Introduction: Why Web3 Security is a Lucrative Path in the Crypto World
Entering the Web3 security auditing field might seem challenging without coding skills, but there are opportunities even if you know nothing about coding with economic audits. In this article, we explore how non-technical contributors can get paid as Web3 auditors, whether through code audits or leveraging basic knowledge and transferable skills to thrive in the blockchain ecosystem. For an overview of where these services fit, explore our full range of Web3 audits.
Imagine earning $10,000 for finding a single bug. Imagine $100,000 payouts for critical vulnerabilities. Imagine top firms paying $200,000+ annually for security experts who know how to keep DeFi protocols safe from hackers amid common DeFi vulnerabilities.
It might sound ambitious, but it's the reality of Web3 Security. People are building rewarding careers by identifying smart contract vulnerabilities and helping projects prevent costly exploits.
The best part about becoming a Web3 Auditor:
- You don’t need a degree.
- You don’t need a tech background.
- You don’t even need coding experience to start.
All you need is the right roadmap and the right resources (like understanding what a smart contract audit involves) to start making serious money in this fast-growing field. And this guide will give you exactly that.
🚨 Warning: If you’re not serious about learning and putting in the work, this isn’t for you. But if you follow this guide, you could be on your way to earning $100,000+ in your first year as a Web3 security auditor.
Why Does Web3 Security Pay So Well?
Every week, we see headlines about multi-million-dollar exploits in DeFi. Because smart contracts run on open, transparent code, a single bug can lead to catastrophic losses. That’s precisely why security auditors are paid so handsomely. The stakes are huge, and the value locked in decentralized protocols is only going up. If you can find vulnerabilities before attackers do, your expertise is worth its weight in gold—especially to projects that could lose millions in a single hack. For more details, explore Three Sigma’s website.
A career in Web3 Security isn’t just about reviewing code. It’s also about understanding the economics behind DeFi, thinking creatively like a hacker, and collaborating with teams to make their protocols airtight. In an industry moving this quickly, a vigilant, forward-thinking security pro can command very high pay. And unlike some fields, there’s no rigid credential requirement. Prove you can find issues, and you’ll be taken seriously.
Essential Skills and Mindset (Even If You Can’t Code…Yet)
Plenty of newcomers assume they must be expert developers to even begin their journey toward becoming a Web3 security auditor. But security is as much mindset as it is coding. You’ll see professional auditors who started with no technical background whatsoever. They excelled because they learned the right skills and embraced the right mindset.
Skills You’ll Need to Develop

- Get Acquainted with Blockchain
Start by understanding how blockchains (especially Ethereum) work under the hood. Why does decentralization matter? How do transactions flow? What role do miners and validators play? Even without diving into the deep end of cryptography, having a solid blockchain grasp helps you see why certain vulnerabilities are critical. These books provide an excellent foundation on blockchain technology, networking, and the specific architecture of Bitcoin and Ethereum.
Recommended Reading:
Mastering Bitcoin by Andreas Antonopoulos.
Mastering Ethereum: Mastering Ethereum (1st Edition) by Andreas Antonopoulos and Gavin Wood.
Mastering Ethereum (2nd Edition) (Upcoming) – Our Lead Auditor, Niccolò Pozzolini, is contributing to the writing of this edition. - Ability to Think Like an Attacker
Security auditing is basically ethical hacking. A significant part of the job is learning to break things intentionally—without the consequences of actually harming protocols. Ask yourself, “How can someone exploit this function? Where might the code fail?” This mindset shift is crucial. - Advanced Blockchain & Smart Contract Knowledge
You don’t need to be a PhD-level coder, but you do need to understand how smart contracts (often written in Solidity) work, as well as the common pitfalls (e.g., reentrancy, price oracle manipulation, and incorrect access control). - High-Level Financial Literacy
Since you’ll often review DeFi protocols (which are basically financial applications built on blockchain), it helps to grasp core finance concepts—like liquidity, collateralization, or how lending pools operate. Even just an overview of these topics will help you pinpoint potential attack vectors. - Communication & Reporting
It’s not enough just to find a vulnerability; you also need to explain it clearly. Whether you’re writing reports for a bug bounty program or presenting findings to a project team, the ability to communicate risks and solutions makes you invaluable.
