often lured to phishing sites via fake Discord bots, compromised Twitter accounts, or sponsored ads. These sites mimic legitimate interfaces and prompt users to sign transactions that grant unlimited approvals or delegate execution rights to attacker-controlled contracts.
What is the role of EIP-7702 in modern phishing attacks?
EIP-7702 introduces programmable EOAs that can delegate execution to contracts. Phishers exploit this by disguising malicious delegations as wallet upgrades or security features, allowing them to execute arbitrary logic once users sign a delegation transaction.
Can transaction simulation tools detect drainer activity?
Simulation tools like Rabby or MetaMask WalletGuard help preview transaction effects, but they can be bypassed. Drainers may exploit time-of-check/time-of-use (TOCTOU) gaps or use obfuscated logic that behaves differently after signature, reducing the effectiveness of simulations.
How are drainers deployed at scale?
Drainer operators automate infrastructure using scripting tools to spin up thousands of phishing domains and clone front-ends. LLMs are sometimes used to vary the text and branding, avoiding detection. These phishing sites all point to a shared backend with the draining script.
What makes Inferno Drainer so dangerous?
Inferno Drainer is one of the most feature-rich phishing-as-a-service kits. It supports cross-chain targeting, auto-generated phishing sites, obfuscated JavaScript payloads, and built-in laundering paths. Affiliates only need to embed one line of code to start stealing funds.
What is the difference between an approve() scam and a delegation-based scam?
An approve() scam tricks users into giving a contract unlimited access to transfer a specific token. A delegation-based scam (via EIP-7002 or EIP-7702) grants broader execution rights, allowing attackers to run arbitrary code from a delegated contract without additional prompts.
How can I protect my wallet from drainers?
Use wallets that support EIP-712 structured signing, avoid signing raw eth_sign messages, double-check URLs, avoid clicking on sponsored search ads, and keep large balances in cold storage. Never approve transactions or delegations from unsolicited prompts.
Why do phishing sites often look so convincing?
Attackers clone real dApp interfaces and use similar domain names (like “uniswap-airdrop[.]xyz”). With LLMs and automation, they can generate customized, localized, and constantly rotating phishing pages that closely mimic legitimate platforms.
Is there a way to recover funds after being drained?
Unfortunately, once a transaction is signed and executed on-chain, it is irreversible. Some platforms may help track funds or identify the drainer's address, but asset recovery is extremely rare. Prevention remains the best defense.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.

Code Security Lead
Niccolò is a security researcher with an adversarial mindset and strong interest in operational security. He holds a Master’s degree in Software Engineering and after years in the field he has audited numerous production-grade DeFi systems. He is also a co-author of Mastering Ethereum (2nd Edition), contributing to industry education and research efforts.