Introduction to Abracadabra.money
Abracadabra.money stands out as a lending platform, enabling users to borrow stablecoins in the form of MIM (Magic Internet Money) by collateralizing their digital assets. It's powered by Sushiswap’s KASHI and BentoBox technology but differentiates itself with its approach to collateral. Users can collateralize interest-bearing tokens (ibTKNs), essentially LP tokens, to mint MIM across various chains. These ibTKNs have the feature of gradually accumulating value, providing continuous returns and becoming more valuable the longer they are held.
The platform isn’t limited to just lending, it also offers the opportunity to open leveraged positions through its Cauldrons Technology. When MIM tokens are repaid, they are systematically removed from circulation, helping to manage the market supply effectively.
In the ecosystem of Abracadabra.money, the SPELL token plays a dual role. It's not only used for governance but also acts as an incentive for active market participation. By staking SPELL tokens, users can receive sSPELL and earn a portion of the fees relative to their stake in the pool. Furthermore, the platform extends its staking options to include tokens like mSPELL, magicGLP, magicAPE and magicLVL For more information on the protocol's features, please refer to the official documentation.
Lending and Borrowing and How does Abracadabra Money work
In this section, you can find a brief introduction to lending and borrowing and how they work in Abracadabra Money. If you're already familiar with the topic, you can skip this part.
To better understand how Abracadabra Money works, you must first understand how traditional DeFi lending protocols operate.
In short, in traditional DeFi, smart contracts facilitate various lending and borrowing platforms, where participants:
- can lend tokens to earn interest.
- borrow tokens for different purposes, incurring interest.
DeFi Looping in Abracadabra (ibTKN → MIM → more ibTKN)
Looping is a common strategy in Abracadabra: users deposit interest-bearing tokens (ibTKNs), borrow MIM, swap MIM back into more collateral, and repeat to amplify exposure. High APY assets can look attractive, but looping tightens your liquidation buffer and amplifies risk.
How the loop works:
- Deposit collateral (e.g., ibTKN) → receive a borrow limit.
- Borrow MIM against the collateral.
- Swap MIM for more ibTKN and re-deposit.
- Repeat until you hit an internal risk limit (your own) or the protocol’s LTV cap.
Tiny numeric example:
- Start: 1,000 collateral units at $1 each (value $1,000). Max LTV 70% ⇒ borrow up to $700 MIM.
- Swap $700 MIM back into collateral → deposit → new collateral ~$1,700.
- Borrow again at 70% ⇒ +$490 MIM … and so on.
Each turn adds exposure but shrinks safety. A 10% collateral price drop can push looped positions into liquidation even if a non-looped position would be safe.
Borrowers must provide collateral in a smart contract, subject to liquidation by lenders or others if repayment deadlines are missed or if collateral value falls below a certain threshold.
If you want to learn more about Lending and Borrowing attacks, you can check out some of our previous audits of Lending and Borrowing Protocols: Maple Finance - Q4 2023, Maple Finance - Q2 2023, Maple Finance - 2022, Yeti Finance.
Understanding Abracadabra Money also requires familiarity with stablecoin loans in DeFi, where loans are usually over-collateralized to safeguard against market fluctuations. This means the collateral's value surpasses the loan amount. For instance, borrowing 100 DAI might require collateral worth $150 in ETH, a 150% collateralization ratio. Loans are governed by Collateralized Debt Positions (CDPs), smart contracts that ensure the collateralization ratio is maintained, with many opting for even higher ratios to mitigate liquidation risks due to market volatility.
While stablecoin loans carry liquidation risks, they offer investors the chance to leverage their digital assets for potential yield enhancement, supporting intricate trading tactics. In general, as we learn above, DeFi protocols like Curve, Yearn, and SushiSwap mint ibTKNs as part of the loan structure. Abracadabra Money leverages these ibTKNs as collateral for stablecoin loans, creating a more decentralized investment landscape. It mints the USD-pegged stablecoin, MIM, distinct for its multi-chain transferability and non-reliance on centralized digital assets as collateral.
Abracadabra Money uses innovative contracts for lending and borrowing. DegenBox handles user funds and strategies, while Cauldrons manage borrowing, solvency, and liquidation. Oracles ensure stablecoin backing. Strategies allow funds in DegenBox to earn interest. Additional contracts facilitate advanced operations like leveraging and managing Cauldron parameters. The system integrates various components for a seamless DeFi experience. For a detailed breakdown, it's best to consult the official documentation.