Mindset: Curiosity, Ethics, and Teamwork
- Curiosity & Adaptability
If there’s one secret ingredient, it’s staying curious and adapting to a fast-moving landscape. New protocols and exploit methods appear constantly. Auditors must keep an eye on the latest research, emerging hack reports, and best practices to ensure they remain relevant. The best auditors also push beyond surface-level details—diving into contract logic, protocol documentation, and user behaviors, always asking “Why?” or “What if?” - Ethical Responsibility
Security researchers often see behind the curtain of a protocol’s most sensitive code. Reporting flaws responsibly, respecting boundaries, and adhering to the law is what separates an ethical auditor from a malicious actor. This professionalism is the backbone of trust in the community. - Open Collaboration
Web3 moves fast. No one can keep up all alone. Whether you join a security firm or dive into online communities, a willingness to share ideas and learn from peers can rocket-fuel your progress. Engaging in Discord discussions, group audits, or hackathons helps refine your skills and perspective.
You Don’t Need to Be Part of a Large Organization
While many auditors thrive at established security firms (where you might get structured mentorship and steady income), it’s equally valid to carve out a successful career independently. There are bug bounties, community-led audit contests, and freelance opportunities such as blockchain audits that don’t tie you to any single company. In short, there’s no “one-size-fits-all” path to success here. Your skill set and mindset matter far more than a specific job title.
The Roadmap to Becoming a Web3 Security Auditor
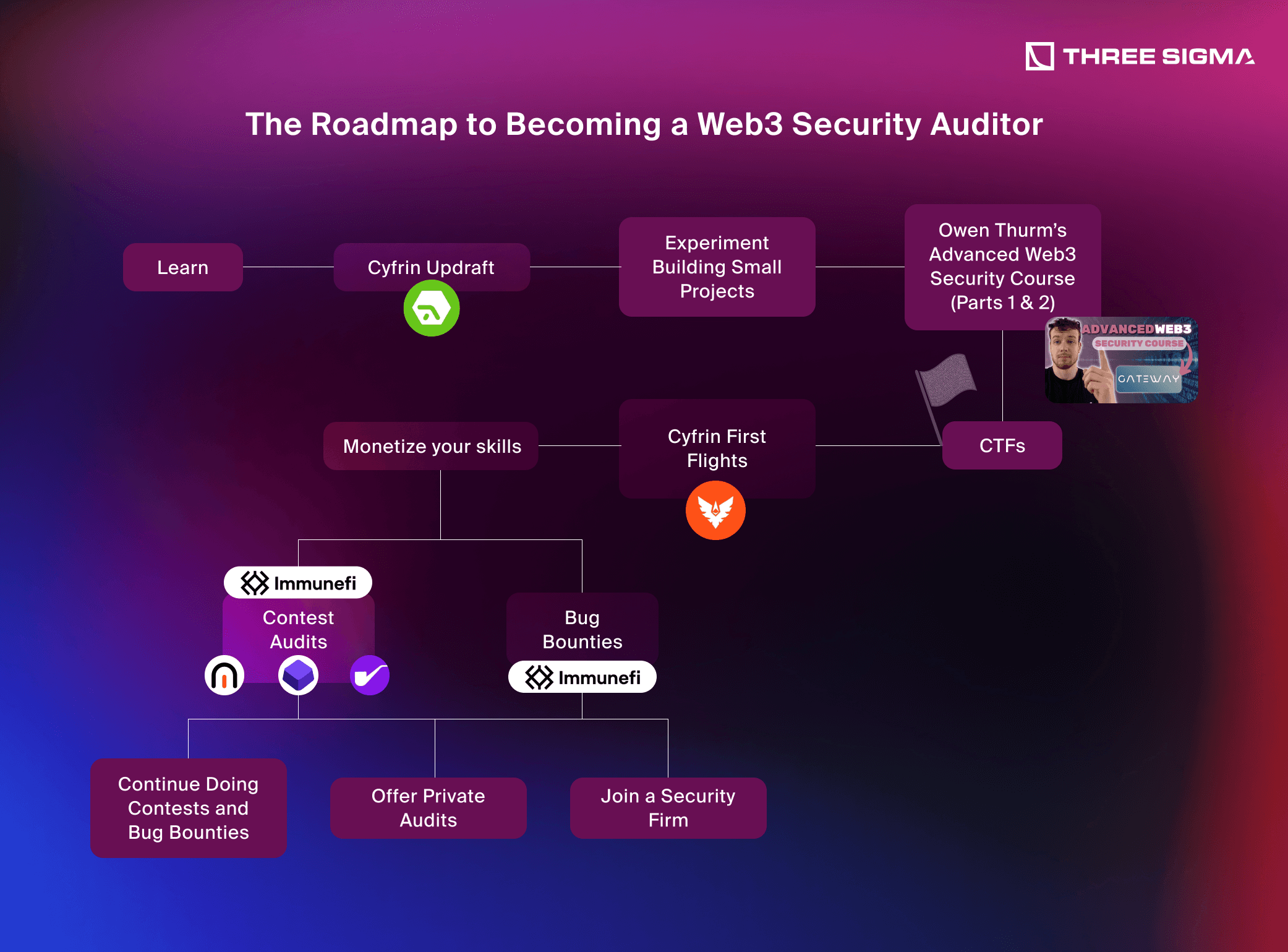
Ready to dive into Web3 Security and start earning money? The journey can seem overwhelming at first, especially if you’re starting with zero experience. That’s why a step-by-step roadmap is essential. This Web3 bug bounty roadmap gives beginners a step-by-step path from basics to bounties and audits. Below, you’ll find the recommended progression for complete beginners to move from basic learning to earning as a professional auditor.
While Web3 security applies to multiple blockchains and smart contract languages, this guide primarily focuses on Solidity and EVM-based contracts. Solidity is the most in-demand language for security auditors, making it the best starting point for both career opportunities and learning efficiency. Even for those who eventually want to audit Rust-based contracts on Solana, or teams building on Sui or Aptos who’ll ultimately need a Move audit, starting with Solidity can be a more practical approach. Its simpler syntax, widespread documentation, and larger ecosystem of learning resources make it easier to grasp security fundamentals before transitioning to more complex environments.
Note: All the specific links and references mentioned here can be found on the upcoming GitHub repository, so you don’t have to bookmark everything right now.
Step 1: Begin with Cyfrin Updraft

Cyfrin Updraft is a free introductory course designed specifically for those who are new to blockchain and smart contracts. Even if you’ve never written a line of code, this course breaks down complex ideas into simple, digestible lessons, covering:
- Blockchain Fundamentals Gain a solid grasp of how Ethereum functions, how blocks are created, and why decentralization matters for security.
- Solidity Basics Learn the syntax and structure of the programming language used for most Ethereum smart contracts—no previous coding experience required.
- Common Vulnerabilities Dive into foundational security pitfalls like reentrancy attacks, oracle manipulation, and access control issues.
- Security Mindset Understand how to think like an auditor, spotting potential exploits before they become real threats.
By the time you complete Cyfrin Updraft, you’ll have a clear understanding of how smart contracts function and an eye for where the most common pitfalls lie. This is where a solidity or rust smart contract audit comes in.