Attack Analysis
The attack was organized using a single ETH, which originated from Tornado Cash. In general the vulnerability lies in its shares mechanism used for debt calculation of the CauldronV4 contracts. This enabled the attacker to steal MIM tokens from the magicAPE and yvCrv3Crypto cauldrons. In the codebase, base/part represents borrow shares (the user’s share of total debt), and elastic/amount signifies borrow asset amounts. Typically, users receive borrow shares proportional to the totalBorrowAssets and totalBorrowShares ratio. However, as interest accrues, totalBorrowAssets increases without a corresponding increase in totalBorrowShares thus the proportional debt of the user grows.
Vulnerability Exploitation:
The attack started with a flashloan of MIM tokens from the platform’s DegenBox. The tokens were then deposited into BentoBox, nominating BentoBox itself as the recipient.
Then, using the borrowed funds, the attacker triggered the repayForAll function, which allowed anyone to repay the debt of others. This function incorrectly reduced totalBorrowAssets without adjusting totalBorrowShares, distorting the asset-to-share ratio.
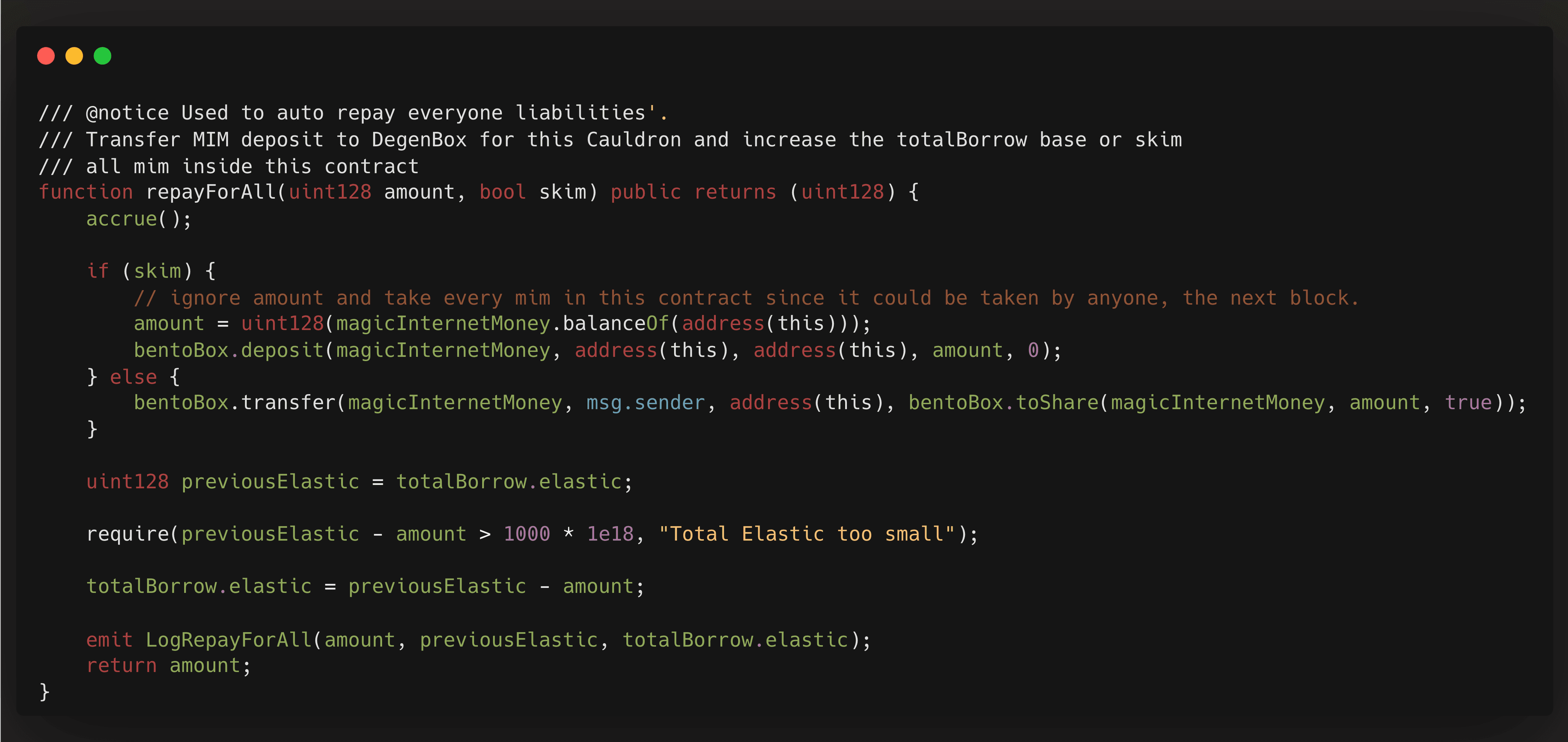

The attacker couldn't repay all of the amount as there was a check that totalBorrowAssets needed to be above a threshold of 1000 ETH. So, the attacker partially repaid the debt, manipulating the totalBorrowAssets to be greater than the threshold. As a result totalBorrowAssets:totalBorrowShares becomes approximately 1:26. In order to continue dropping the amount of assets, the attacker needed to manually repay liabilities for other borrowers.