Step 2: Get Your Hands Dirty with Solidity, Tooling & Ethical Web3 Hacking

Now that you’ve seen the basics, it’s time to experiment. Building small projects and testing them locally helps cement your knowledge:
- Practice Writing Simple Contracts
A basic ERC20 token or “Hello World” contract can teach you about functions, state variables, and events. - Use the Right Tools Frameworks like Foundry make it easier to compile, test, and debug.
- Explore Our Blog We regularly post about smart contract security, current threats, and advanced techniques. Keep an eye on our latest articles to stay up to date.
- Study Real DeFi Projects Review code from robust protocols like Maple. Observing their security patterns can spark ideas for your own audits.
Step 3: Owen Thurm’s Advanced Web3 Security Course (Parts 1 & 2)

This two-part series is designed to take learners from solid fundamentals to expert-level auditing skills. It focuses on both practical demonstrations—like live code walkthroughs—and theoretical foundations that explain why and how advanced exploits succeed (or fail).
What You’ll Learn in Owen Thurm’s Courses
- Under-the-Hood Contract Design
Explore best practices for safe architecture, delve into external call safety, and tackle reentrancy in all its forms. This foundation helps you identify where contracts are most vulnerable and how attackers exploit fundamental design flaws. - Testing Strategies & Advanced DeFi
Discover how to systematically test contracts using various methods (including fuzzing), and deepen your grasp of perpetuals and other high-level DeFi mechanisms. Emphasis is placed on pinpointing subtle exploits that often lurk in complex financial logic. - On-Chain Manipulation & Reporting
Unpack frontrunning and sandwich attacks, learning how transaction ordering can tilt the playing field. You’ll also see how to write clear, compelling vulnerability reports, ensuring your findings carry weight in bug bounty programs or professional audits. - Code Deep Dives & EVM Mastery
Watch live audit sessions that walk through code line by line, and explore EVM internals—covering memory layouts, Yul optimizations, and calldata handling. These sessions reveal how nuanced mistakes in low-level operations can escalate into significant security risks.
Where an introductory course covers the “what” of security basics, Owen Thurm’s Advanced Web3 Security digs into why sophisticated attacks work—pushing you to think like a determined adversary and sharpen your investigative mindset for high-stakes auditing.
Step 4: Start Doing CTFs

Capture The Flag (CTF) challenges are a fun, hands-on way to test exploit techniques. They can help you sharpen your auditing instincts even further:
Recommended CTFs
- Ethernaut: Puzzle-like, focuses on various smart contract vulnerabilities.
- Damn Vulnerable DeFi: Emphasizes common DeFi exploits.
CTFs offer a self-paced environment to tackle new vulnerabilities and think creatively like an attacker.
Pro Tip: It’s easy to get caught in an endless cycle of CTF practice. One or two challenges are great to build confidence and creativity, but don’t let CTFs become a distraction from real auditing experience. Your ultimate goal is to audit live protocols and uncover tangible vulnerabilities.
Step 5: Level Up with Cyfrin First Flights

This smart contract audit contest platform replicates real DeFi environments. It’s a safe space to hone your skills, gain practical auditing experience, and receive valuable feedback on your findings.
What You’ll Do in First Flights
- Join Mock Audits Participate in contests built around codebases that mirror actual DeFi protocols.
- Identify Vulnerabilities Pinpoint issues ranging from straightforward reentrancy bugs to more complex economic exploits.
- Submit Findings & Receive Feedback Write professional-style vulnerability reports, then see what you missed through feedback from organizers and peers.
- Level Up Your Skills Sharpen your ability to read code, think critically about security, and communicate your findings effectively.
Contests on First Flights are less daunting than full-blown client audits, yet they prepare you for the rigors of professional security work—ensuring you’re ready to tackle real-world vulnerabilities with confidence.
Step 6: Monetize Your Skills as a Web3 Auditor

Now that you’ve absorbed the fundamentals, practiced with real code, and honed your security mindset, it’s time to monetize what you’ve learned. After exploring everything from Cyfrin Updraft to advanced auditing courses and CTFs, you have a solid foundation in Web3 Security. You’re ready to find vulnerabilities, report them responsibly, and get paid for your expertise.
In the next section, we’ll dive into three common paths that many successful auditors follow. Whether you prefer competitive auditing contests, bug bounty platforms like Immunefi, or taking on private audits for clients (or even joining a company full-time), these routes can help you turn your skills into income.
Unlocking Your Earning Potential in Web3 Security

1. Participate in Contest Audits
What Are Contest Audits?
These are time-bound, competitive code reviews where auditors race against the clock—and each other—to discover and report vulnerabilities. Each valid finding earns a reward proportional to its severity and impact. Additionally, if you find a bug that fewer auditors report (or you’re the only one to spot it), you typically earn more for that discovery. This creates a strong incentive to dive deeper into the codebase and uncover even the most hidden issues.
Popular Platforms
Each platform sets specific rules, timelines, and prize pools. Contest audits are an excellent way to build your reputation while getting hands-on, real-world security experience.
2. Bug Bounties on Immunefi

What Are Bug Bounties?
Bug bounties give security researchers the opportunity to find and responsibly disclose vulnerabilities in live deployed protocols holding millions of dollars in locked funds. Because the stakes are so high, payouts for critical bugs can reach six or seven figures—though uncovering such issues may take months depending on your skill level.
Immunefi is the most popular platform for these bounties, known for hosting some of the biggest payouts in the ecosystem. By submitting well-documented vulnerability reports and following each project’s guidelines, you can earn significant rewards while helping secure the Web3 space.
Note: While bug bounties can be lucrative, payout disputes occasionally arise. Some projects may downplay severity or reject valid reports, so it's wise to research bounty history before committing time. Audit contests, by contrast, always guarantee payouts since clients fund them upfront.
3. Transition to Private Audits or a Full-Time Role

Once you’ve built a solid portfolio whether from successful contest audits, Immunefi bounties, or a verified track record of private audits, you’ll find that opportunities come naturally. In Web3, your portfolio of proven wins is your calling card. Following a clear web3 bug bounty roadmap and potential Web3 security certification is what turns curious beginners into trusted professionals. And it all starts with your first step.
You have several options to level up your career:
- Continue Doing Contests and Bug Bounties
- Double down on what’s worked for you so far. As your skills grow, you’ll tackle bigger codebases and potentially find more critical vulnerabilities, leading to higher payouts.
- Offer Private Audits
- Work directly with clients to secure their codebases. This route often offers more consistent engagements, higher pay per project, and the chance to build long-term relationships with protocol teams. You’ll need to manage contract negotiations, timelines, and deliverables, but it can be highly rewarding.
- Join a Security Firm or Web3 Company
- If you prefer steady income, mentorship, and a supportive environment, many firms are actively hiring security experts. For instance, we at ThreeSigma provide audits to various protocols, and you can check out the story of our Head of Security’s path for real-world inspiration on growing your career in an established Web3 security firm.
Whichever path you choose—freelance or full-time—your portfolio of proven wins is your calling card. Keep learning, adapting, and you’ll discover endless opportunities to turn your Web3 security expertise into a thriving career.
Conclusion

Breaking into Web3 security might initially feel daunting—especially if you’re starting from scratch or don’t have a technical background. But as we’ve explored, there are multiple ways to learn the essentials, develop a hacker’s mindset, and translate those skills into paid opportunities. From competitive audit contests to bug bounty programs and private consulting gigs, the Web3 security field is packed with options for ambitious learners.
The key is to keep building your portfolio—every vulnerability you find and responsibly disclose adds weight to your credibility. Over time, you can command higher pay, unlock top-tier engagements, or land a stable role at a respected security firm. Whichever path you choose, staying curious, ethical, and adaptable will help you thrive in this rapidly expanding domain.