This distortion was further exploited by repaying all but a negligible amount (100 wei) of shares for the last borrower, resulting in totalBorrowedAssets being 3 and totalBorrowShares 100.
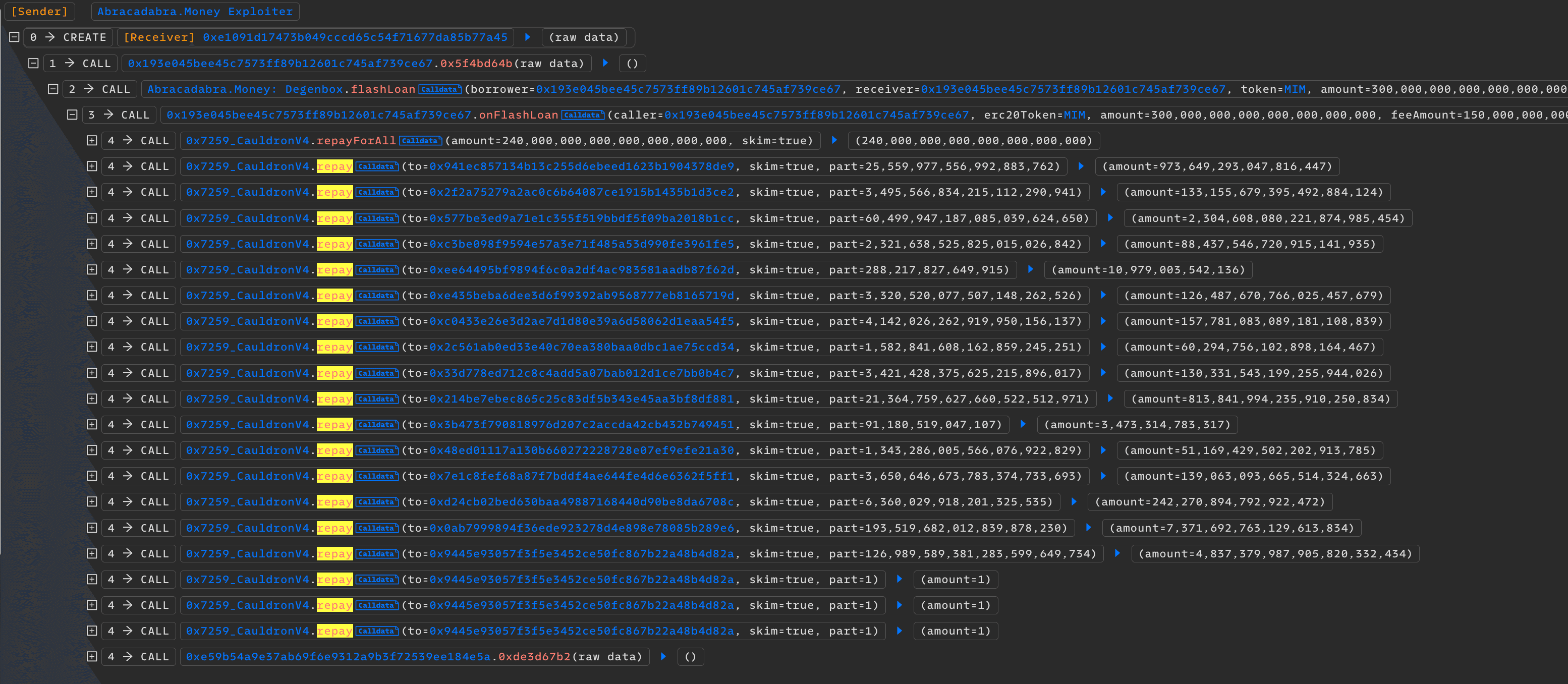
The attacker repaid 1 wei of share 3 times, which meant totalAssets reduced to 0, and totalBorrowShares were 97. Now the attacker started borrowing 1 wei from their account. At this point, totalBorrowAssets is 1, and totalBorrowShares is 98.