As the DeFi ecosystem grows and more complex protocols emerge, demand for skilled auditors will only rise. Whether you’re a self-taught hacker or pivoting from another field, Web3 security can be your gateway to a lucrative, future-proof career—all while helping protect the very foundation of decentralized finance.
Frequently Asked Questions (FAQ)
1. I have zero coding experience. Can I still become a Web3 security auditor?
Answer: Absolutely. While coding knowledge helps down the line, many of the core skills—like a hacker’s mindset, curiosity, and an understanding of blockchain basics—don’t require heavy programming at the start. You can learn Solidity and security concepts in parallel through beginner-friendly courses, hands-on practice, and capture-the-flag (CTF) challenges.
2. How long does it take to become proficient enough to find real vulnerabilities?
Answer: The timeline varies by individual. Some people pick up enough fundamentals in a few months, while others take closer to a year. The key is consistency—practicing with small smart contracts, participating in mock audits (like Cyfrin First Flights), and joining contest audits or bug bounty hunts to gain real-world experience.
3. Do I need a formal degree or certification?
Answer: No. Web3 security is a results-driven field—if you can demonstrate the ability to find and communicate vulnerabilities effectively, most projects and security firms will take you seriously. While certifications (e.g., in information security) can help showcase your dedication, they’re not a strict requirement.
4. Where can I find communities or mentors to help me learn?
Answer: Discord channels, Twitter, and specialized Reddit groups are gold mines for networking. Platforms like Code4rena, Immunefi, and Sherlock often have active communities where you can ask questions, share resources, and discuss audits with experienced peers. You can also follow well-known security researchers on Twitter and engage with them online.
5. What if I find a vulnerability but the project ignores me?
Answer: Always follow a responsible disclosure policy—document your findings, share them privately with the team, and allow them time to respond. If a project completely ignores you, check whether they have a publicly listed bug bounty or official guidelines. In some cases, going through a platform like Immunefi ensures that both parties follow established protocols. If all else fails and the vulnerability is severe, you may consider alerting the broader community ethically, but proceed with caution and legal advice if necessary.
6. How do I decide between bug bounties, contest audits, and private audits for clients?
Answer: Each path has pros and cons:
- Bug Bounties: More flexible, potentially large payouts, but finding severe bugs can be unpredictable.
- Contest Audits: Short, competitive reviews with clear timelines and guaranteed prize pools for valid findings.
- Private Audits: Stable projects, often higher flat fees, and deeper relationships, but requires building your reputation and trust first.
Many auditors combine all three approaches at different stages in their career.
7. I’ve heard of huge payouts—are they really that common?
Answer: High six-figure or even seven-figure rewards are possible, but they’re relatively rare and usually tied to critical, high-impact vulnerabilities in large protocols. Most researchers earn more modest but still substantial rewards for medium- or high-severity bugs on a consistent basis.
8. How do I keep my skills updated in such a fast-moving field?
Answer: Continuous learning is crucial:
- Follow Web3 security thought leaders on social media.
- Read audit reports from top security firms.
- Participate in capture-the-flag events or hackathons.
- Recreate real-world exploits using DeFiHackLabs – a hands-on repo where you can test vulnerabilities found in past hacks.
- Review post-mortems of real exploits to see how they happened.
Regularly practicing and staying curious about new attack vectors will keep you on the cutting edge.
9. What’s the best way to show off my skills to potential clients or employers?
Answer: Create a portfolio or security CV that lists:
- Publicly disclosed vulnerabilities you’ve found.
- Audit contest results or bug bounty acknowledgments.
- Links to any write-ups, public reports, or educational content you’ve produced.
Evidence of actual findings carries weight in hiring decisions, often more so than formal qualifications.
10. How much can I earn as a Web3 security or smart contract auditor?
Answer: Earnings as a Web3 security or smart contract auditor can vary widely based on experience, skill level, and the types of engagements you undertake. For instance:
- Bug Bounties: You might earn anywhere from a few hundred to several thousand dollars per vulnerability, with critical bugs potentially yielding six-figure rewards.
- Contest Audits: Depending on the platform and the contest, payouts can range from a few thousand to tens of thousands of dollars per audit.
- Private Audits and Consulting: Experienced auditors can charge anywhere from $50,000 to $200,000+ annually, depending on their reputation and the complexity of projects they handle.
Top firms may offer salaries exceeding $200,000 per year, and freelance auditors with a strong portfolio can command high rates per project. Overall, the potential for high earnings is significant, especially as the demand for Web3 security continues to grow.
11. Is a career as a Web3 Security Auditor a good idea?
Answer: Yes, pursuing a career as a Web3 Security Auditor is a promising and lucrative path for several reasons:
- High Demand: With the rapid expansion of the DeFi and blockchain sectors, the need for security auditors is growing, ensuring ample job opportunities.
- Competitive Compensation: As outlined, earnings can be substantial, with top auditors earning six or seven figures.
- Impactful Work: Auditors play a crucial role in safeguarding financial assets and ensuring the integrity of decentralized systems.
- Continuous Learning: The fast-paced nature of Web3 provides constant opportunities to learn and develop new skills.
- Flexibility: You can work with top security firms, as a freelancer, or even establish your own consultancy.
However, it's important to note that success in this field requires dedication, continuous education, and a strong ethical foundation. If you're committed to staying updated with the latest security trends and enjoy problem-solving, a career in Web3 security auditing can be both rewarding and future-proof.
12. Will AI take over security auditing?
AI is increasingly being integrated into security auditing, particularly in automated code analysis, vulnerability detection, and pattern recognition. While these advancements help streamline certain tasks, human expertise remains essential due to AI’s limitations in contextual reasoning, economic security evaluations, and assessing complex attack surfaces that require deep technical and strategic insight.
The Role of AI Agents in Security
AI-driven tools designed for security analysis are still in their early stages. CertaiK Agent, for instance, is a smart contract auditing agent that assists in identifying issues through automated checks. Agent4rena by Nethermind is another AI-powered initiative, with its MVP expected in the near future. While these systems show promise, they remain far from replacing human auditors and are still in active development.
Despite their potential, AI auditing agents struggle with accuracy and often generate a massive number of false positives—sometimes exceeding 90%. As one security researcher recently noted, even the most advanced AI agents tend to fabricate vulnerabilities or flag theoretical issues that lack real-world exploitability. A recent observation from @muellerberndt highlighted this problem, describing how AI-driven security tools consistently make things up rather than identifying actual vulnerabilities. This overwhelming volume of false positives forces human auditors to spend significant time filtering through incorrect reports, often negating the efficiency gains of automation.
https://x.com/muellerberndt/status/1878276452220821525
AI as an Assistant, Not a Replacement
Security auditing extends beyond finding technical issues—it requires understanding protocol mechanisms, financial dynamics, and ecosystem-wide risks, all of which demand human intuition and expertise. A vulnerability that seems minor in isolation might have critical implications in live deployment, and assessing such risks goes beyond AI’s current capabilities.
For now, AI is best seen as an assistant rather than a replacement, helping with automated checks, generating test cases, and scaling early-stage assessments. While AI can speed up parts of the process, human oversight is still required to filter noise, validate findings, and contextualize security risks.
Although AI will continue evolving, securing high-value Web3 applications still requires deep manual reviews from experienced professionals who can analyze risks beyond the reach of automation. AI can enhance security efforts, but for the foreseeable future, human expertise remains indispensable.

Security Researcher
Simeon is a blockchain security researcher with experience auditing smart contracts and evaluating complex protocol designs. He applies systematic research, precise vulnerability analysis, and deep domain knowledge to ensure robust and reliable codebases. His expertise in EVM ecosystems enhances the team’s technical capabilities.