From then on the attacker used a tiny bit of collateral, just 100 wei, and began a cycle where they borrowed 1 wei worth of assets and then paid back 1 wei of borrow shares. Because totalBorrowShares exceeded totalBorrowAssets, borrowing 1 wei of assets resulted in the creation (minting) of a significant number of borrow shares. However, since the protocol rounds up in its favour, when the attacker repaid 1 wei of borrow share, even though it is worth near 0, the protocol makes the attacker repay 1 wei of assets.
At the end, this loop inflated totalBorrowShares exponentially without increasing totalBorrowAssets, essentially making the shares value negligible.
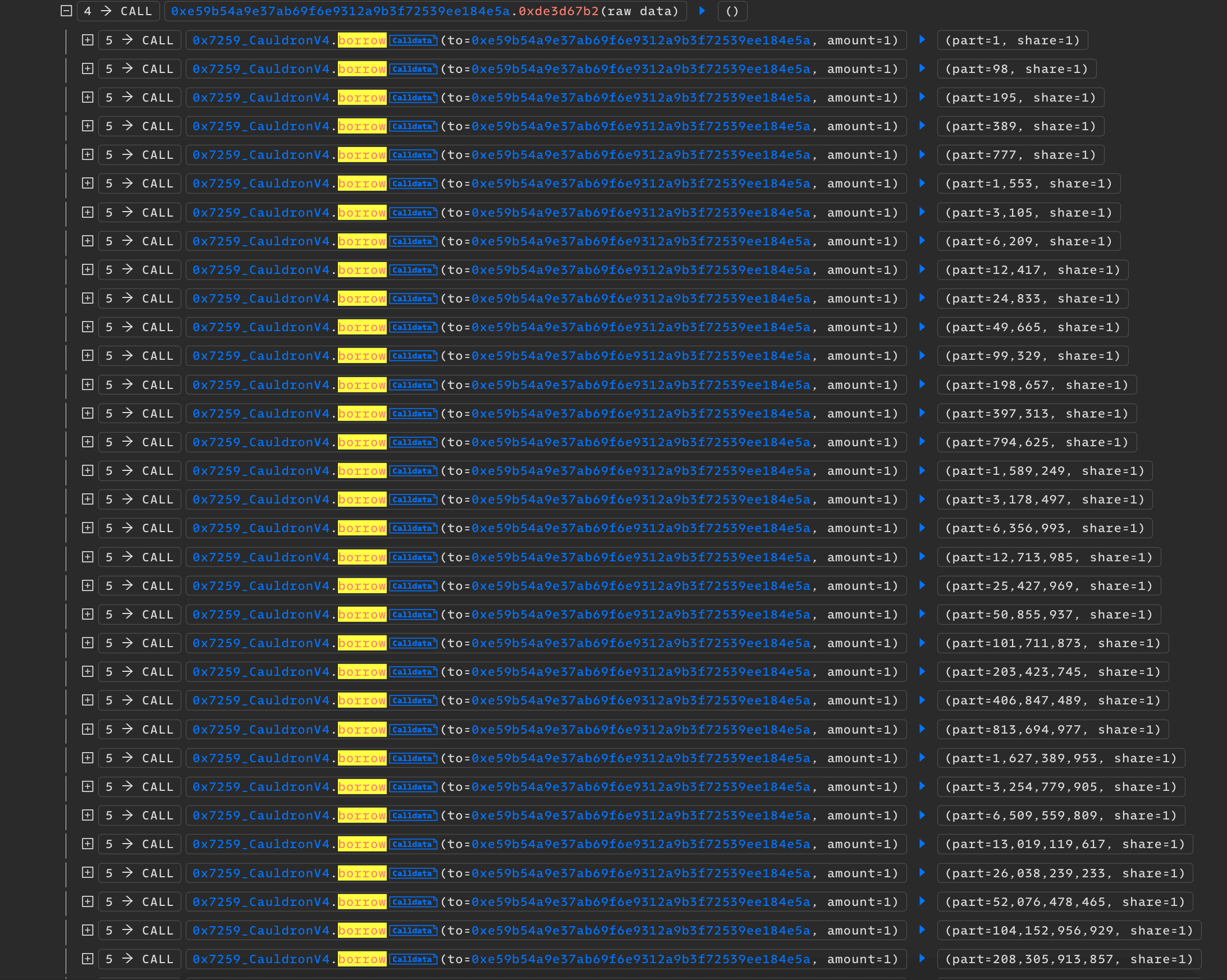
After inflating the borrow shares, the attacker set totalBorrowAssets to zero while maintaining totalBorrowShares at an inflated level. The attacker then used another account to borrow the entire funds from the protocol against minimal collateral.
The attacker fully leveraged their available funds, receiving an equivalent amount of borrow shares, maintaining a 1:1 ratio.
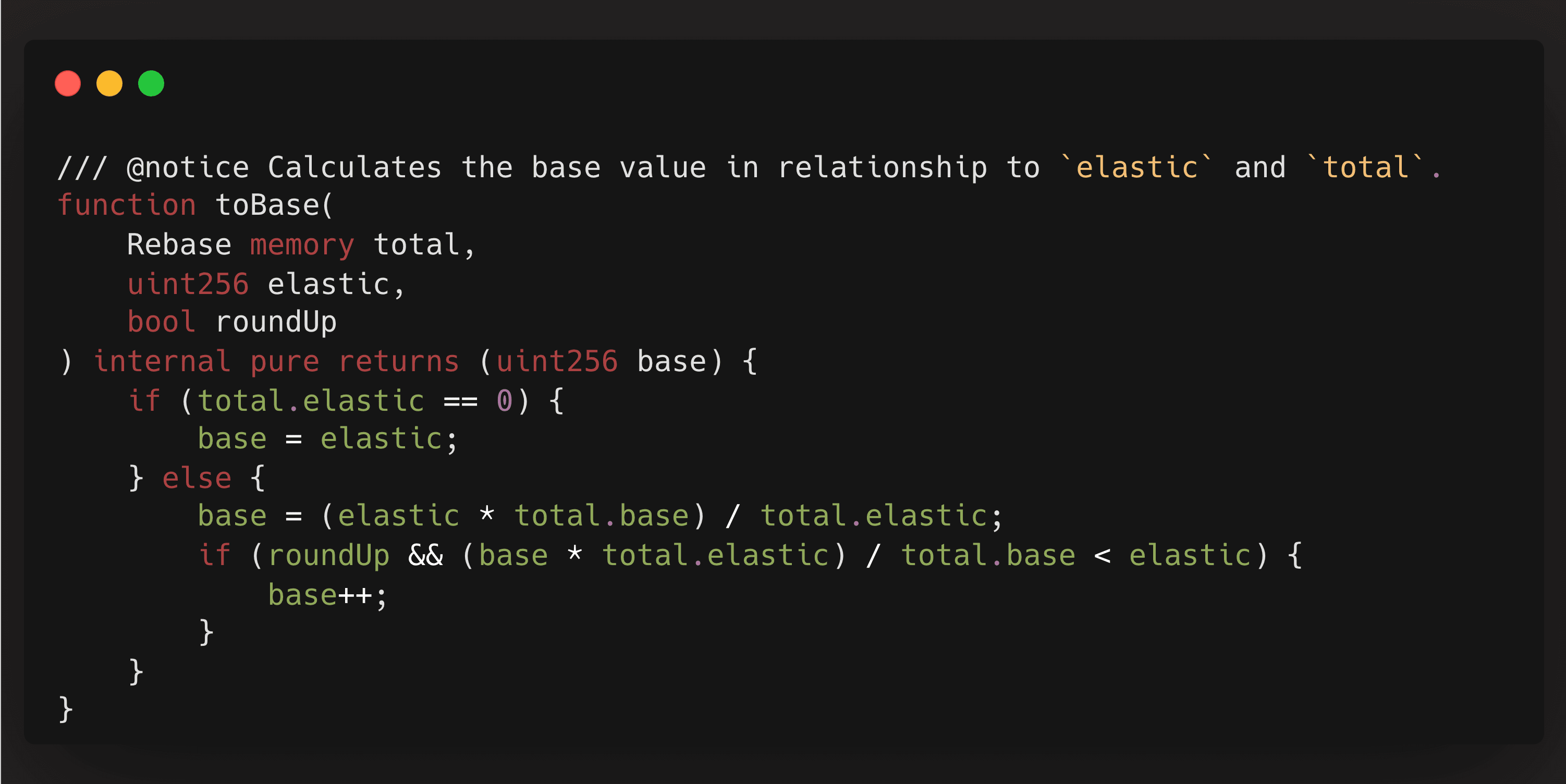
This happened because in the borrowing process, when assets are translated into borrow shares, and if the total assets borrowed amount to zero, the system generates borrow shares equal to the number of assets borrowed. Consequently, the attacker borrowed the maximum amount permissible, receiving an equivalent quantity of borrow shares.
At this point, it's crucial to note that the total borrow shares are excessively high, virtually infinite. When the system evaluates this specific account for risk, it converts the borrow shares back into the borrowed asset amount to gauge the borrowed volume.
The result is negligible, as the shares held by this account are minuscule in comparison to those held by another account involved in the scheme. The system mistakenly perceives that the latter account, with an immense number of borrow shares, has borrowed the majority of the funds, not the former. This misjudgment allows the account to pass the protocol's health check.
Attack Flow:
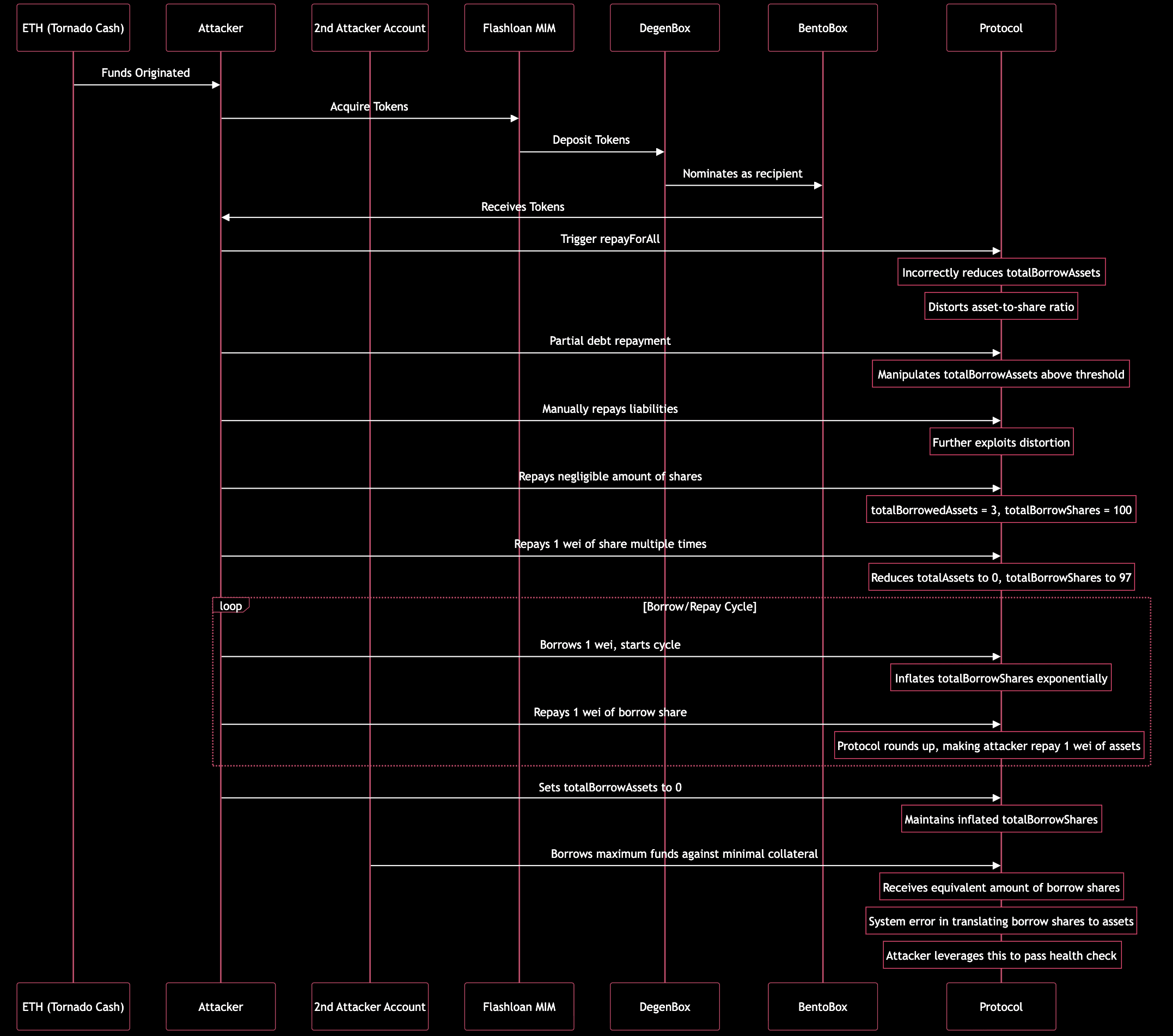
How the attack could have been prevented
For Abracadabra Money, tighter oracle medianization, sanity bounds on share accounting, and circuit-breaker caps would materially reduce the same class of risk.
To prevent similar attacks, the lending and borrowing protocols that use shares calculation to calculate owed interest, should ensure that the ratio of totalBorrowAssets to totalBorrowShares cannot be manipulated in a way that allows totalBorrowShares to be inflated while totalBorrowAssets remains low. Also, implementing more robust account health and core invariant checks, which consider potential manipulations of the shares and assets, can be useful.
Consequences
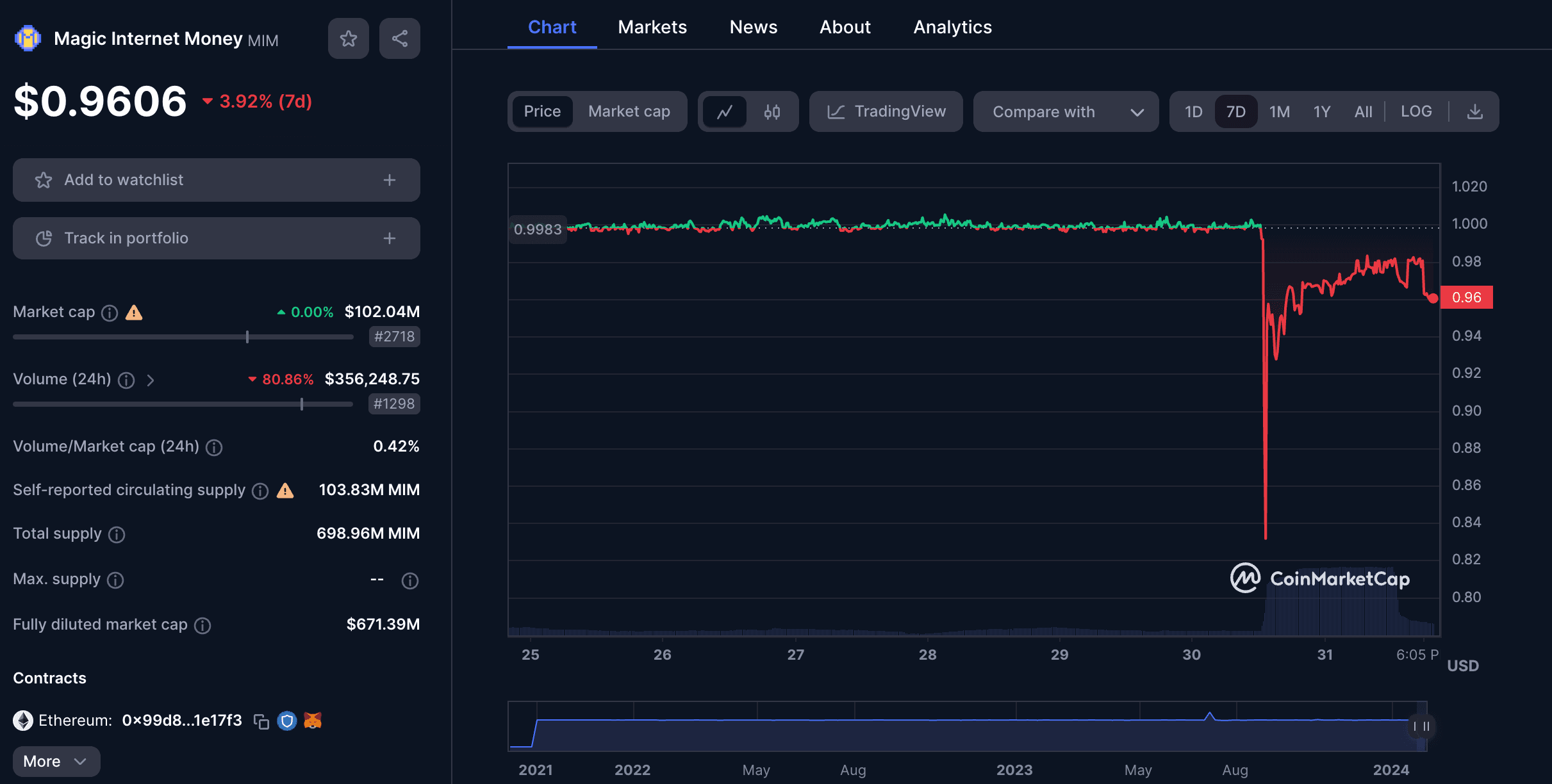
Despite the approximately $6.5 million that became bad debt, the dump of the stolen MIM for ETH led to the stablecoin losing its peg. Even though the issue had been fixed by the team just over an hour after the attack began, the protocol's team faced a tough challenge in restoring MIM's peg (currently sitting at $0.98).
An end-to-end ecosystem risk assessment can surface these systemic knock-on effects before they cascade.
Peg Impact & Liquidity Snapshot:
- Intraday low: MIM fell to $0.76 at the height of sell pressure.
- Recovery band: ~$0.96–$0.98 shortly after stabilization steps.
These figures quantify the “lost peg” beyond a single point-in-time quote and contextualize market depth and slippage in the immediate aftermath.
The Abracadabra.money Protocol Response
The abracadabra money exploit highlights how debt-share and pricing design can cascade into major losses. Strengthening oracle checks, accounting invariants, and circuit breakers reduces recurrence risk and improves resilience. Following the incident, Abracadabra Money outlined mitigation steps and design hardening priorities to prevent similar pathways from reoccurring.
After the official acknowledgment, Abracadabra Money announced their recovery from the exploit, reinforcing protocol security, by setting borrowing limits to zero for affected Cauldrons. They've contacted the attacker, offering a bug bounty and collaborating with Chainalysis for fund tracking and possible legal action. The protocol's resilience is further backed by a robust $15M DAO treasury, which will be used for buying back MIM tokens from the market and burn them. Meanwhile, operations, including their expansive product suite and liquidity provisions, continue unaffected, with future plans to introduce a Depeg Contingency Fund for enhanced DAO defenses against illicit activities.
For the full blog post, visit mirror.xyz.
The Abracadabra Money case underscores how small mismatches cascade; prioritize invariant checks and parameter guardrails before growth.
The exploit exploited logic that passed tests but failed in practice. Our Smart Contract Audit service focuses on real-world behavior, not just syntax, uncovering hidden assumptions, token edge cases, and exploit vectors that cost millions.
FAQs
What is Abracadabra Money?
Abracadabra Money is a lending protocol where users post interest-bearing tokens (ibTKNs) as collateral to borrow the MIM stablecoin; the protocol accounts debt using borrow assets vs borrow shares.
Who founded Abracadabra Money?
Abracadabra is commonly credited to Daniele Sestagalli along with co-founders including the pseudonymous Squirrel; some contributors are pseudonymous by design. The Blocktracxn.com
What caused the $6.49M exploit?
A design flaw allowed repayForAll to reduce totalBorrowAssets without reducing totalBorrowShares, corrupting the price/share ratio and enabling outsized extraction.
Which markets were impacted?
The attacker targeted the magicAPE and yvCrv3Crypto cauldrons.
How did the attacker “turn 1 ETH into millions”?
After skewing the assets:shares ratio, tiny borrows/repays minted disproportionately large borrow shares, letting the attacker borrow the vault with minimal collateral while passing health checks.
Did MIM lose its peg, and by how much?
Yes. Coverage at the time recorded an intraday low near $0.76 with recovery toward $0.96–$0.98 shortly after mitigation.
What did Abracadabra do after the attack?
They set borrow limits to zero on affected cauldrons, contacted the attacker with a bug bounty path, and coordinated with Chainalysis on tracing, alongside treasury steps.
How can protocols prevent similar bugs?
Enforce invariants so any action reducing borrow assets must reduce borrow shares proportionally; add share/price sanity bounds, circuit breakers, and health-factor checks robust to third-party repays.
Does leveraging (looping) increase risk on Abracadabra?
Yes. Looping ibTKN → MIM → more ibTKN amplifies exposure and shrinks liquidation buffer, so small price moves can liquidate faster than unlooped positions. (See your Looping section for a numeric example.)
How can Three Sigma help?
Through Solidity audits and tokenomics/economic risk reviews focused on real-world behavior, invariants, and market-level failure modes before they reach production.
Addresses
- Attack TX 1 ~$4.5M (10:14 UTC): 0x26a83d...0f7e4cf2
- Attack TX 2 ~$1.9M (10:26 UTC): 0xdb4616...79b6d877
Attacker Addresses:
- 0x87f585809ce79ae39a5fa0c7c96d0d159eb678c9
- 0x40d5ffa20fc0df6be4d9991938daa54e6919c714 (~$4.2M)
- 0xbd12d6054827ae3fc6d23b1acf47736691b52fd3 (~$2.2M)
Exploited Contracts:
- yvCrv3Crypto: 0x7259e152103756e1616A77Ae982353c3751A6a90
- magicAPE: 0x692887E8877C6Dd31593cda44c382DB5b289B684
Credits: Kankodu, EXVULSEC, Offside Labs

Software Engineer
Simão has a Master’s in aerospace engineering from Instituto Superior Técnico. Following college he took up a career in the enterprise software industry, as a fullstack developer. He joined Three Sigma with a continued passion for software development, security, coding tools and infrastructure, and an interest to learn from the exceptional talent at Three Sigma. In his free time he enjoys playing football